Starting with what port scanning is - It is simply the process of sending packets to specific ports on a host network to determine which ports are open to sending/receiving data.
An analysis of these ports on your network can help you identify vulnerabilities which is why most IT personnel carry it out routinely.
In order to conduct this scan, you will first have to conduct a network scan. Make a list of active hosts and map them to their IP addresses.
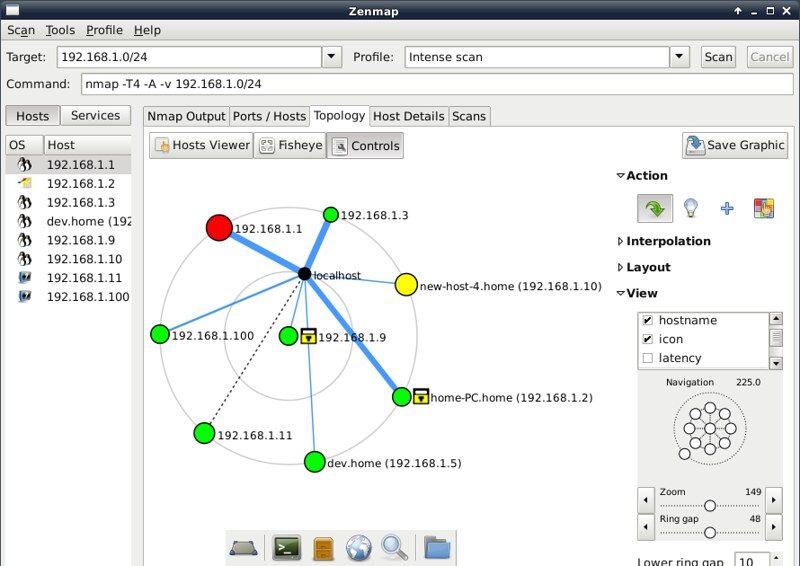
When a cybercriminal conducts a port scan of your network, he/she is looking for vulnerabilities that can be exploited to gain access to your network.
Why Bother?
After completing a successful scan, the hacker is able to get his hands on valuable information critical to the safety of your network, such as
- Nature of your business
- Nature of your networking operations (reveals a lot)
- Dynamics of data inside your network
- The operating systems you use
- The Firewall/Routerguard Model and version
- Network Consistency Table status
- Status of all connected infrastructure
- Critical information about everything else connected to your network
What is a port?
Well, a port is a harbour - where the freighter picks up our goods, travels across the ocean - only to arrive at another port. In computer networks too, a port is a place where the data that is to be sent or received is parked. If your computer is a house (identifiable by home address), then ports are your gates.
In order to make life easy for techies, each port is denoted by a port number. (Port Number + IP Address) form the combi that can be used to pinpoint your device on the network.
Port numbers range from 0 to 65,536 where 0 to 1023 are used for communication/special purposes, 1024 to 49151 are registered ports and 49,151 to 65,536 can be used by nearly everyone, playing a role in exploits.
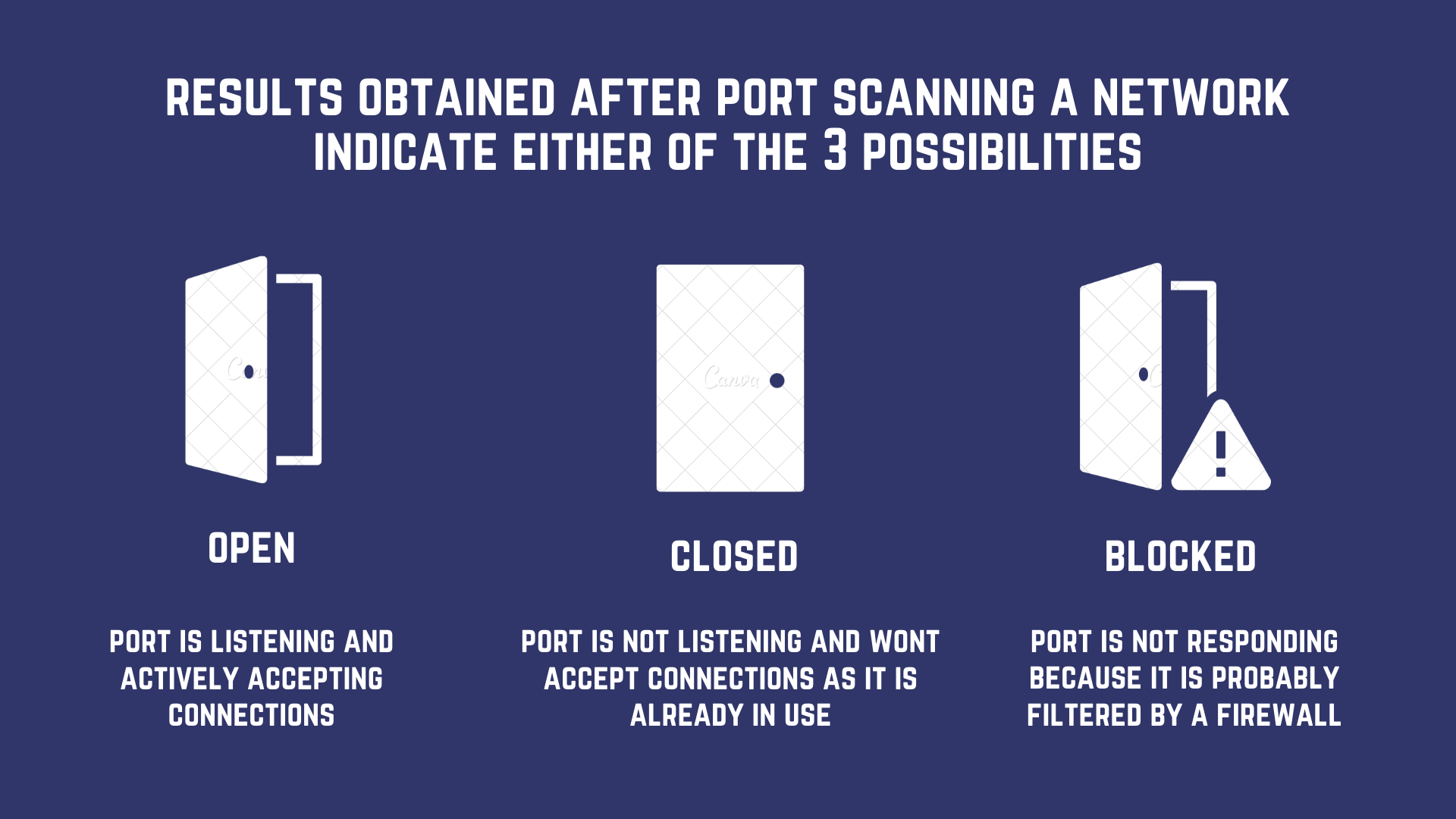
How do we scan this port or network? Whatever?
There are a bunch of Port Scanning Techniques around, each with its own set of pros, cons and use cases. To start off, of course, you need the host list first which is obtained by conducting network scans.
