“We will bankrupt ourselves in the vain search for absolute security.”
- Gen. Dwight D. Eisenhower (Allied Commander of the European Theater, WW2)
Same is especially true when talking about cybersecurity. Absolute cybersecurity being an absolute myth, what we want to do is keep ourselves ‘relatively safe’. Simply making sure you are the quickest in your herd will not just dissuade the predators into pursuing you, but also make them look for easier targets as you are not worth the effort. That said, article 3 of our series “Cybersecurity and you”, welcomes the seekers to the summary of do(s) and don't(s) of personal cybersecurity.
Having covered the malware, their symptoms and how they spread, along with common prevention and remedial, today, we shall be juicing those articles into a list of dos and don'ts for easier comprehension and adoption. However, it is still highly recommended you go through article 1 and article 2 first, for greater understanding. Structurally, let’s take the reverse approach here - first let's look at Don’t(s) or passive cybersecurity techniques. You can augment your personal cybersecurity by 3X simply by making sure you DON’T make any of the cyber mistakes we are about to discuss. After that, we shall move on to what you should definitely “DO” for a boost of another 5X mitigating considerable risks to your data security and augmenting it eight times over! Let’s go!
Make sure you,

Make the Silly Mistakes:
What could be the silliest mistake when it comes to cybersecurity? Entertaining phishing mails? Not having an antivirus? Nope! Silly mistake include -
- Leaving your system unlocked when you leave your desk, or
- Writing down your passwords on a sticky note. (Seriously, memorize them or use some password management software like Dashlane or Nordpass, but don't note them anywhere! - it's like keeping all your keys together at one place), or
- Not setting up an unlock code/pin for your laptop/smartphone, or
- Assuming that it won't happen to you. (A very persistent cyber threat!)
Gist is: Don't make these basic mistakes.
Click without thinking:
Don't think twice before clicking - think thrice! Remember, one wrong click can cost you big time. Malicious links can do damage in several different ways and with each passing hour, cybercriminals are innovating new techniques to disguise and hide them - in images, documents, songs, everywhere! So make sure you inspect links and ensure they come from trusted sources before clicking.
“When hackers can’t find a security vulnerability, they’ll attack in other ways.”
This type of attack, also known as social engineering, is used to target the ‘mind’ of the user, rather than the ‘device’. Especially with the information publicly available online and over social media, there is a mad scramble among cybercriminals for creative ways to dupe users, making social engineering the most innovative form of cyberattacks.
Especially if it's a phishing mail:
Perfect and most common example of Social Engineering, phishing emails are responsible for more than 44% of the total attacks and more remarkably, 90% of total "successful" attacks. The standards and lethality of these attacks have improved at least tenfold since the last impression of the one you have in mind. Primarily designed to deliver the killing blow via a Ransomware, their content is fine-tuned with all the little details designed by accomplished content developers to dupe you into taking the bait.
