Phishing is not some malware, it is a threat vector - a method of getting malware across to the target machine. When we talk about phishing attacks, the most common ones either make use of mailing services (phishing emails) or real looking counterfeit websites (phishing websites).
Usually, the mails are used to fire malware whereas the phishing websites are used to capture credentials.
The best way of understanding phishing is by looking at real-life fishing.

How do we fish? We lower the bait into the pond and wait for some dumb fish to swallow it. Once swallowed, we retract the fishing line, claiming our prize.
How do we Phish?
This time, we send over the bait via an email and then wait for the dumb fish to swallow it. Once the fish swallows it, we pull the line and claim our prize.
More formally, Phishing is a 90% social engineering and a 10% technical acumen based method of causing disruption.
Hiding malware inside files is not difficult, getting you to click on the malicious link or download the infected file is more critical. Hence the cybercriminals leave no stone unturned to make their email/website look as genuine as possible.
In a targeted attack, they can even go as far as to hack the email account of somebody you know/trust and will then send you mail from there to increase their chances.
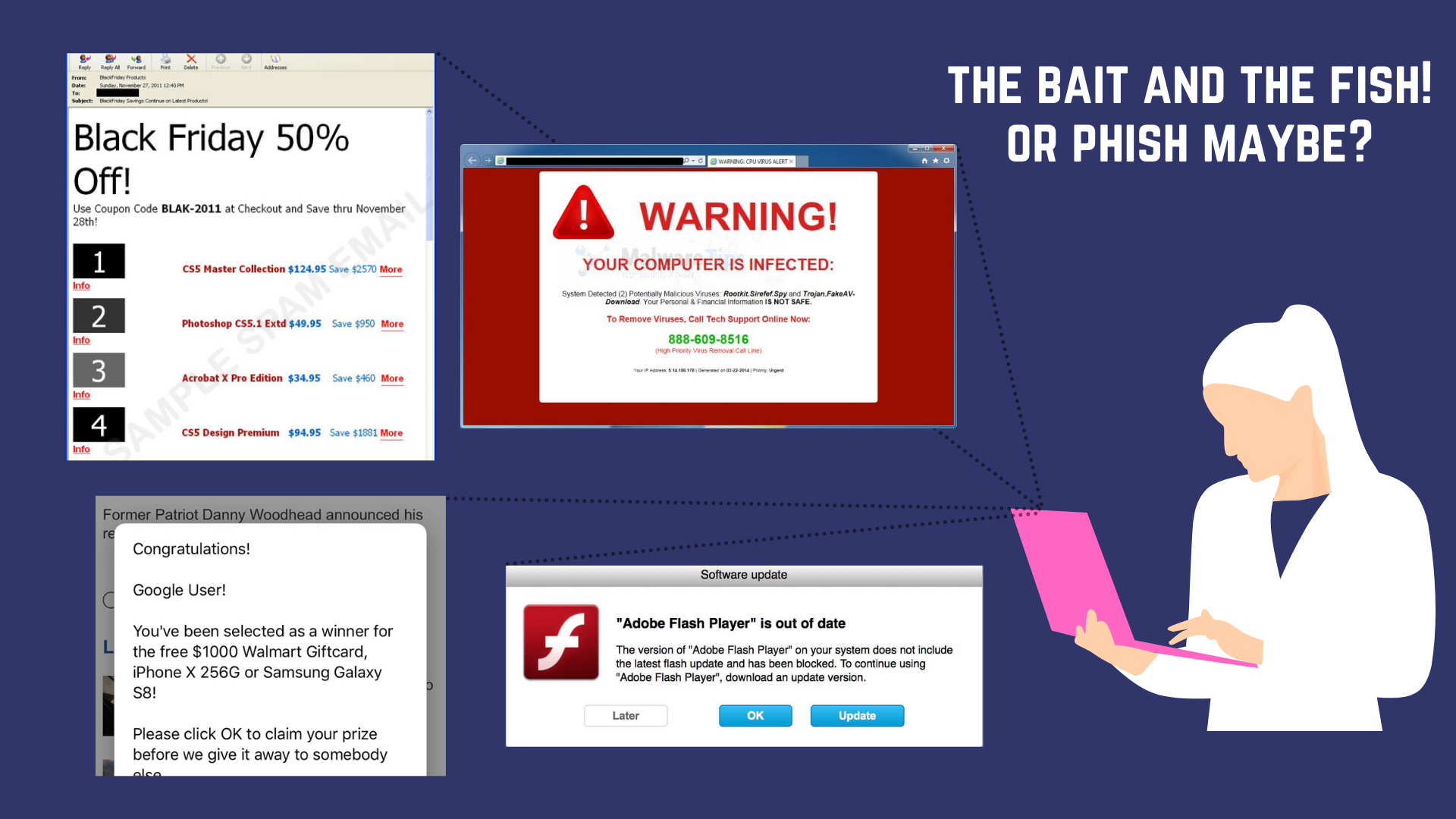
Why Bother?
