Malware is like a comet. Yes that extrasolar, interstellar marvel, up in the heavens. See, they both have much in common. They both become a sensation (rather a total hype) when visible (ie. when some major cyber attack takes place), are talked about for let's say 2-3 days, and plunge into darkness as soon as some time passes by.

With that digested, welcome to the second article in our series on Cybersecurity. In this piece, we will be looking at malware delivery methods or “the roads” that lead into your system, exclusively. It is assumed that you have already been through the first article and are familiar with what malware means, what its symptoms look like and how to how to protect your computer from malware. In case you haven't yet caught up I’d say you have a look here first.
Towards the epilogue, we shall be focussing on how to prevent malware attacks - leveraging technologies that can help ‘block’ those ‘roads’, keeping your system/network safe.
Compromised Files and Software
Before we look at the possible entrances malware can leverage to make it to your system, let’s get one thing clear. In most cases, the malware has to be bundled with something - a file or a software and that file or software has to make it to your PC somehow.
“Either you download it, or you are tricked into downloading it, or it was mailed by a friend, or it passed onto your system when you plugged in your brother’s External HDD - any case, the file/software has been invited by YOU! The weakest link in any system is the person at the keyboard.”
Although file-less malware attacks have been reported but they are relatively few, so it would be better if we focus on them some other time.
CASE 1:
Bundled Malware: Some programs, upon their setup, will install other software if you don't go through the installer settings in detail. For instance ‘AVG Installer’ that installs ‘Opera Browser’. These ought not necessarily be malicious, but some are. Usually you can opt-out and not install this extra software by clearing a check box during the installation. Generally, Adware Toolbars get installed like that. So make sure you read exactly what you are installing - don't just click [Next], [Next], [OK] blindly.
CASE 2:
Embedded Malware: The malware is embedded within the software and gets unleashed as the software installs. Probably the most common way of getting malware across, especially if you like to try out free/cheap variants of mainstream software from unverified publishers. Programs used to generate software keys (keygens) often install malware at the same time. In limited cases, we have also seen the malware exploit software vulnerabilities or glitches to embed itself.
CASE 3:
Installation Files: Again, there are two possibilities - either the malware was purposely placed there by the programmers, or someone exploited the security vulnerabilities in their cloud drive (from where you download stuff) to inject the malware externally. The bad thing about this is that YOU DON'T NEED TO INSTALL THE SOFTWARE TO UNLEASH THE MALWARE! All you need to do is download the setup files, and you are done!
How do you get malware on your computer?
Now this is an interesting part, since most users who are pretty casual with the media they allow on their machines are the ones who are utterly shocked when an attack takes place. Sometimes, we suffer, not due to our actions, but our inactions. Same is true about protecting your system from malware.
