Your curiosity first - IP Spoofing is when we change the source addresses of the packets we send across on the internet - to either hide or to impersonate somebody’s else’s computer - the guy to whom that IP address actually belongs.
IP spoofing ought not always to be malicious in nature - people often do that to bypass authoritarian governments and organizations for whistleblowing purposes.
Talking about its ‘lethality’, IP Spoofing does little to no damage by itself but just like the rocket that carries the probe to space, IP Spoofing can be used to launch further attacks like DDoS (Denial of Service), MiTM (Man in the Middle) and XSS (Cross-Site Scripting).
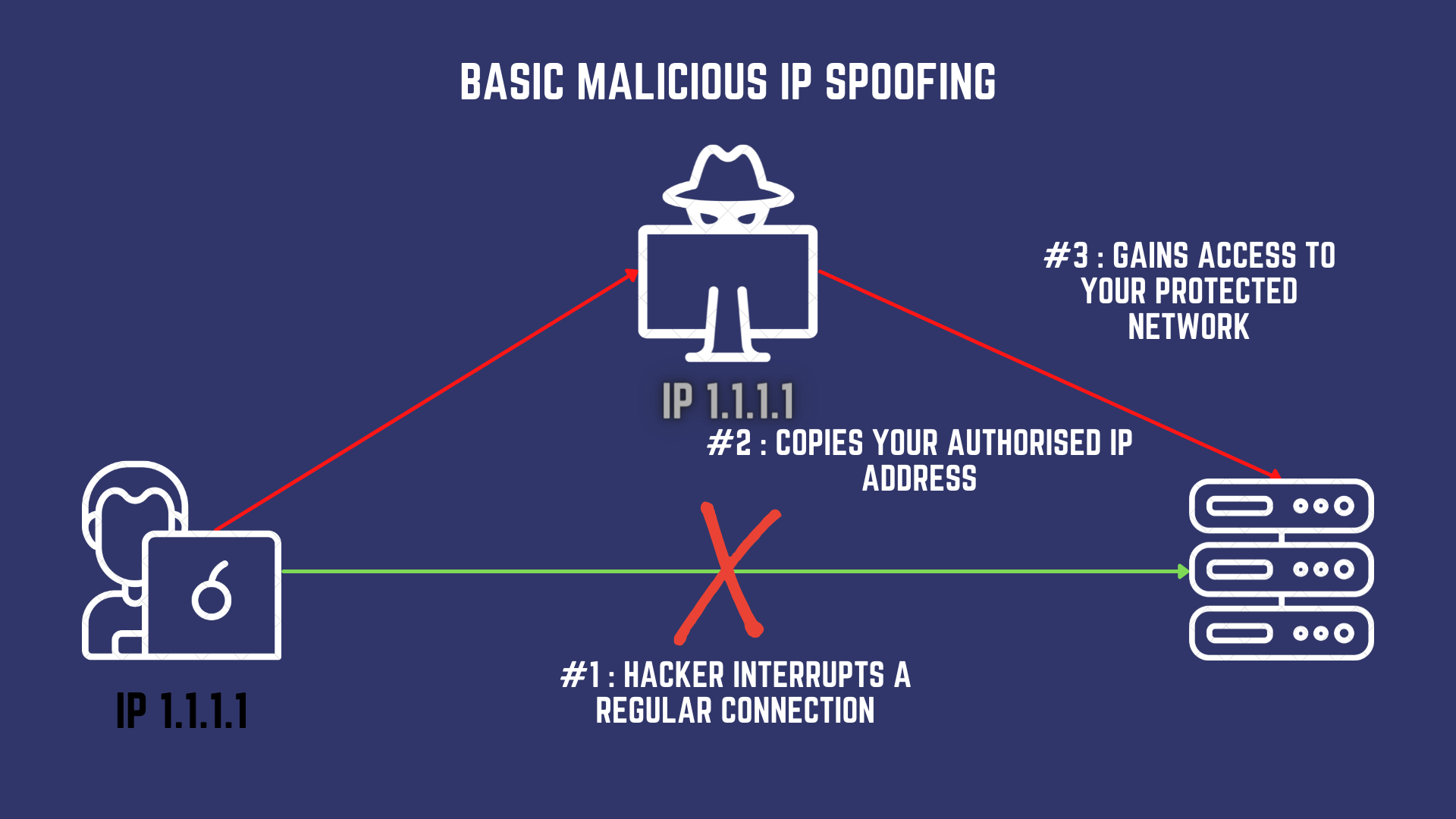
Why Bother?