Network Scanning allows you to determine all active devices on your network by sending a ping to each device on the network and awaiting a response.
Once this initial step has been completed, you are all ready to scan the ports - types and techniques of which are as follows.
Ping Scan
Ping Scan sends an ICMP echo request to the target (or across the whole network, if the target hasn’t been identified) to check if it is open. If the response is an ICMP reply, it means the port is open if there is no response, it means there is a firewall guarding the network.
TCP Half Open
This relatively commonly used port scan sends a packet with the SYN flag set and waits for the SYN-ACK from the target. Unlike a regular full TCP connection, the sender does not reply with an SYN-ACK response packet, since the SYN-ACK received is enough to determine the state of the port. This makes the entire process extremely fast - you can scan 1000s of ports every second.
TCP Connect
This is essentially the same as the half-open scan above but instead, we finish the handshake process and establish a connection by sending the final ACK packet. This is a much slower means of port scanning as it takes more packets to finish.
Response analysis for both these TCP based techniques is similar;
Successful handshake = open port,
RST (reset) packet = target is alive but the port is closed,
No response = target is alive but the port is filtered.
UDP
UDP scans work by sending a packet, which is usually empty. These scans are slow, and UDP is directionless - you can never be sure if the packet got to its target in the first place.
Response analysis is a little trickier here;
ICMP unreachable error = port is closed.
ICMP unreachable error + other error codes = port is filtered.
No response = port is open/filtered. Here, you need the “version enumeration” to determine if there is a firewall blocking communication.
Advanced Scanning Techniques – NULL, FIN, X-MAS
These types of scans are also known as “stealth scans” because here we are trying to induce a response from the target without going through the handshaking process.