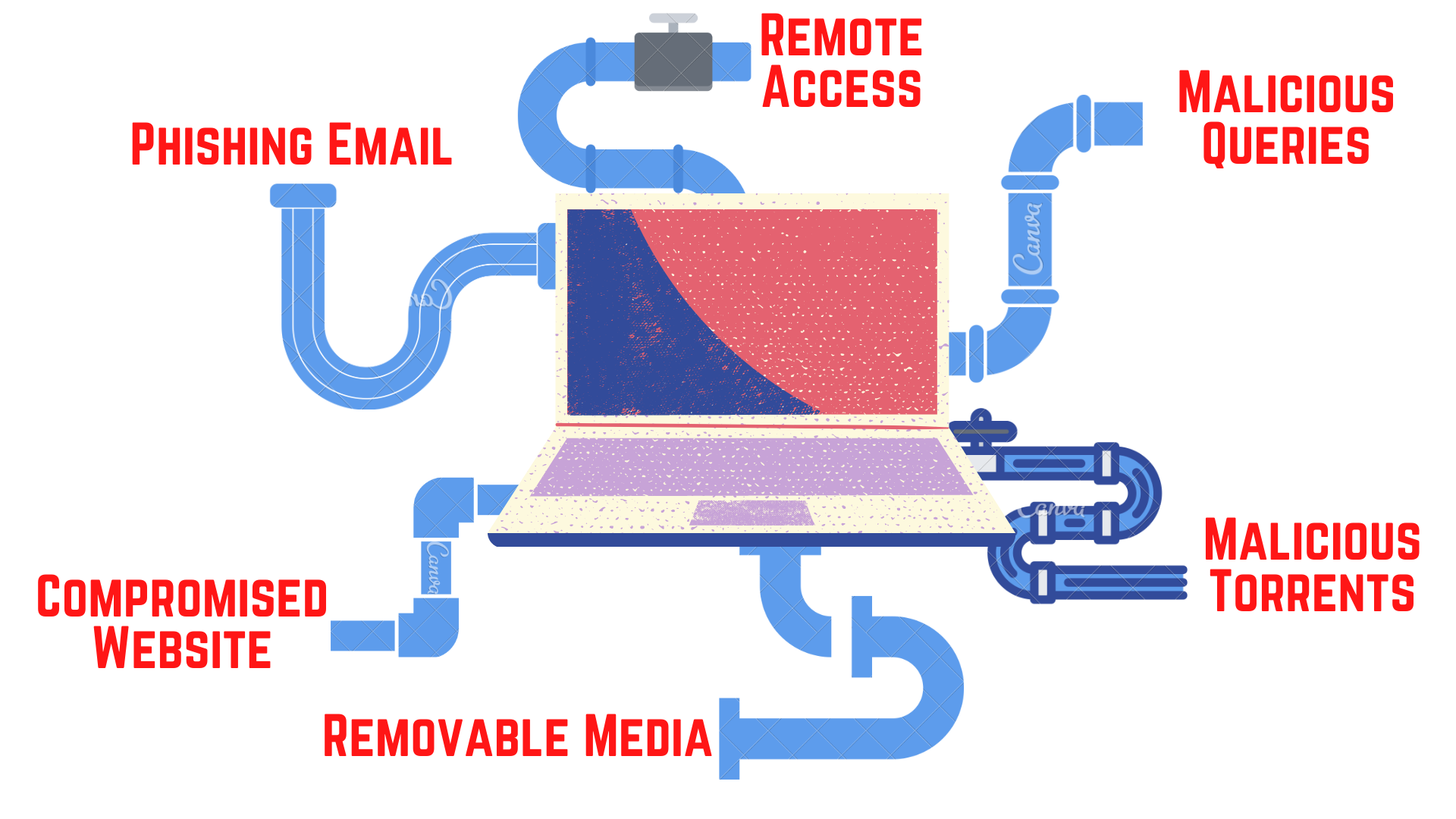
Just look at it this way, malware has to find some way around your security systems and into your machine. Let’s in fact, forget the security systems, for now, the malware just needs a path. There are multiple entry points through which malware have made it to their host machine, you can probably already recount them - External HDDs, Cloud Drives, Remote Desktops, Websites, Email, USB Drive - everything that can connect, communicate and exchange data with your machine, can serve as an entry channel for malware.
Phishing Emails
The most common method used by cybercriminals to spread ransomware, spyware, botnets and remote access trojans is via phishing emails. Yes, it has been steadily serving as a medium in a whopping 87% of the attacks resulting in serious data breaches. When it comes to phishing emails, crafting is the key! Put yourself in the shoes of the hacker and all you need to do is trick the victim into opening the attachment or clicking the malicious link.

Now, you already know that the attachment has to be an exe file and will for sure not be lured into downloading and running one. Wrong! The file can come in any format - pdf, zip, doc, xls or js. As soon as you run the malicious pdf, known vulnerabilities in your pdf reader will be exploited and the malware, hidden as an image file within that stylish calligraphy font, will make its way in to take down your computer while you fiddle with the reader. Mind you if you don’t have a pdf reader, you do have a browser that has an inbuilt pdf engine. Which of the two is scarier?
In a second case, the same can be done using a word file by baiting you into “enabling macros” when viewing the document. This enables the hacker to run a script that downloads and executes a malicious exe file.
Remote Access
The Remote Desktop Protocol was designed to allow IT administrators and support technicians to securely access your machine remotely, for configuration, upkeep or troubleshooting.
As you can already guess, this is 'just the' opportunity for anybody with criminal intent. If you are by any chance running over port 3389, you need to make sure you have a robust cybersecurity framework with active cyber threat intelligence in place. Hackers can leverage the port range and status to look your machine up on search engines like Mojeek, Shodan and Dogpile and gain access by brute-forcing the password to log in as an administrator.
How to avoid that? Don't turn on Remote Access unless extremely necessary. If you do, make sure you do that on a secured network or use VPN to mitigate the cybersecurity risk. Changing the default port is also a good idea and so is enabling two-factor authentication for remote sessions and extending it to network-level for any new machines that appear.
Visiting a Compromised Website (Scripts and Overlays)
After all the news that pops up day in and day out, and having read this article till here, I’m sure you won’t make the mistake of purposely visiting a malicious/suspicious website. So, how would the poor hacker live? I'll tell you, he's gonna “drive-by”. Drive-by(s) are another entry path that attackers use to deliver malware. These are malicious downloads that trigger without your knowledge, in the background, when you simply “visit” a compromised website.