Would it be a surprise to you if I told you that I could use your “secure office wifi” to conduct a DoS attack against somebody and your network administrators won’t even come to know about it?
“These spoofing based attacks are no rocket science - they are but a simple manipulation of the call and response mechanism of the internet - yet, how do you prove to the law enforcement that it was me and not you?”
Research by the Center of Applied Internet Data Analysis (CAIDA) states that:
99.9% of all attacks are carried out by machines using spoofed IP addresses. Those that are not, are carried out by amateurs.
Over the course of 2020, about 187,000 spoofing based attacks have been recorded every day, tallying at 126M for the entire year.
A total of 37.3M unique IP Addresses were targeted over the year past, implying that all major ISPs have been under some or the other form of attack at any given time.
Before we get to it - What is an IP Address?
IP (Internet Protocol) Address is a unique identifying address that helps in connecting your device to other devices/servers across the internet.
Since IP Address is unique, it can be used to pinpoint and reach your device on the network at a given time.
An IP Address readable by machines is made up of numbers and characters and looks something like 76.157.14.214. You are supposed to enter in your browser to get to that website.
However, thanks to this thing called DNS resolver, you don't really need to memorize it, but only need to write the name of the website like say www.bhaifi.com which automatically gets converted to the machine format.
What is IP Spoofing?
Any data that is to be transmitted over the internet will first be broken into multiple packets, and then those packets are transmitted independently.
The system at the receiving end acknowledges the receipt of packets before they are finally reassembled.
Each of these packets has an IP (Internet Protocol) header that contains information about the packet, including the source IP address and the destination IP address.
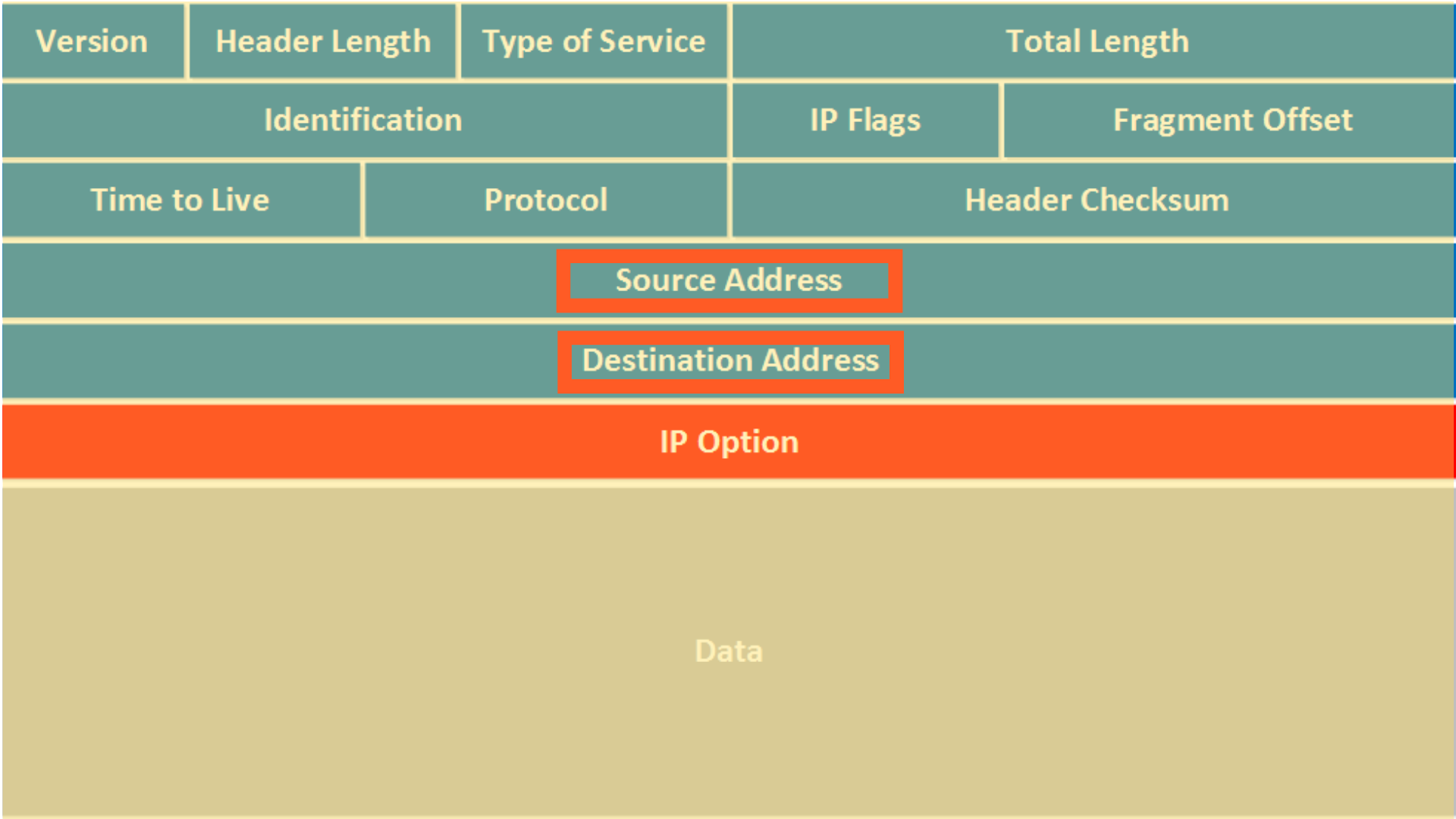
To spoof this IP, we use tools to modify the source address in the packet header to mask the origins of the sender to the receiving system.
