Starting off with what this CryptoJacking attack is - it is an innovative cyberattack - one of the few where the injected malware is NOT after your important data.
The Cryptojack DOESN’T even want to cause disruption, in fact, it wants your system/network to function at its best!
Seriously!
All this crypto mining malware wants to do is harness your processing power to mine cryptocurrency for the hacker who planted it on your machine/network.
The method of spreading a cryptojack (threat vector) is nearly the same as that of any other malware - from a malicious link in an email or an infected download file/application to auto executing javascript.
Why Bother?
Though limited in number as compared to other mainstream cyberattacks, cryptojacking is slowly picking up pace with a 200% increase in the number of attacks since 2017.
The sophistication of attacks has gone up too with emerging cryptojacks steadily targeting android smartphones in addition to PCs and laptops.
The main attraction for the hackers seems to be the low-risk high payoff factor. Worst that can happen - you will detect and remove the cryptojack - the hacker will then innovate and make his malware stealthier.
What culminates to all this - we’ll look at that but let's see the whole picture first.
What is Cryptocurrency?
For a better understanding of cryptomining malware, we need to first know what cryptocurrency is and how it works.
Cryptocurrencies are encrypted digital currencies created as an alternative to traditional money that exists only in soft copy and the money is protected with cryptography - an encryption technique that makes it nearly impossible to counterfeit or double spend.
The “Coins” of cryptocurrency are basically entries in a decentralized database - a distributed ledger maintained by a network of individual computers.
Now if you use your computer (basically its processing power) to verify transactions on this ledger, you will receive some “coins” in return and this process is called mining.

How does your processing power help?
Special administrative computers collect data from the latest cryptocurrency transactions every 10 minutes and turn them into a mathematical puzzle.
Now, to verify this particular transaction, you have to solve the puzzle it has been converted into. ‘Solving’ this puzzle is exactly what we call ‘mining’.
The miner who solves the puzzle receives some amount of cryptocoin as a reward.
“However, with an increase in the number of miners, the complexity of the puzzle calculations has also augmented over time and today even high-end machines cannot mine profitably enough to cover the costs involved.”
For instance, A bitcoin mining farm can cost up to $80K every month in electricity bills.
Enter CryptoJacking - The way around these bills?
Just asking - what time would it have taken for a criminal mind to come across the idea of “stealing” this “processing power”? Well because that is what this cryptojacking is all about.
Instead of paying for an expensive mining computer, hackers infect a large number of regular computers with ‘cryptojack’ (a Remote Access Trojan based malware) to create a botnet (network of bots or zombie computers).
The malware allows the hacker to control this entire botnet and harness the processing powers of individual systems to mine bitcoin. Since the malware doesn’t have any symptoms, users end up believing their system has slowed down due to age.
How does Cryptojacking Work?
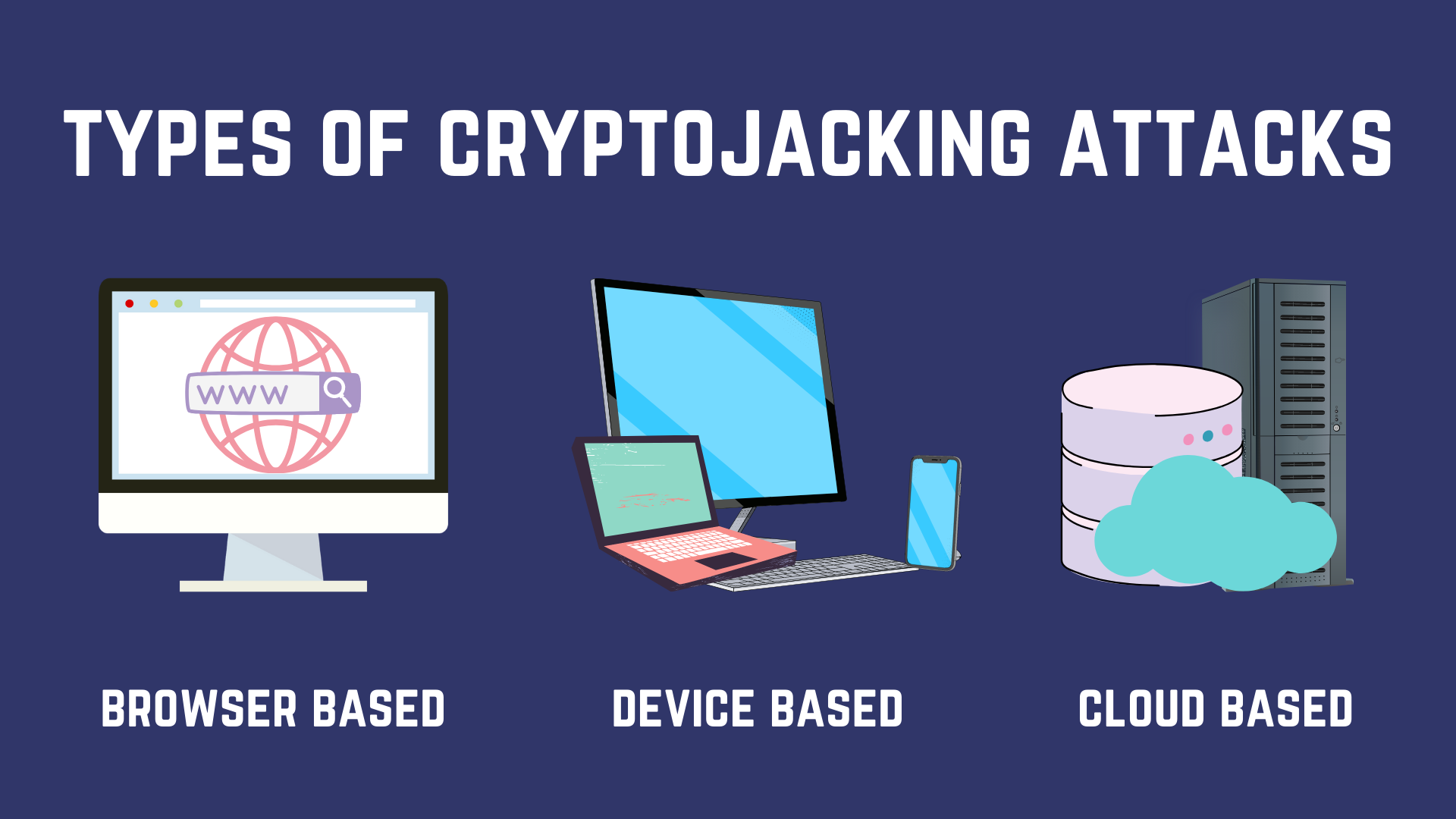
Cryptojacking is of 3 main types based on how hackers get hold of your machine. They either
Infect System
Hackers trick the victims into loading crypto mining code onto their machines, through carefully crafted, genuinely convincing phishing emails. Once you click on the link in the mail, a code runs that installs the cryptojack.
Infect Browser
Hackers inject a script on a website/ad/applet that is delivered to multiple websites. Once victims visit the website script automatically executes and the malware infects their browser.
It is important to mark that since no code is stored on the victims’ computer, most anti-malware programs cannot detect it.
Infect Network
Also known as ‘cloud based’ cryptojacking, this is a targeted attack where the hackers probe the network, exfiltrate API keys and consequently gain access to your cloud drive. Once there they siphon off CPU resources for cryptomining.
Far more profitable as compared to the browser or system based cryptojacking as the gain in computational power is significant.
More often than not, hackers usually use a combination of both - browser and system based cryptojacking to maximize returns. Again, since infecting browsers is easier and stealthier, 80% of cryptojacks are browser-based and about 20% are device-based.

