I am presuming we are aware of what a DoS/DDoS attack is, and DNS Based Attacks are a subset within this DoS family. DNS Amplification Attack is that notorious thug in the family that plays stealthy and pulls carpets from under people’s feet.
Why Bother?
It is not easy to block these attacks and tracing the attacker is also next to impossible thanks to the UDP (Connectionless) packets deployed.
A DNS Amplification attack can be so powerful that at its top speed, it can represent up to 20% of a country’s total internet traffic. How does it get so powerful? Let’s see.
Our Story Starts with the DNS…
DNS (Domain Naming System) is the address book of the internet. You enter a name like www.bhaifi.com and the DNS directs you to the website by matching it to its IP address (which is usually alphanumeric) like 20.512.32.66.
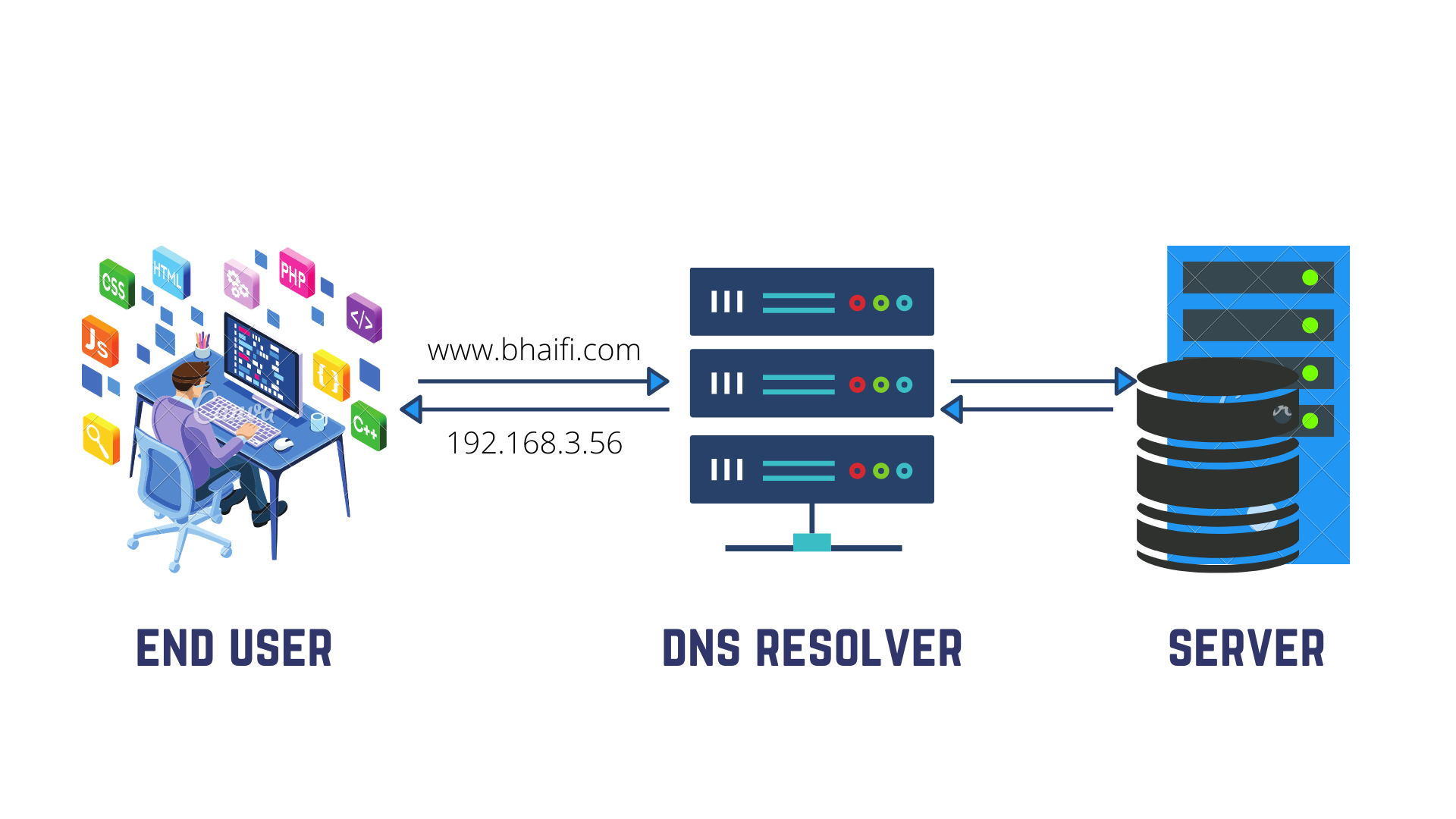
Thanks to DNS, we don't have to remember the complicated alphanumeric addresses of websites that we want to access.