What is the IP Spoofing attack?
The situation where spoofed packets are used to overwhelm a target system, deliver malware, gain unauthorized access or probe it for vulnerabilities, is categorized as an IP Spoofing based attack.
Call it an example, call it a tutorial; but launching a basic Volumetric Attack (DoS) leveraging IP Spoofing is really simple. All you need to do is-
- Run your VPN and wait for it to connect. VPN disguises your IP address.
- Run the LOIC (Low Orbit Ion Cannon) - a DoS tool - to bombard the target with bogus packets.
- Complement your attack with a split manipulation tool (won’t mention one) to fragment your data packets irregularly, confusing and overwhelming the receiver further.
And this is but one instance, on the whole - you can modify, complement, adapt and restructure the attack into serving multiple purposes in a single shot. After all, you have changed the very thing required to trace you - your address.
How dangerous can that be?
You send out letters in someone else’s name and address instead of your own - imagine what all you could deliver and in what ways could you land the other guy in trouble.
IP spoofing attacks can be categorized based on their procedure and motive.
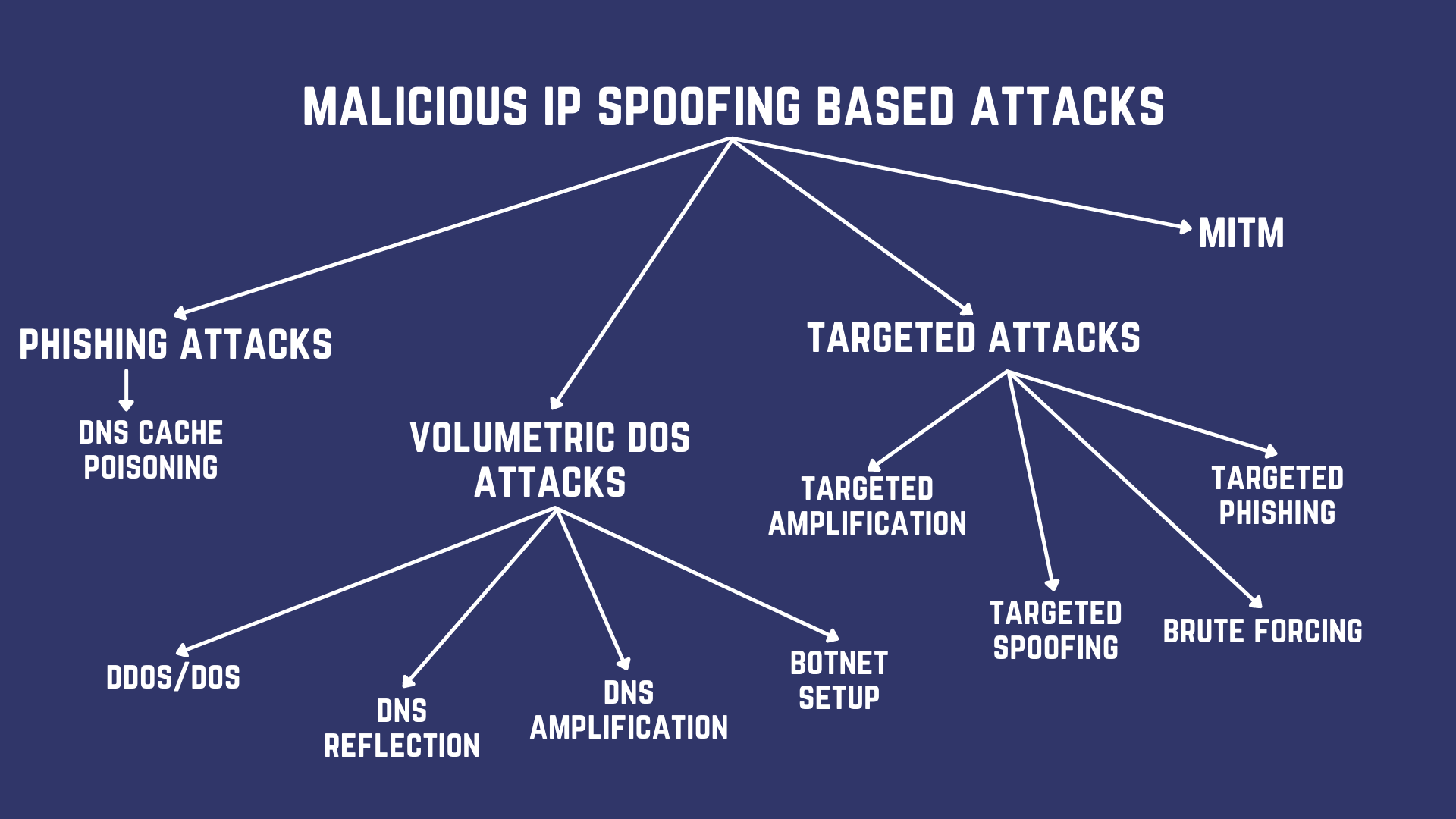
Volumetric Attacks based on IP Spoofing
Denial-of-Service (DoS) attacks overwhelm target machines with high-speed bogus traffic so that their ‘service’ is denied to the ‘actual’ or legitimate users. Direct query DDoS attacks are often the weakest, therefore the hackers have now shifted over to...
DNS Reflection Attacks, where the hacker will first impersonate your IP address and then send huge volumes of requests to the DNS server. The server believes you requested the information and replies to your system with a huge volume of data, overwhelming it. A deadlier variant of this attack is the...
