It is not uncommon for businesses to lose critical client information, trade secrets and intellectual property to their rivals. When we try and deduce these cases, we realize that the organization at the receiving end has been a victim of a targeted cyber attack.

Why Bother?
Targeted Attacks are Specialized - The malware that wrecked your enterprise was specifically designed to target your network. They knew your strengths and weaknesses.
Recovering from them is another story - You can be sure that the hackers have been following you around the internet for a while. They probably know a lot about you including how much money you can cough up closing any window for a bargain.
Moreso, as of now, a staggering 85% of organizations have reportedly been hit with spear phishing, the lethality, as well as convincingness of the same, has gone up dramatically.
Talking of the whole picture, targeted attacks which used to form 41% of all attacks back in 2010, amount to 69% of all attacks today.
So what is a Targeted Attack?
A targeted include could be any, or a collection of different cyberattacks like- Ransomware, 0-day exploit, data exfiltration, spear phishing, DDoS executed against your network after a long drawn strategy.
Since you have been in the attackers’ crosshairs for quite some time now, they have had ample time to evaluate your defences, adapt to any measures you recently took and improvise their attacks.
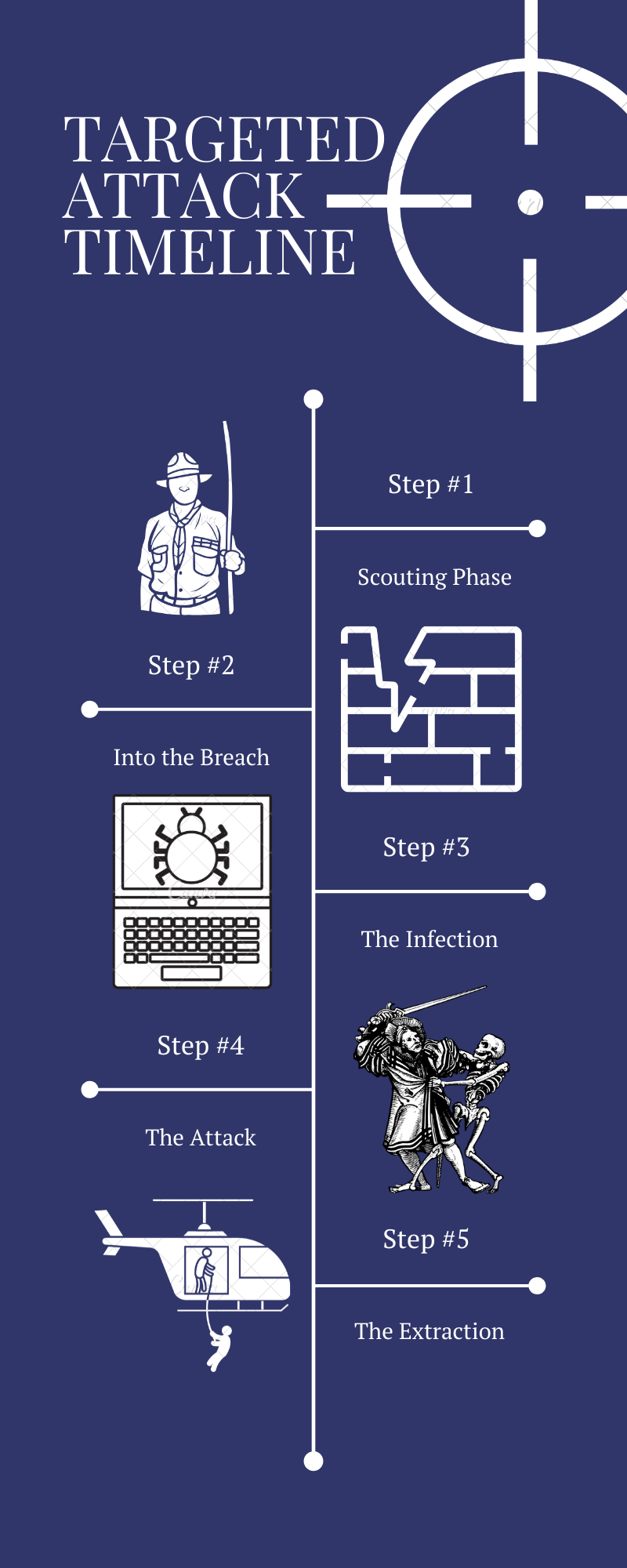
A better way of understanding these attacks is by breaking them down into steps depending upon what activity is taking place.