Hierarchical and Decentralized, DNS is valid not just for the Internet but all networks in general, but its role in network security is a topic for another day.
But how does this DNS help in amplifying the attack?
About 90% of all cyberattacks leverage DNS directly or indirectly.
Any internet communication generally starts with a DNS resolution until after a complicated process we finally have an IP address that is actually usable by the application.
“Now this DNS is like a gunpowder keg that supplies hunters in a wilderness commune. It is needed for food, but at the same time if someone ignites it, there is a disaster!”
In this type of attack, hackers use the “replying mechanism” of the DNS to manipulate it into flooding the target system.
While usually, most trusted enterprises have dedicated resolvers with protected access, there also exist open DNS servers that are used in such attacks.
What is the DNS Reflection Attack?
DNS based attacks are volumetric in nature like their matriarch DDoS hence they too, aim to overwhelm the victim’s network by flooding it with more traffic than it can handle.
Since Hardware capable of bombarding sites with terabytes of traffic every second comes really expensive, let's use the open DNS Servers.
The DNS resolver looks up and loads websites, beginning with your device and travelling through a hierarchy of DNS resolvers across the Internet. But to do that your system sends some queries to the DNS (questions/information) and the DNS replies with the parameters needed to proceed with browsing.
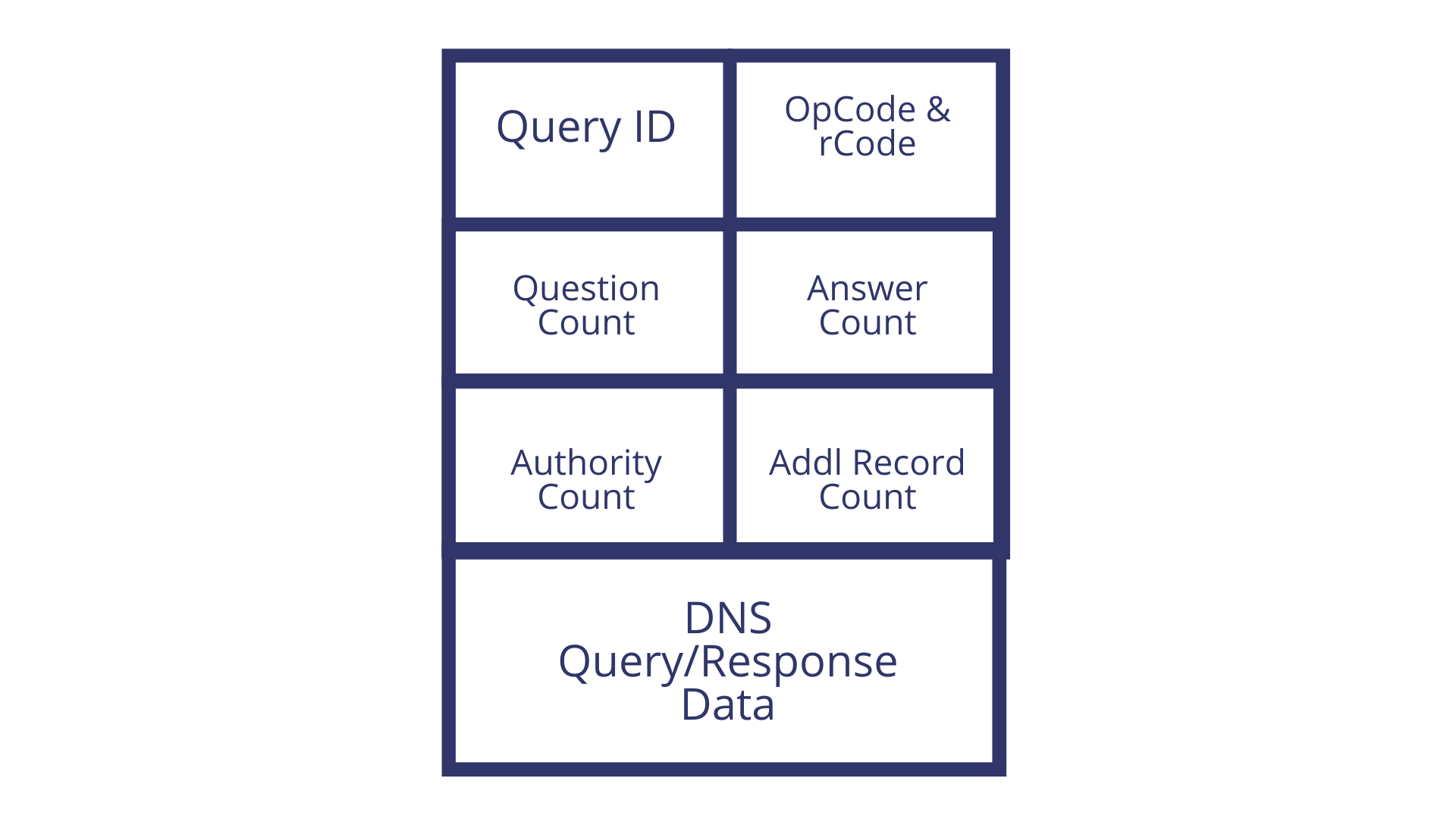
A typical DNS request packet is very small (20-30 Bytes) and returns a response that’s only slightly larger (40-50 Bytes). In its simplified form, the DNS request packet looks something like this ...
