It is just another day at your office when a guest, probably there to meet somebody, walks in.
Its the age of today and so its naturally impossible (as well as uncourteous) to keep a guest waiting without access to internet.
So, when the guest walks towards nearest receptionist, he is automatically pointed to the QR Code/password for the Guest Network.
Once having connected his device, your guest conducts a quick port scan of your network to look for vulnerabilities.

It is not long before the guest has successfully located the smartphone belonging to somebody from your staff with credentials required to access network admin panel.
Since you have just started off on your business journey, you didn't bother with either securing or managing your wifi network - it is just the beginning and why would someone attack you - nothing of value here, you wrongly presume.
And that is where most of us go wrong - even if your enterprise doesn't hold huge volumes of money, you definitely do hold a treasure trove of user data - name, address, contact etc. that, believe me, are equally lucrative to a cybercriminal.
An unprotected network is like a fish tank for a cybercriminal - it saves their time as they don't have to wait around for potential targets to take the bait - like otherwise on the internet.
Keeping your business running
Now, networking is a big thing - so for simplicity, engineers have divided IT networking into two main components - network management and network security.
Frankly even if the boundary does exist, it is somewhat overlapping and this region of overlap is all we need to keep your business running. At least the online component of it.
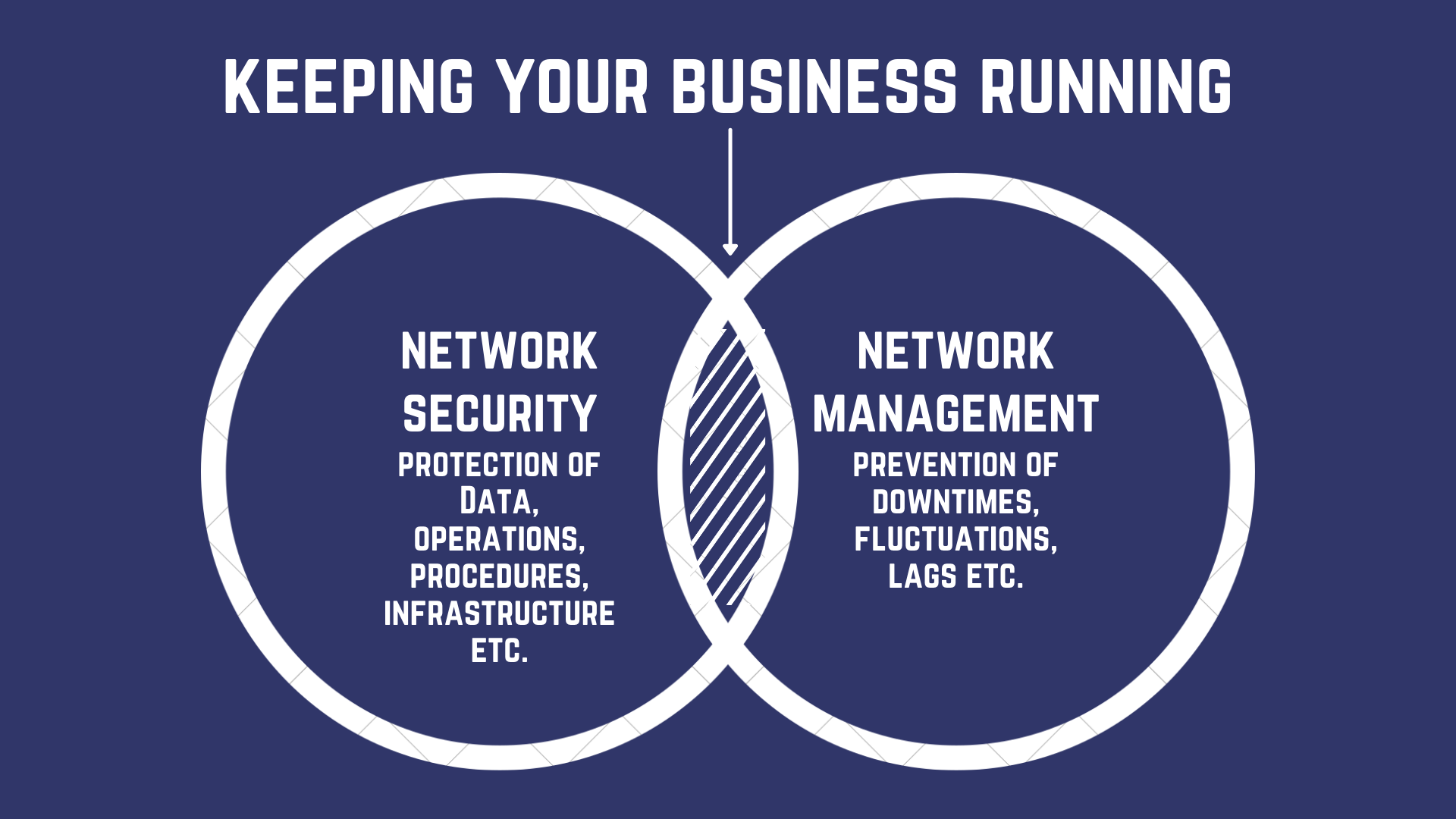
A well managed network will be secure in its own right - as it will be easier for the IT personnel to monitor and manage threats and vice versa; it is always easier to manage a properly secured network.
We can conclude that network management and network security always go hand in hand.
Networking traditionally
Has mostly been centered around everything you can imagine - from bulky, serious looking equipment to a horrendous mesh of wires and antennas scattered all around.