They are impactful as the techniques required are fairly simple and they cannot be traced by most logging tools - only high-end firewalls and BhaiFi Time Machine can trace them.
What makes them different from TCP Half Open? The way the packets are crafted- most of these packets like the ones used in FIN and NULL type stealth scans - shouldn't even exist.
Well, I cannot explain their functioning here, do let us know in the comments; we’d be more than happy to discuss the same in an upcoming article.
How to do a basic open port scan on Windows?
The Windows operating system comes loaded with this command-line utility called netstat.exe that can be used to determine open ports on a particular host. (Yes this cannot scan the whole network).
To view which ports are listening (open) on a local host type the following command in prompt:
netstat –an ¦find /i “listening”
The results will be displayed across 4 columns – the protocol type, local IP address and associated port number, foreign IP address, and state.
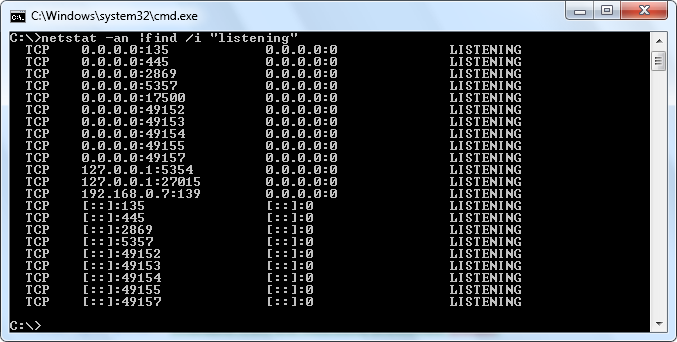
You want to look at the 2nd column (local IP address with associated port number), the state of which can be affirmed from the 4th column.
What is a Port Scanning Attack?
Port scanning almost always precedes any major cyberattack. It is the most popular recon tactic used by hackers when looking for vulnerable servers.
This problem becomes all the more acute because, as discussed, there are scanning techniques that do not appear in security logs. To cover tracks better, attackers also use “decoy traffic” to perform port scans without revealing any network address to the target.
Attackers probe networks and systems to analyze how each port will react — whether it’s open, closed, or filtered and what is the nature of security.
Once complete the hackers use the open ports to deploy their malware. It is an excellent method of pumping malware directly into a network. The hacker can easily save the time they would have otherwise wasted on social engineering the infection.
Usually, the malware of choice is a CNC (command and control) malware capable of lateral movement within the network like a RAT (Remote Access Trojan).
Once safely inside the network, the malware causes disruption, steals data, mines cryptocurrency, locks down your data for ransom - depending upon how good or bad your stars have aligned on that particular day.
Malware is just one part of the story. Open ports can also be used to conduct denial of service attacks like DoS and DDoS.
How to Defend Against Malicious Port Scanning?
Most effective ways of detecting and avoiding Malicious Port scanning requires comprehensive security measures with up-to-date threat intelligence because protocols and security tools are evolving daily.
- IPS (Intrusion Detection and Prevention System) is specifically designed to address the control related issues with respect to open ports.
- They can be availed separately as well as parts of higher end firewall systems.
- Packet filtering firewalls can also detect a port scan in progress and shut it down, but require the proper policy implementations.
- More autonomous solutions like next gen firewalls can go a step further and detect even the dummy traffic used by hackers as a decoy, keeping you a step ahead.
- Using Wrapping: TCP wrapper allows you to control access to the servers based on IP addresses or domain names, especially effective on Linux and BSD.
- Plugging the holes: Conduct your own port scan to determine if there are more ports open than required.
- Check your system to determine existing weak points that could be exploited and take measures to prevent the same.
- Threat intelligence: Plays the most important role here. If intrusion is detected, ports should be shut ( by disconnecting remote access, shared drives etc) and active measures should be taken to reboot in safe mode.
- Remember, port scans only precede a major attack.
- Take measures to ensure that operating systems and firmware stay up to date with latest security definitions. More often than not it is the vulnerability associated with the old system that gets compromised.
Parting Words
That was all about that, with some minor alterations that are always there. Isn't it kinda funny how 3 states of a port can be used to determine so many things about your network and machines? I feel so.
Hope this was able to help you get better acquainted and hence better prepared against the threat. Anything you believe we missed, or is not clear, fire a question right there in the comments below and don't forget to sign up for our weekly newsletter to stay a step ahead of cybercriminals, always.
Cheers and Happy Reading!

Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).