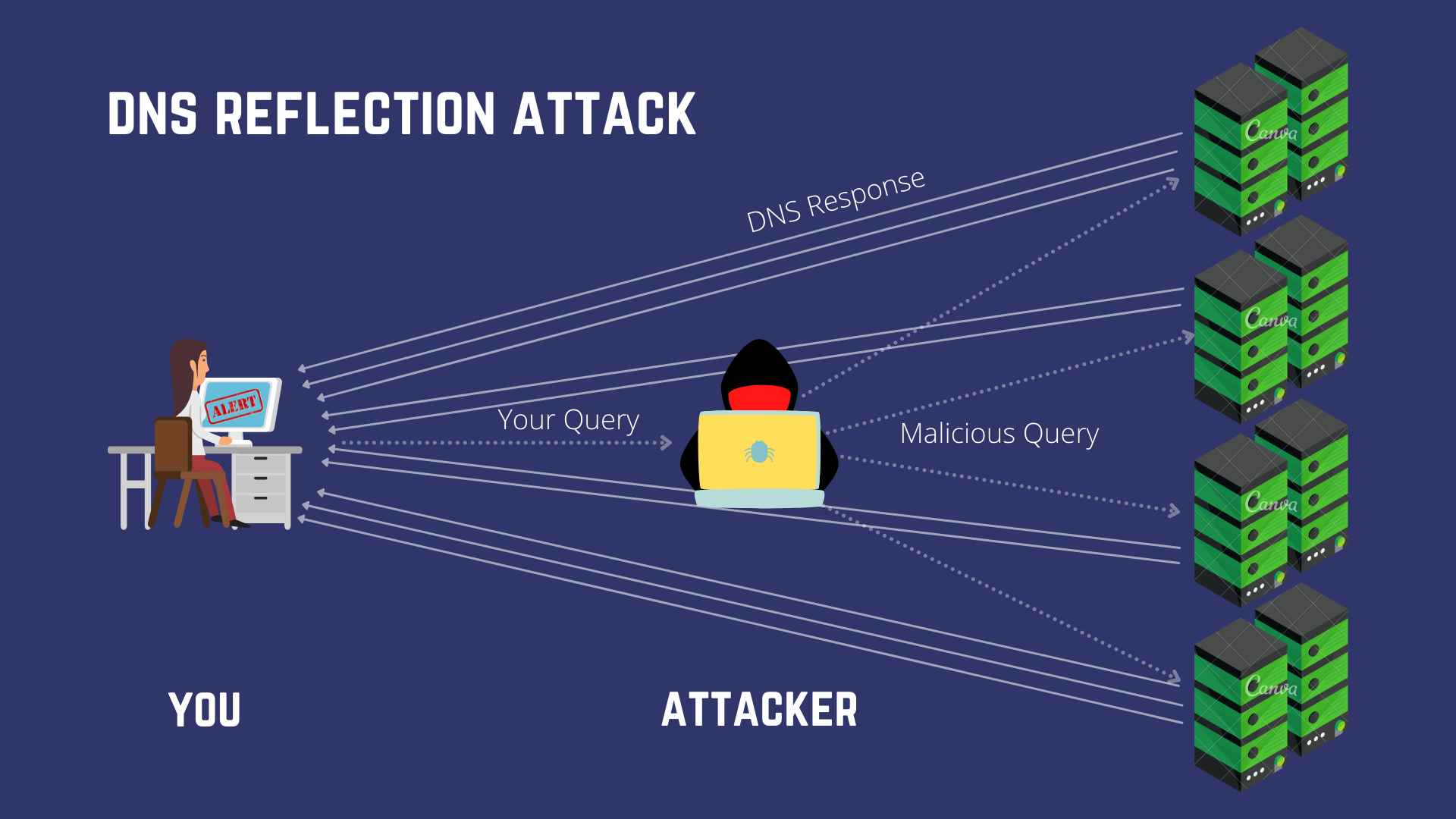
The attacker will spoof (edit) the “source address” part of his requests to the DNS Server to resemble yours (victim’s) and when the DNS replies, it will bombard your system with 40 Byte responses. Since the attack is “reflected” over a DNS Server, it is called a reflection attack.