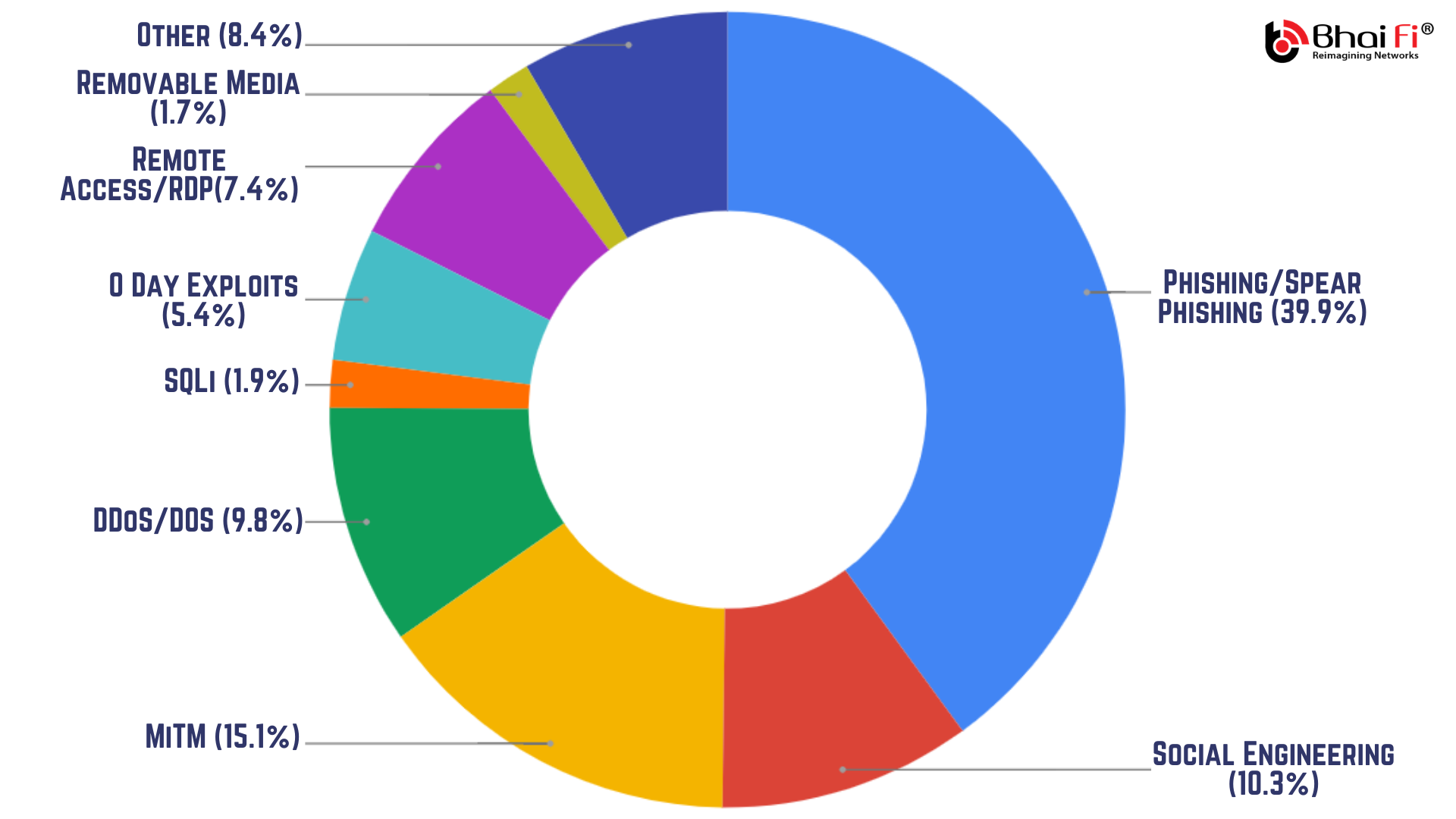
“As you can see, in most of the cases, what we do is, we invite the shady man with a knife into our house and cry foul when somebody gets hurt.”
Overstretch your digital footprint:
In the new “always-on” world of social media synchronizing via smartphones, you should be very cautious about the information you include online. Your socio digital footprint is used by cybercriminals to choose and track their targets. It is highly recommended that you only show the very minimum about yourself on social media. Consider reviewing your privacy settings across all your social media accounts, particularly Facebook. Adding your detailed home address, birth date, or any other similar identifiable information will dramatically increase your risk of a security breach.
Use outdated OS and device security:
Make sure you update your operating system whenever a new stable release is available. A general rule of thumb, the longer a software has been out in the market, the more time cybercriminals have had to mine data, reverse engineer it or exploit its vulnerabilities to serve their purpose. While keeping the software up to date is the best-case scenario, you can still strike a balance here. Most of the time MS tries to push unstable (beta) versions that not just do more harm than good, but act as primary breeding grounds for 0 day exploit attacks. Generally speaking, you can go without updates for about a month or two in case of Windows - just make it a habit to read the changelog - what new features the update carries and do you really need them or not. Don’t say no if it's an important structural or security update, rest of the time, well wait for the next big stable release, features will be included in that anyway!
Visit Compromised Websites:
Do we even need to talk about this? You pretty much know the risks. You visit a compromised website, and that is more than enough to bring your machine to ruin. Malware can download in the background (without your clicking anywhere) and latch onto your browser by installing themselves as javascript (again without your having to click anywhere). Usually the compromised websites are red-flagged by your browser as you try to make your way there and are completely blocked by browser integrations that come with free antivirus software.
Depend too much on single-layered defenses:
A strong password is difficult to crack, but it can still be cracked with sheer brute force and if what lies ahead is unrestricted access to your system, you are doomed. If you work in a shared workspace or a coworking space, it is advisable to use multiple layers of security. Folder locks, Application locks and Drive Locks are good places to start- at least for critical data and applications. Then there are the ‘two factor/multi-factor’ authentications that can help boost your online privacy and security further by adding additional layers of security. More on them later.