As already discussed, Phishing continues to ace out in both, its commonness and its success rate. However, what if I told you that phishing also aces out in terms of growth - the number of incidents swelling by over 225% in 2020.
Research from Forcepoint indicates that 75% of organizations around the world have experienced a phishing attack in 2020, and 74% of these were actually successful.
To date, information (credential) capture remains the top motive behind the attack (47%), followed by ransomware delivery (18%), trojan (RAT) delivery (15%) and spyware delivery (8%).
According to IBM, nearly 1/5 companies that suffered a malicious data breach in 2020 were INFILTRATED DUE TO STOLEN CREDENTIALS.
With 44% of attacks conducted in its name, Microsoft is the most impersonated brand globally when it comes to phishing attempts, owing mainly to the popularity of Windows OS.
What is a Phishing Email?
A phishing Email is essentially a malicious link/attachment bearing message disguised as something important to get you to click on! It exploits your greed and fears - a request from your bank, investor or an account deactivation warning.
Recent research has shown that 96% of social engineering attacks are delivered by email, while just 3% arrive through a website, and 1% are associated with phone or SMS communications and malicious documents respectively.
A big chunk of Phishing Emails (35%) are targeted towards Software-as-a-Service (SaaS) users and promise special features/product upgrades.
Over 90% of malicious attachment bearing phishing emails would either turn out to be carrying either a windows exe file (74%), a script file (11%) or an office document (5%). Fending off against office documents and PDFs (2%) is next to impossible given the sophisticated nature of malware involved.
What is a Phishing Kit?
A phishing kit is an archive of software tools that allow even people with little technical skills to launch a phishing attack.
A single kit bundles phishing website resources - the cloned legitimate website, credential stealing overlay script, remote access trojan and other support/modification tools - ready to be installed on a compromised website.
Once installed, all the attacker needs to do is send out emails to potential victims. Phishing kits, as well as mailing lists, are available on the dark web.