Steps that make up a targeted attack.
Step #1: Scouting Phase
The aim of hackers in this phase is to gather as much information about you as possible to tailor their attacks. The cybercriminals zero in on you by following your digital footsteps around the internet and by rigging your network with their port scanners. This phase is barely noticeable.
Step #2: Into the breach
The hackers have acquired the necessary information needed to launch an attack. Attacks like spear phishing, malicious queries (water holing), 0-day and other bundle exploits aimed at delivering the malware (mostly RATs- Remote Access Trojans) to your network are carried out in this phase.
Step #3: Infection Phase
Having made it safely inside your network, the malware will now move laterally to scan your network, infect more devices, data storages and execute malicious routines. Hackers use the CNC (Command and Control) protocol to get the RATs into attack positions.
Step #4: The Attack
The malware starts isolating the important data and preparing it for extraction. Files are either copied or moved (depending on the customization) to hidden directories, ready to be picked up. At the same time, the malware also updates your network drive tables and registry values to avoid radar.
Step #5: Extraction Phase
The isolated and prepared data is then transferred by the RATs which can also adapt to your packet sizes and harness ports to make the file transfer look legit. Extraction of data can be quick or gradual with the latter being very hard to detect thanks to their low bandwidth consumption.
Even after the purpose of the attack has been achieved, the hackers can leave behind a dormant RAT to facilitate another round of attack sometime in future.
Targeted Attack vs Others
In an untargeted attack, the hackers don't have a specific target in mind, hence, they target as many devices, services or users as possible.
A Phishing Email that is fired randomly and reads “Dear Customer” is an example of an untargeted attack.
In a targeted attack, your organization has been singled out well in advance because the hacker has a specific interest in your business.
The groundwork for the attack could have taken months so rest assured the cybercriminals had already discovered the best route to deliver their exploit directly to your systems.
A Spear Phishing Email that addresses you by your name is an example of a targeted attack.
Most Common Types of Targeted Attacks
Social engineering
Social engineering attempts to manipulate your psychology by exploiting trust. Social engineers will leverage your poor understanding of technology and inability to understand the attack patterns to play their card. Social engineering is a predominant component of targeted attacks because it helps in critical when what, where and how planning.
Spear Phishing
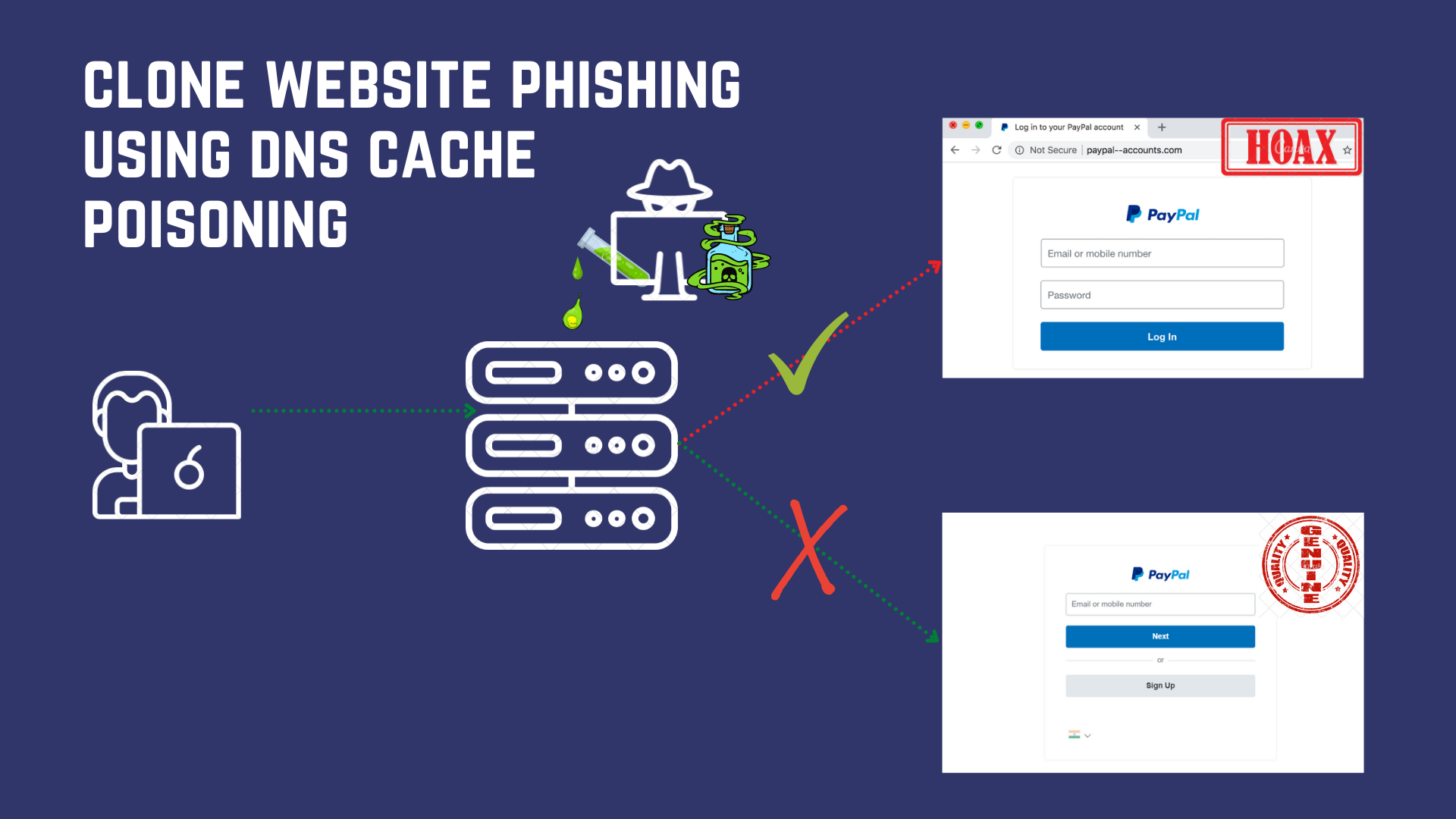
Spear Phishing involves sending malware/malicious link bearing emails to specific, well-researched targets. If phishing is like wading across the water with a net, spear phishing is like using the spear to pick the big fat fish. A spear-phishing mail will never be unrelatable - exactly why you need to be extra careful.
DDoS