Keep unnecessary data:
It's a good personal cybersecurity practice to keep shredding your obsolete data from time to time. Files, Contacts and other sensitive personal or business-related information that you do not need anymore but could compromise your digital well being, should they fall into the wrong hands. Even from a cybersecurity management point of view the lesser data you have, the easier it is to secure and organize it. In case of an unfortunate attack, it becomes easier for your security system to locate and target the malware, as they have to scan lesser data. Also, older untouched files have a chance of getting corrupted much easily as compared to their newer counterparts. Get the picture?
Make sure you:

Keep at least a Free Antivirus:
Antiviruses, even if free, can deal with most malware that makes it to your system better than the Windows Defender. Additionally, most of them come equipped with a browser extension that blocks access when you try to visit a compromised website. These extensions are also capable of blocking malicious javascript from installing onto your browser. Although free variants of antiviruses provide basic security, you can avail better features if you go for their paid variants. Avira, Kaspersky Free, Malwarebytes, Avast! and Bitdefender are some excellent free antiviruses that don't hog your system resources.
Although, if you want to keep using Windows Defender:
You can, but you need to make sure you are extra careful. For starters, don't use the dark web (use only if you know and trust the sites), don't visit websites that offer freeware from unverified publishers (It is worth mentioning here that a ton load of Malware today are capable of generating fake verification licenses and are able to trick the Windows Defender into believing they are legit), turn all sharing off when using a public network, take regular backups, keep creating system restore points every month or so and always keep you recovery image ready in a Pendrive. Windows Defender should advertise something like - Increase your cyber awareness within 10 days! Just kidding and moving on:
Get a free firewall:
Like ZoneAlarm, Comodo or LifeLock to add another extra layer of protection. Firewalls work differently as compared to Antiviruses, for the fact that they secure the entry points leading to your machine, rather than scanning files. Firewalls provide real-time intrusion prevention - keep them up to date and they are going to make sure no threat gets past your gates. Usually, paid variants of mainstream antiviruses like Norton, Kaspersky and Malwarebytes come equipped with a software firewall.
Keep a malware removal utility handy:
Although most free antiviruses and windows defender is able to neutralize the malware, they cannot reverse its effect. The crap that it has already spread around your system. The settings, the registry values, group policy, memory allocations- etc- a long list of stuff malware can contaminate. To reverse these effects you need either a system recovery image in Pendrive, a recent system restore point or a malicious removal utility like Microsoft Malicious Removal Tool (MRT) or Virus Effect Remover (VER). That brings us to the next point:
Schedule system restore points:
To be set after every fixed period of time or so. They are especially effective in reversing malicious effects as they can be used to roll back the changes made to your system settings until a certain time of day (your last restore point). To create a system restore point, go to
- [Control Panel] -> [Recovery].
- 3rd option from top says [Configure System Restore].
- You click that, and a [System Properties] pop up menu opens up
- Navigate to the [System Protection] tab there and this is where you wanted to be.
- To create a system restore point right away, click on [Create] and to schedule or configure a restore point, click [Configure].
Worth mentioning, System Restore points are created at ‘partition’ (virtual drive) levels and you need to have the protection turned [On] for a drive to run it. Also, it is not necessary for you to cover all partitions, simply protecting the C: drive to create restore points is good enough, since that is the partition that usually houses your operating system.
Sad news? Multiple Ransomware have been reported to have deleted the system restore points soon after having gained control.
Use a strong and different password on every single occasion:
I know what you are thinking! There are just too many passwords for a lone soul to manage - at least 10 that belong to your non-essential (social media and online gaming accounts). This makes reusing the same strong password on multiple sites a tempting thing to do, but that is where the entire strength of the password is compromised. Either, jot your passwords down on a piece of paper you intend to keep really safe, or go for a password manager like DashLane, NordPass or LastPass that can help you to maintain strong unique passwords for all of your accounts. These programs can generate strong passwords for you, enter credentials automatically, and remind you to update your passwords periodically.
Use Multifactor Authentication:
While it is good to have a strong password, it's even more imperative to have two-factor, or multi-factor, authentication. This method provides two layers of security measures so if a hacker can accurately guess your password, there is still an additional security measure in place to ensure that your account is not breached. For example, as soon as you sign in to your account protected by multifactor authentication, the website will try to confirm your entry with a code sent to your registered mobile number. If you don't produce the code, you cannot enter. However, this means you further need to:
Make sure your smartphone is secure:
It’s important to get into the habit of securing your presence through your mobile device as well. Use strong passwords, patterns, pins and biometric features, keep your Bluetooth off, don’t automatically connect to any public WiFi, and download apps from outside of Google Play Store. Securing your android device deserves a whole article for itself.