How easy is it to launch a Phishing Campaign?
Let's say you have next to 0 technical acumen - you can still launch your very own phishing campaign for less than $100! All the ingredients you need are available on the dark web.
A phishing email list that costs somewhere between $40-$80, a basic email address spoofer ($12), a phishing kit ($5-$15), and a free VPN like Psiphon are enough to set your very own campaign into motion.
Feeling more evil? Add another $100 and you can load your malicious mail with ransomware and extract 10x the value!
Is it possible to launch a phishing attack without social engineering?
Yes it is! DNS cache poisoning is a method of carrying out a clone website phishing attack without requiring you to click on a malicious link. This is an advanced targeted type attack and needs a whole article to itself.
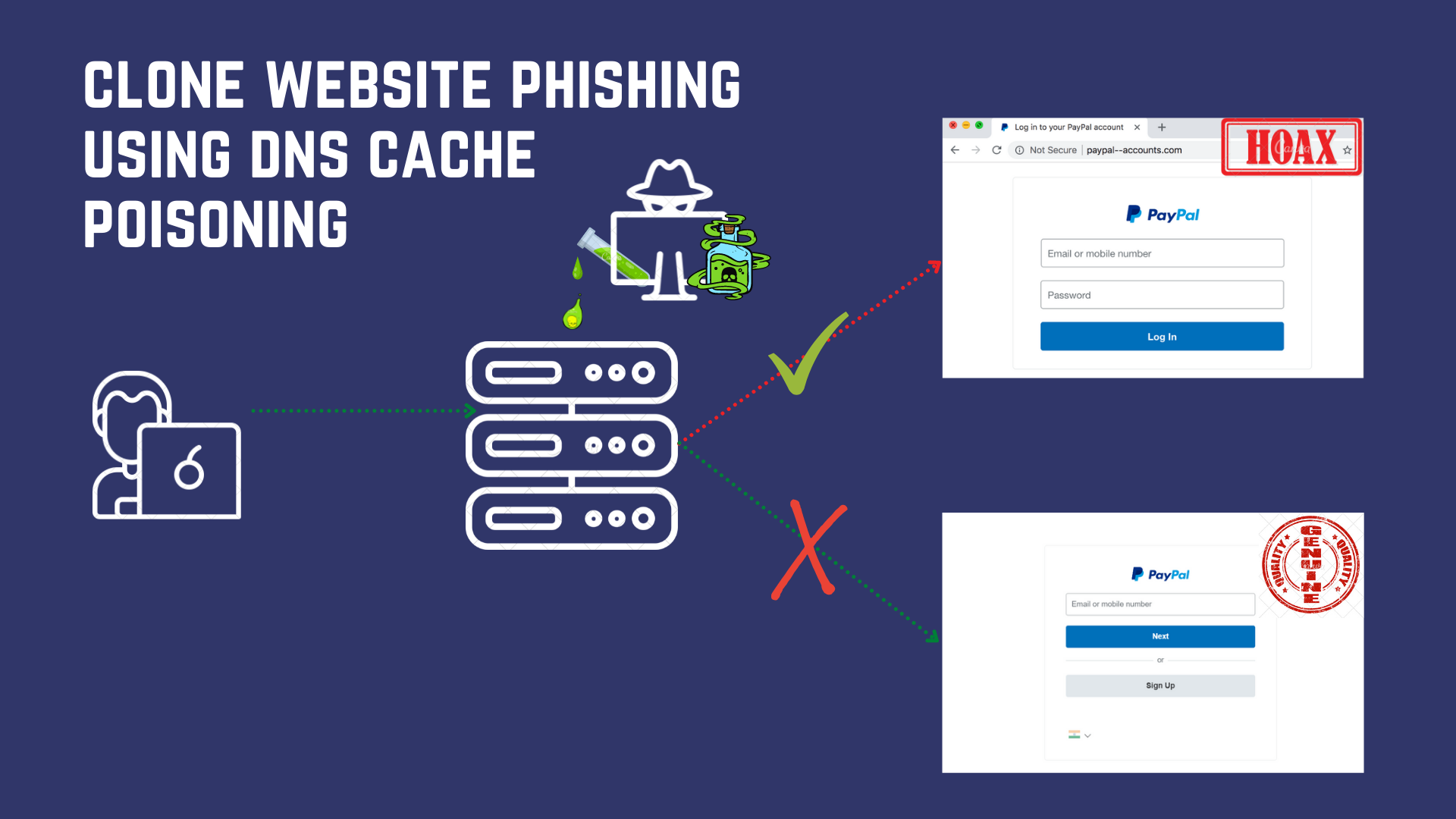
We'll be looking at social engineering based clone website phishing soon ...
Types of Phishing Attacks
Broadly, phishing attacks can be classified into the following 6 categories depending upon how the attacks are carried out.
Spear Phishing
While usual phishing is like wading across the water with a massive net to catch any fish that falls in its span, spear phishing is like pinning the “big” fish with your spear. Contrary to normal phishing mail, spear phishing mail will be addressing you personally and may even carry details such as your cellular contact or home address.
Catphishing
Is a type of online deception that involves attackers creating a social network presence as a fictional person (fake ID) in order to lure someone into a romantic relationship. This usually begins online and the victims end up divulging sensitive information, if not downloading professed malware.
Clone Mail Phishing
In clone phishing, the attacker will create an identical replica of a trusted legitimate message (most commonly a subscribed newsletter) from a reputed institution to trick you. Either the attackers penetrate the legit source, or create a ditto copy of it.
Clone Website Phishing
This is the best way of gathering credentials. The attacker uses a phishing kit to clone the login page of a legitimate website (say amazon) you have your account on. Then, you receive an email saying you need to verify your password. You click on the link, visit the page and enter your credentials.