But, there is a catch . . . .
The size of this response packet from the DNS Server is not fixed and there exist techniques that can be used to increase the response size to upwards of 300KB.
How is the size of DNS Response packets manipulated?
You can increase the size of DNS response by either ...
Requesting additional information from the server
We have already seen how a packet with default DNS information looks like, now let’s compare the same to a response. Note this field which says Answers - corresponding to the number of Qs asked by the communicating client.
Since minimal information is required to establish the connection, as discussed, the response is just slightly larger than the query.
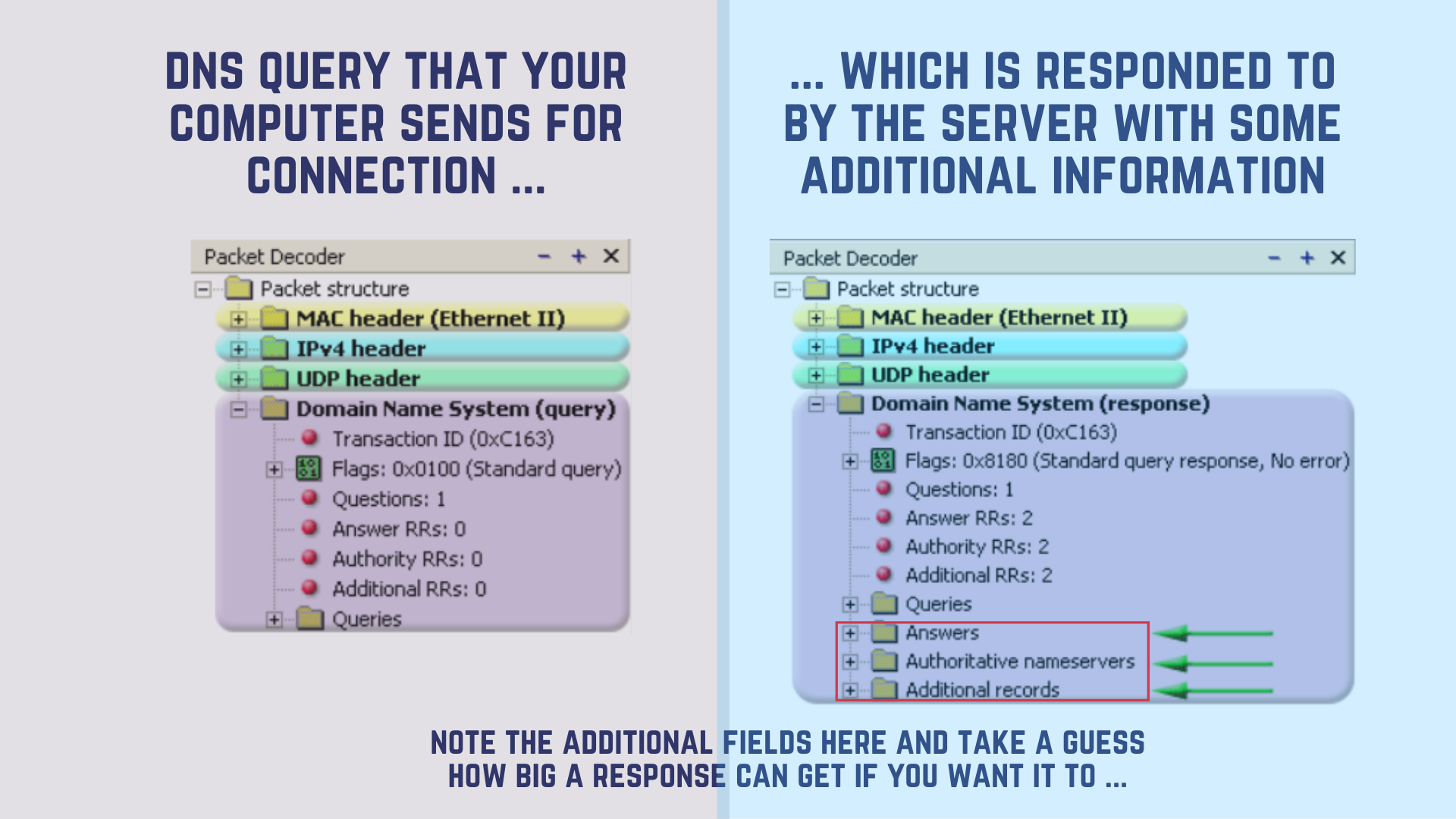
However, what do you think will happen if we ask for other UNNEEDED AND BOGUS INFORMATION? Information that is not required for communication like- Details on subdomains, system volume information, backup server information, account information, mail servers and similar additional records?