Keep Your Recovery options handy:
If worst comes to pass, always keep system recovery options ready. Although Microsoft has finally come up with a “factory reset” option with an option that allows you to save your data, I would recommend that only in case of corruption caused by factors other than malware, because the system reset resets your windows to default settings but the malware can still survive in your files.
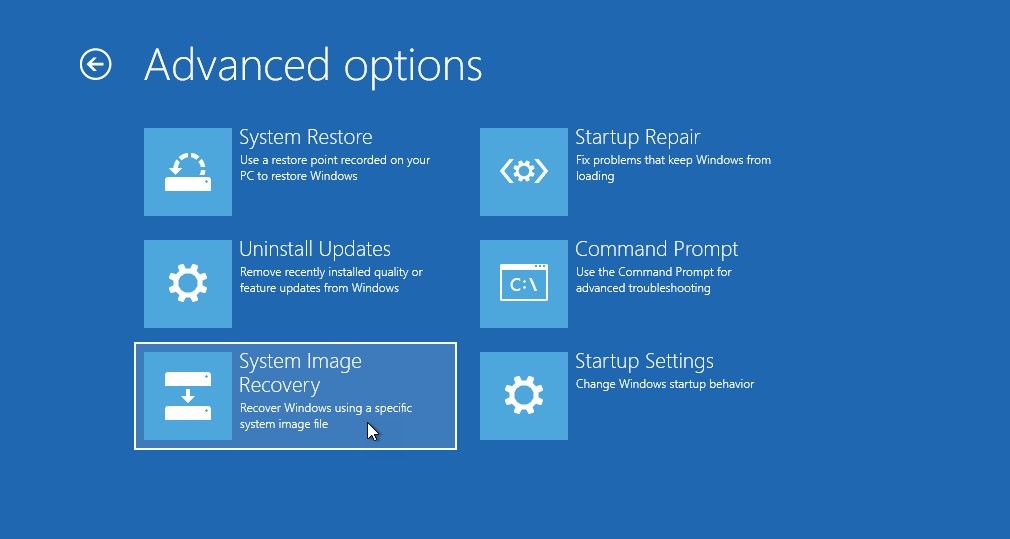
The most recommended thing to do is to save your system image as a backup on a recovery media like pen drive and go for a ‘clean installation’ of Windows. The system image recovery can reinstall the Windows environment and allows you to restore your saved settings, installed applications and other related data. To set up a system image for recovery, click on [Start] and go to [Settings].
- Select the [Backup] option and click on [Add a drive].
- In the drop-down menu that appears, choose your Pendrive (in which you plan to set up the system restore).
- A wizard opens up, and will inform you regarding the space that is required for creating the system image. You will need somewhere close to 50GB, therefore a 64GB Pendrive is recommended.
- Once the recovery image has been created, you can launch the recovery environment by holding down the [Shift] key as your system boots up.
- [System Restore], [System Image Recovery] and [Automatic Repair] can all be accessed from this recovery environment menu.
Connect only to private/secured networks or use a VPN:
You might be tempted to connect your device to an unsecured connection, but when you weigh the consequences, it’s not worth it. Connect only to private networks, especially when handling sensitive information, or make sure you are running a VPN. A Virtual Private Network connects your machine to the destination device or server securely, mitigating the possibility of attacks. Psiphon, Nord VPN, Photon VPN are some excellent software that secure your connection.
Classify and Organize your Data:
Keep high-level Protected Data (e.g., SSN's, credit card information, important academic, social and personal records, health information, etc.) off of your workstation, laptop, or mobile devices. Make a habit of creating a repository (password protected folder) on a password protected HardDisk and depositing all your sensitive information there. Securely remove (shred, don't delete) sensitive data files from your system when they are no longer needed. If at some time you have to transmit that sensitive data, make sure that happens via a secured channel- encrypted path.
Conclusion
With that final point marked, we arrive at the end of our time together. We looked at some critical personal cybersecurity tips that help you mitigate threats to data security and keep you off the cybercriminal limits. Although, if you belong to a non-technical non-cybersec background, there is little you can do to prevent a cyberattack on your own, if the hackers are after you on tenterhooks, yet conclusively enough, the biggest threat to cybersecurity is your lack of awareness.