Cybercriminals initiate drive-by downloads by deploying “overlays”. Overlays are similar-looking interfaces (say an overlay that looks like Facebook) that redirect you from the real Facebook to the site controlled by the hacker. An overlay attack exploits known vulnerabilities in the software of legitimate websites - in this case, some back end vulnerability in Facebook.
In a code injection attack, also known as cross-site scripting or XSS, these site vulnerabilities are exploited to embed the malicious code (aka exploit kits) on a website. Exploit kits allow the hacker to silently scan the visiting devices for weakness, and, if found, execute code in the background without the victim being required to click anywhere. Mostly notorious for delivering ransomware attacks, XSS has been carried out against some of the most popular websites in the world like NYT, BBC and Cooltoad, with billions worth of daily traffic.
Malicious Queries Trap
This is a relatively new, and hence extremely dangerous method of getting malware across to your system. It has its basis in the idea that “your information is everywhere.” The search engines, the websites you visit, their social media crawlers, all know who you are and what you are looking for. All this information is auctioned at dark web marketspaces where hackers gain access to it.
To carry out this attack, the hacker generates a bogus website optimized with your search query to bring you to snare. For example, I know that you are looking for Photoshop and I also know that you don't want the legal one. So I will automatically generate a link to feed your query - "photoshop free" in this case and bring you to my site where you can download the Adobe Photoshop for free. It's a zip file, you download it, you take the bait.
Another example- there are certain utilities like an offline installation bundle for MS DirectX. Now the catch is, MS DirectX gets automatically installed as part of your windows OS update. People who run cracked or pirated versions of Windows cannot update it online and have to rely on downloading the update files. While there are some genuine uploaders who collect these update files, bundle them together and provide you with the archive, there are many others who have malicious intent.
Removable Media Attack - USB Drive, External HDD
Ah! The old school creepypasta! Last, but not the least, let's have a look at where this all began. The good old days of CDs, DVDs and Floppies!
How is this pulled off? The removable media device is left (dropped) by hackers at places where they can be found and picked up. In case of a mass 2016 attack in Australia, the pen drives were mailed to victims as promotional Netflix applications. Now, even if you are a good person, it is simply natural for you to plug it into your system and check out the content.
A very interesting attack, launched mostly via USB drives is called HID (Human Interface Device) Spoofing. The flash drive will trick your computer into thinking that a USB keyboard is attached and inject keystrokes to command the computer into providing remote access to the cybercriminal after your security framework has been disabled. The notorious Spora Ransomware leveraged this functionality to spread around.
Malicious Torrent Websites
Even against the popular view, I am not against the use of torrents. Although I am against piracy but my point is torrents provide an excellent method of sharing files, conserving both the per capita bandwidth and data utilized as compared to traditional upload/download methodologies.
Nevertheless, compromised torrent websites are as dangerous as they sound. To initiate the seeding and leaching process (downloading a file via torrent), you have to first download the torrent file and then run it using your torrent client, probably Utorrent. In several cases these torrent files are placed inside archives for extra security. This is where the criminals play their game, they place their malware inside the archive which enters your computer when you unzip the files to run your torrent. Mind you, your security scanners cannot detect a malware while it is inside the archive, it can only be detected once the files have been unzipped.
Preventing Malware Infection - Intrusion Detection System (IDS) & Intrusion Prevention System (IPS)
Although we have already discussed how to deal with malware in our previous article, along with some best personal cybersecurity practices, the idea this time is about preventing malware altogether. That brings us to the concepts of intrusion detection and intrusion prevention which form the backbone of what we call a firewall. Keeping it simple, Firewall is the gate that leads to your system/network, while IDS and IPS are men who stand guard.