Cryptojacking Facts and Trivia
- A fresh installation of an OS gradually slows down over time due to cache/prefetch data; so a slow system is not a litmus indication of a cryptojack.
- It is possible to program the cryptojack to utilize only a certain number of cores of your processor, say only 2-3 of them, to trick you into believing that the machine is slowing down naturally.
- Some rare cryptomining scripts have worming capabilities that allow them to infect other devices and servers on a network.
- Some others include multiple versions matching different architectures on the network, to allow for better spreading. A cryptojack might also simply download the implants for each architecture until one of them works.
- Cryptojacks can detect and remove competition. As soon as the script installs, it scans your machine to see if it is infected by competing cryptomining malware.
- The cryptojack can also scan your machine for your cryptocurrency wallet private key and exfiltrate it to the hackers. (If you do use some cryptocurrency).
- Thanks to cheap hardware manufacturing, China mines over 75% of the bitcoins and is yet to apprehend any impactful cryptomining campaign.
How to detect and prevent cryptojacking?
Cryptojack, like any other malware, can be detected and blocked by antiviruses and firewalls. On a personal scale, it is not much of a challenge if you follow the personal cybersecurity best practices.
The real challenge lies in dealing with a cryptojack in a professional (business) internet network. Not only are we dealing with a powerful network infecting malware, but things become increasingly complicated with the size of the network.
Add the BYOD factor and situations seemingly start getting out of hand.
In such a case a comprehensive solution like a well-configured hardware firewall or AI-driven cybersec solution like BhaiFi is strongly recommended if you want to be 100% sure.
Still, a lot can be saved, if you-
- Conduct periodic performance/security audits and device profiling drives to keep a tab on anomalies that might be indicative of a cryptojack.
- Standardize your software and familiarize all users with the resources utilized by it. Train them to raise an alarm immediately as they notice anything odd.
- Organize cybersecurity awareness workshops to help users detect phishing emails, malicious ads and website links. Cryptojacks are mostly delivered by emails and infected websites.
- Software (Endpoint) Firewalls and Antiviruses can help detect and block cryptojacking software.
- Enforce basic web content filtering at least and if possible, use the whitelisting approach as recommended by our security experts.
- Browser extensions can help. Unchecked Malicious Ads are rigged by hackers to spread cryptomining malware and ad blocking extensions like Adblock can help block them.
- Similarly, browser extensions of Antiviruses can effectively block compromised websites, malicious scripts and compromised downloads.
- In case the worst comes to pass, always conduct root-cause analysis to identify how the malware got installed. This can help formulate the security policy for the future.
Parting Words
While these tips can definitely help you ward off the majority of attacks, it must be stressed yet again that running an enterprise without comprehensive network protection is like leaving the gates of your home open at night.
It is an open invitation to cybercriminals and should someone decide upon a targeted attack, you have no defence against that at all. To know more about what all attacks your organization can face, check our series here.
So hopefully that’s about all you wanted to know about cryptojack - the cryptomining malware. If it wasn’t we are all eyes and ears.
Cheers and Happy Reading!

Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).