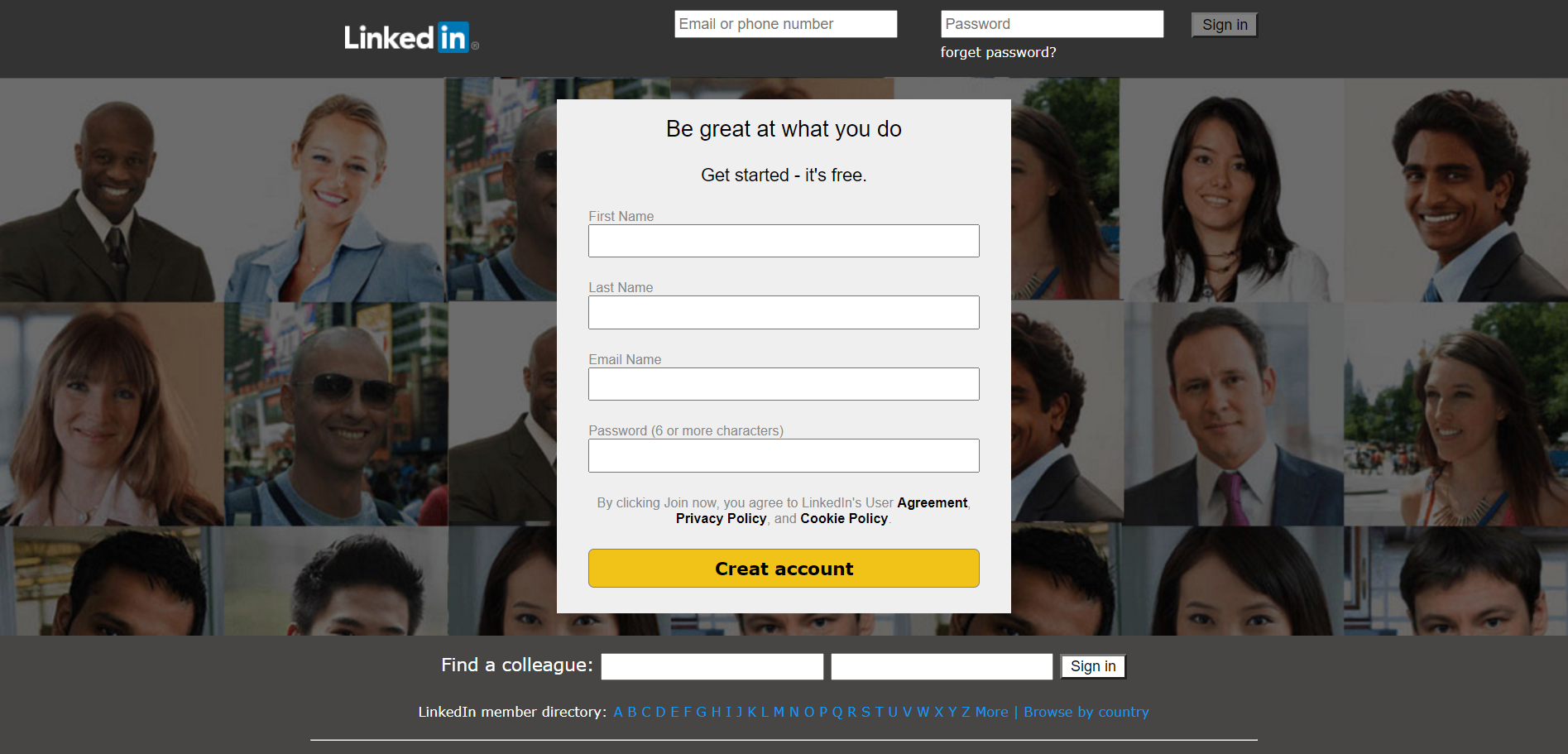
The phishing site records your credentials before displaying an “Incorrect password” popup and then redirects you to the real website’s login page.
On the second attempt, you are actually able to log in successfully eliminating all doubts that indeed you entered the wrong password the first time!
Vishing
Vishing (voice phishing) initially began with fraudulent calls but turned malicious over time. In a classic case, you will receive an IVR call apparently from your bank, investor or some other financial institution.
The IVR will then direct you to dial your account number, CVV, PIN for some verification or KYC purpose which gets leaked to the hacker.
Smishing
Although Smishing (SMS Phishing) accounts for less than 1% of attacks, they are deadly when they land. 78% of text messages are read and 37% are responded to as compared to respective 20% and 6% of emails, making this an exploitable opportunity.
How to not be a victim of Phishing?
The best way of preventing phishing is by learning to spot phishing emails.
Following are a few more tips you'd like to look at-
- Always check the spellings of the URLs in email links before clicking on them.
- If the URL of the website doesn’t start with “HTTPS”, or you cannot see a closed padlock icon next to the URL, do not click!
- Always pay attention to details of website design, while the attackers try to make it look real, there always remain flaws that can be caught.
- Browser add ons like Cloudphish can help. Even Adblock can help detect and block phishing ads. Similarly, browser integrations that come bundled with antiviruses can also help.
- Installing antivirus can help, even a free version is better than nothing. Basically, the sandbox thingy is a pretty helpful feature that helps contain malware infection.
- If you receive an email from a source that appears suspicious, contact that source with a new email, rather than replying directly.
- Regularly rotate and update your online account passwords to prevent the attacker from gaining unlimited access.
Parting Words
At some point, the situation will inevitably boil down to “how dedicated the cybercriminal has been in designing the mail” and “how observant you are about leaving your next digital footprint.”
The good news is that many mail services now have this inbuilt anti phishing mechanism in place which limits the possible propagation and download of malicious links.
Still, it is always better to have comprehensive network security - segmentation, DMZs, IDS/IPS, filtering, blocking, forensic logging - not just for stopping an attack but minimizing the effects in case one does happen.
Cheers and Happy Reading!



Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).