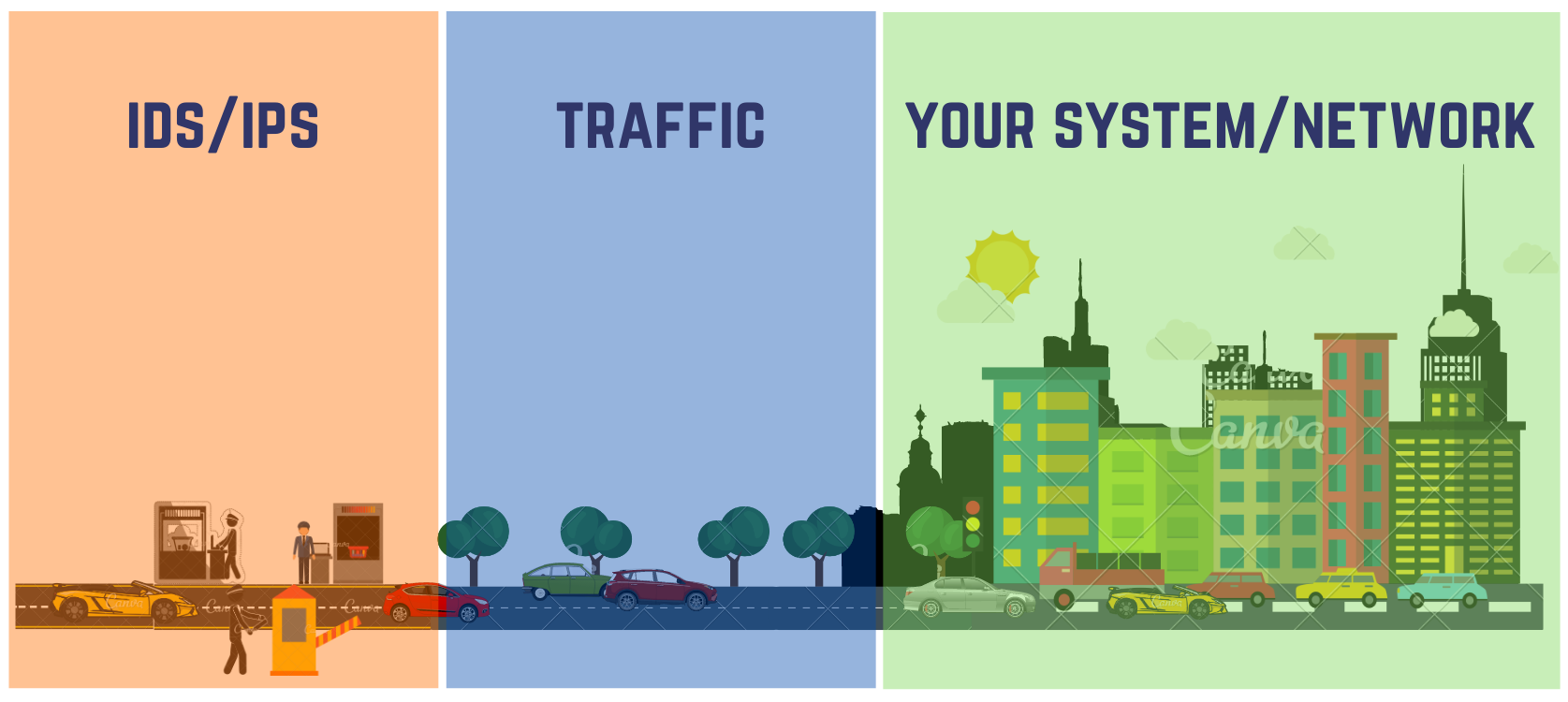
An Intrusion Detection System (IDS) constantly monitors and analyzes incoming network traffic for signals that exhibit malicious intent and an Intrusion Prevention System (IPS) goes a step ahead to proactively deny/allow network traffic based on the predefined security profile. If a data packet represents a known threat, it is blocked, otherwise allowed. This brings us to a very important part- the limitations. Since the IDS and IPS need a database (known as a threat database) to compare known threats in order to block them, it leaves them vulnerable to previously undetected threats. Also, they are powerless against internally present malicious files.
Nowadays, software-defined networking has allowed enough flexibility for solutions to bypass these traditional vulnerabilities by leveraging and hybridizing hardware and software capabilities of firewalls and systems into a unified threat management system. Solutions like BhaiFi are changing the art of computer virus prevention by smartly monitoring, maintaining and securing networks to great productive effects.
Summing Up
So that's all folks! For now. That sums up the major highways that lead to your system, rather, the major highways that carry most of the malicious traffic. It is worth noting here that ever-evolving cybercrime industry has opened up many sideways, alleyways and tunnels too, but we shall look at them some other time. The scope of article series “Cybersecurity and You” is to acquaint you with the concepts of malware, their symptoms, their attacks and prevention. The purpose is to make you cyber aware of the risks that loom within the air currents of your room. You might want to have a look here for some endpoint security measures (personal measures) that you can take to ensure the safety of your machine. Endpoint security, bundled with prevention at source and your own cyber awareness makes up your unbreachable comprehensive all-round protection.
Do let me know in the comments of any thoughts that cross your mind and don’t forget to sign up to our email newsletter to catch up more cool tech stuff related to cybersecurity.
Cheers and Happy Reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).