DNS Amplification Attack, where the attacker requests additional information from the server causing it to reply with larger “amplified” packets. So this time, the DNS server will bombard your system/network with a huge volume of amplified packets, making this the deadliest DoS attack out there. An important aspect of DoS attacks is the...
Botnet Preparation; Botnets are zombie computers that have been penetrated by CnC (Command and Control) malware like RATs (Remote Access Trojans) and are controlled by a hacker. The botnet is usually prepared to launch DoS attacks or to mine cryptocurrency.
Phishing Websites
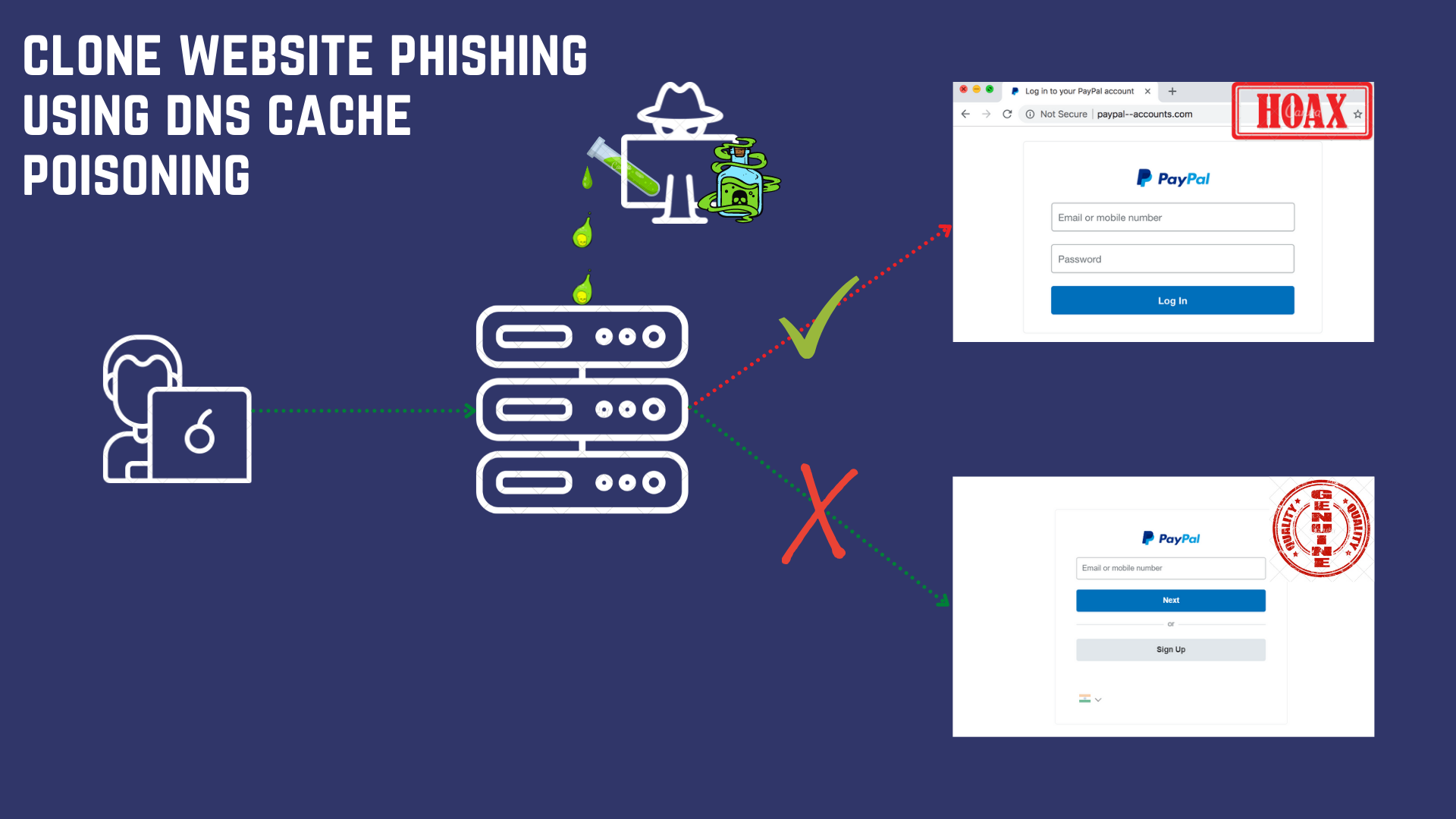
Phishing Websites are created as standalone websites with the interface and URL resembling the original website.
Next, the IP address of the original website is spoofed and as a result, the phishing site receives all the traffic headed towards it. This is achieved by…
DNS Cache Poisoning, where the hackers exploit and enter wrong information on DNS Resolver, causing it to redirect unsuspecting victims to their phishing websites.
The relief is, companies are always watchful of the same and more often than not, target organization will be an SMB .
Targeted IP based attacks
Remember, all targeted attacks are carried out against high-value targets.
Targeted DNS Amplification is a DNS Amp DoS that will be conducted against your system in case you happen to be an IT specialist/network/system administrator, wherein a compromise at your end could be disastrous.
Targeted IP Spoofing, is another attack you may face, this is done usually as a prelude to...