A Volumetric attack conducted against a specific organization’s internal network or website aims to flood the target with bogus queries to overwhelm its capabilities and “deny” service to legitimate users/customers.
Ransomware
Most Ransomware are a targeted attack since it is useless wasting malware on people with low-value data or empty pockets, sufficient background research is carried out before firing the ransomware. Once it has infected the system/network, the ransomware will encrypt all data and hold it for ransom. Pay the price if you want to see your data again.
A successful targeted ransomware attack against a company can easily stop its business processes for days, making owners more likely to pay up.
CryptoJacking
Is an attack where the RATs are used to take over your network and its components, but unlike Ransomware primarily aimed at encryption and exfiltration, Cryptojacks tend to harness your computing power to mine bitcoin for the attacker.
Waterholing
A variant of a drive-by download attack, in targeted waterholing, the attacker will use your stolen data to predict which websites you are likely to visit next and lay a trap there. Attack derives its name from the waterhole used by hunters to lure animals.
Protecting against Targeted Attacks
Now well, since the targeted attack is not even defined in cybersecurity, there is no “as-such” dedicated protection against the same. There are tools to deal with ransomware, RATs, worms or sweepers, but by the time they are noticeable, the attack is almost through.
One thing you can do is minimize your social signature as much as possible. Of course, it cannot be reduced to 0 and there are data breaches from trusted sources, but let's start with checking the unnecessary trumpets first.
“Securing the network comprehensively is the only reasonable chance we have at preventing Targeted Attacks."
- Dr Leroy NW
Stopping targeted attacks requires a sophisticated approach to security that integrates multiple layers of defence with up-to-the-minute threat intelligence. IDS/IPS (Intrusion Detection/Prevention Systems) are packet filtering modules that prevent malicious traffic from plying on your network.
Properly Configured and Maintained Firewalls or AI-Driven Automated Networking Solutions like BhaiFi deal with targeted attacks by mitigating them at different steps.
For example, if your malware somehow makes it beyond step 2, it still will not be able to spread and infect the network because of extensive checks and measures. In the case of BhaiFi, the existence of network antivirus makes things worse for the malware by actively tracing and eliminating it.
I would have otherwise directed to our list of cybersecurity best practices that minimize attacks, you could still have a walk there, but honestly, they aren't too good against targeted attacks.
Parting Words
And that was all about Targeted attacks, how they are carried out and what all you can do to keep your network protected.
Once again there is this assumption that we were able to help you know all you wanted to, about these attacks, and if it is not true, do feel more than free to let us know in the comments.
Cheers and Happy Reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).