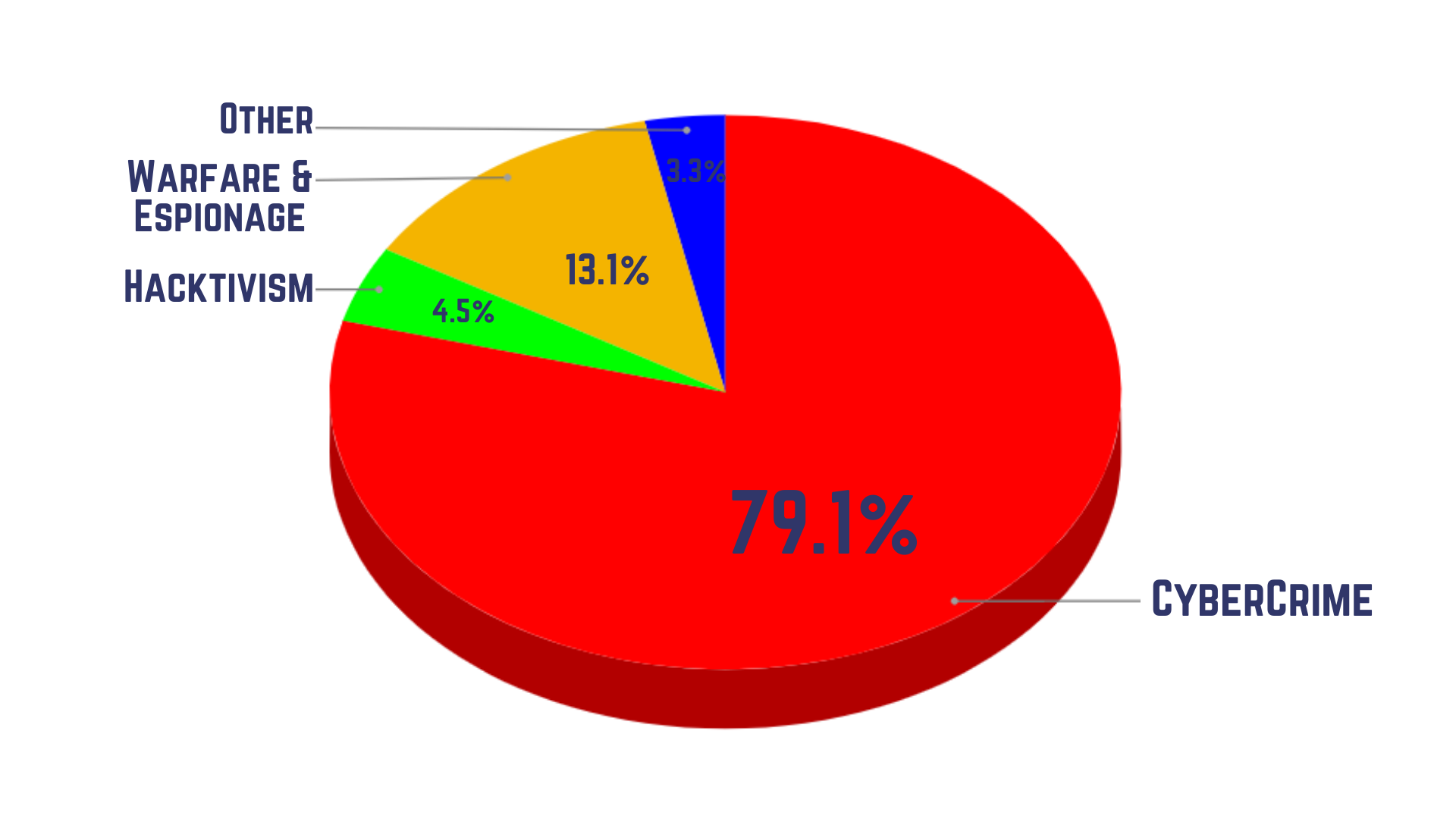
The other good news is, hackers won't be after you on tenterhooks unless you are someone very very important (like James Bond), - as you can see, cyberwarfare and hacktivism (a term used to define hacking with the intention of whistleblowing) constitute a bare 14%. These are targeted and usually sophisticated attacks, resistance against which calls for comprehensive cybersecurity measures like BhaiFi. On the personal level, if you follow these tips properly, you can augment your data security and online privacy enough to dissuade any potential threat.
Do let us know in the comments below if we have missed on anything and don’t forget to subscribe to our email newsletter for more cool cybersecurity stuff.
Cheers and Happy Reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).