Targeted Brute Forcing, aka system breach to bypass IP address authentication on a secured network and gain access to critical admin accounts, privileges, data and for...
Targeted Phishing, because your colleagues/employers are more likely to open mail coming from you, rather than from some random source.
MiTM Attack
Man in the Middle Attack is carried out by inundating the local area network with fake packets that disrupt the traffic routing process and help the hacker interrupt communication between two computers.
The hacker then alters these packets with malicious code and subsequently transmits them without the original sender or receiver knowing.
IP address spoofing provides the launch pad that boosts the hackers into infinity.
How to defend against IP spoofing attacks?
Spoofing itself cannot be prevented. Endpoint Security is only partially effective against basic attacks. VPNs are somewhat safer and when compounded with personal cybersecurity best practices, are pretty effective.
For an enterprise network, best that can be done is preventing spoofed packets from entering - in short, comprehensive network security devices, protocols and practices.
Constant lookout/vigil needs to be maintained for indicators of compromise especially the more visible ones like spikes in traffic, outgoing packets with source IP that doesn’t match your company standards, abnormally high device activity trends and escalation/alterations in account privileges.
Lastly, enforcing strong data encryption techniques and multifactor authentication can help a lot. They make sure that even if the data is intercepted, the attacker will not be able to decode it.

Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).