It gets returned within the DNS Question and Answer section, amplifying the size of the response packet.
Or
Using EDNS (Extended DNS) protocol extension
EDNS(0) was designed to overcome the restrictions in the size of flag fields, return codes and label types available in the basic DNS protocol that restricted many desirable features.
A 10-byte DNS request, in this case, can generate a response that’s 10, 20, even 50 times larger effectively ushering packets as large as 4000KB. Since 4000KBs can’t be transmitted at once, they get broken into fragments that are bombarded.
What is a DNS Amplification Attack?
Just like in the case of our DNS Reflection attack, here too, the hacker spoofs (edits) the “source address” of the DNS packet to resemble that of the victim, who in turn receives overwhelming responses, the size of responses here is MUCH LARGER.
It is worth mentioning here, that since these attacks are carried out via UDP (User Datagram Protocol), there is no way of determining that the “source address” is valid.
In a real scenario, these spoofed packets requesting heavy data are sent out by multiple systems (botnets) and get reflected over multiple servers. All this volume is directed at the target system or network.
How to prevent DNS attacks?
Protection against DNS attacks is tricky. You cannot block all traffic from open recursive servers since that can interfere with legitimate communication attempts. Whitelisting and strict filtering come with their own sets of issues. Still we can rely on,
- Actively monitoring the network and filtering incoming/outgoing packets. You need to make sure that your system inspects packets entering and leaving your network for indications of compromise. The firewall should be trained so as to not allow “public IP addresses originating from a private network” to leave the perimeter.
- Similarly, incoming packet traffic needs to be checked for the destination - if it is anything different from DNS resolvers handling outbound requests, these packets should immediately be dropped. BhaiFi’s proactive filtering for example uses live threat inputs to identify and block these packets.
- Setting up a network DMZ and fortifying it. If your company offers web-based services, setting up a DMZ outside of your internal network can help to a great extent. In a DMZ, the publicly accessed servers are placed outside of the firewall-protected network and then another firewall is added to protect those servers.
- As further reinforcement to the abovementioned strategy, you can place the DNS Resolver that deals with remote employees within the DMZ and local (internal) DNS Resolver inside the network. Then, configure the local DNS server to handle DNS requests from within the organization to draw a clear line.
- A network DMZ created by setting up 2 BhaiFi controllers in parallel can guarantee 99.9% safety. AI driven system ensures that the DMZ is fortified with reinforced channels, facilitating not just security within DMZ but also speeding up the entire response mechanism.
- Casting - Adding failover lines for backup. DNS Anycast can distribute the volume of DNS traffic among servers across multiple locations which in turn balances the load effectively making it difficult for hackers to overload a single server.
- Scrubbing. A good DDoS protection and mitigation (scrubbing) service can stop an attack before it hits your network by routing it through protected systems that absorb malicious traffic. It's like having those flood control dykes and wells that take in the extra water.
Parting Words
Before we part, a word of wisdom from our security experts at BhaiFi - we recommend having some form of forensic logging available (available in a limited manner with monitoring tools) for post-attack analysis and diagnosis processing. Nothing beats that in helping prepare for upcoming attacks.
Hope all that was able to help and feel free to let me know in the comments if there was something else about DNS Amplification attacks that you wanted to know and we sadly missed out.
Cheers and Happy Reading!

Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).