And that is still true to a degree, for example this very basic network with at least 1 component of each type -
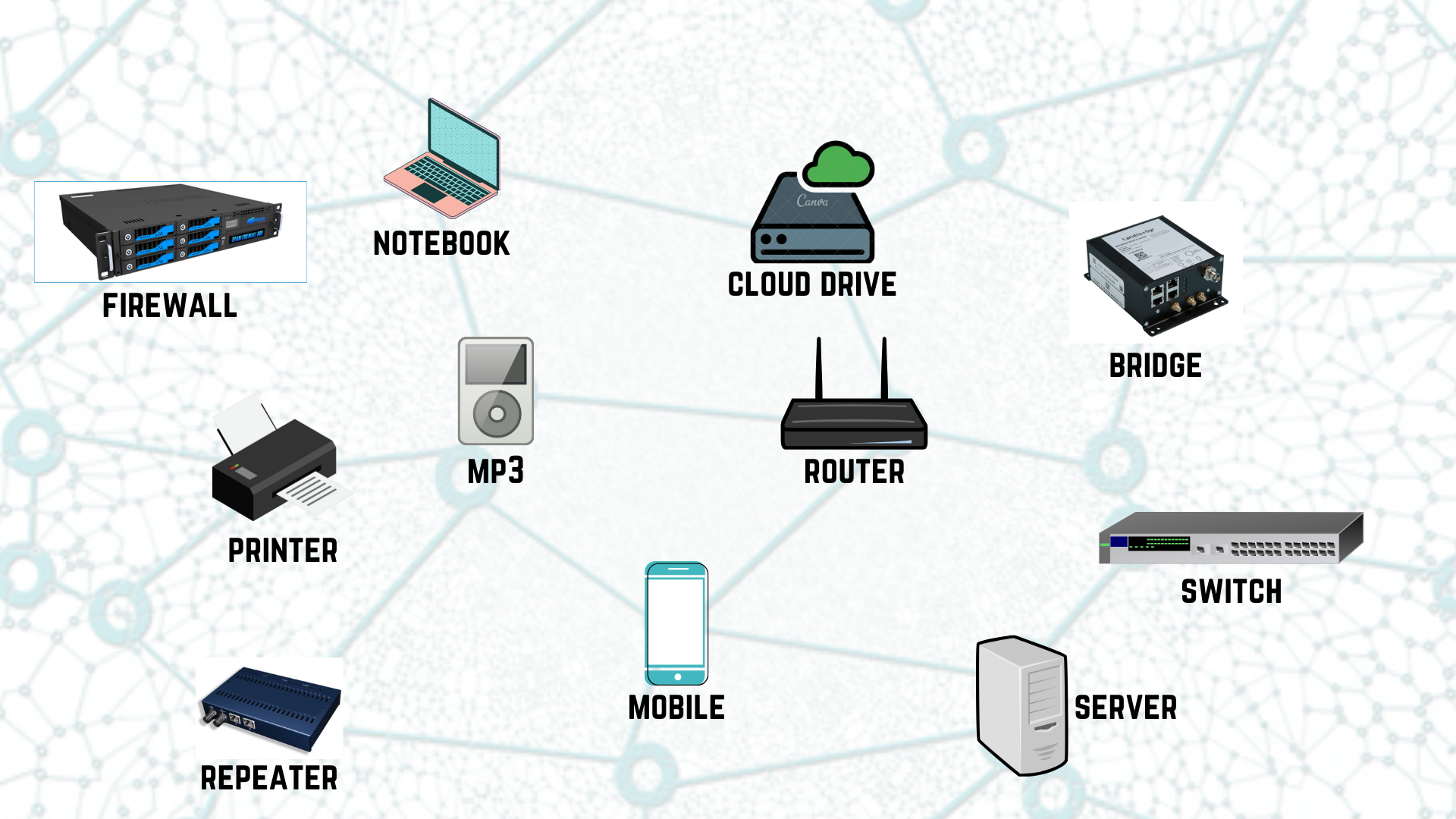
You don't need to have them all to get your network up and running, but this minimalistic setup serves as a standard for benchmarking.
In a real world scenario - the size of this enterprise network is going to grow with the addition of more people, bringing more devices - laptops, smartphones - making it all the more difficult and costly to maintain, administer and secure if we are to stick to traditional means.
Too Centered around the firewall?
All management and security aspects of this network we discussed above, inevitably center around the firewall.
The firewall - consider it a CPU that has to run 24x7 and is primed to secure and manage your enterprise network. Usually placed at the entrance of your network, the firewall protects it by denying entry to malicious elements.
Being a CPU like entity, the traditional hardware firewall has similar limitations - the hardware.
Imagine investing in the best CPU around today - loaded with best in class processor, RAM, graphics and disk, but will they remain same way a little beyond 2 months from now?
And what is going to be its state after 3-4 years?
In order to operate the firewall, one needs special training focused around its operating system, usually provided by the manufacturer.
Compatibility issues that pour cold water on 'fire'.
A Firewall cannot be integrated with every other piece of hardware you have in your office - integration is difficult, time consuming and impossible in many cases.
The device monitoring - a feature meant to keep a tab on the health of devices connected to your network - is most affected by this incompatibility problem, requiring drastic last minute budget reconsiderations.
As a result of all these complications
Cybercrime figures around the world (and esp. India) have shot up significantly. Just look at the loss, rather wastage of resources (in million USD)
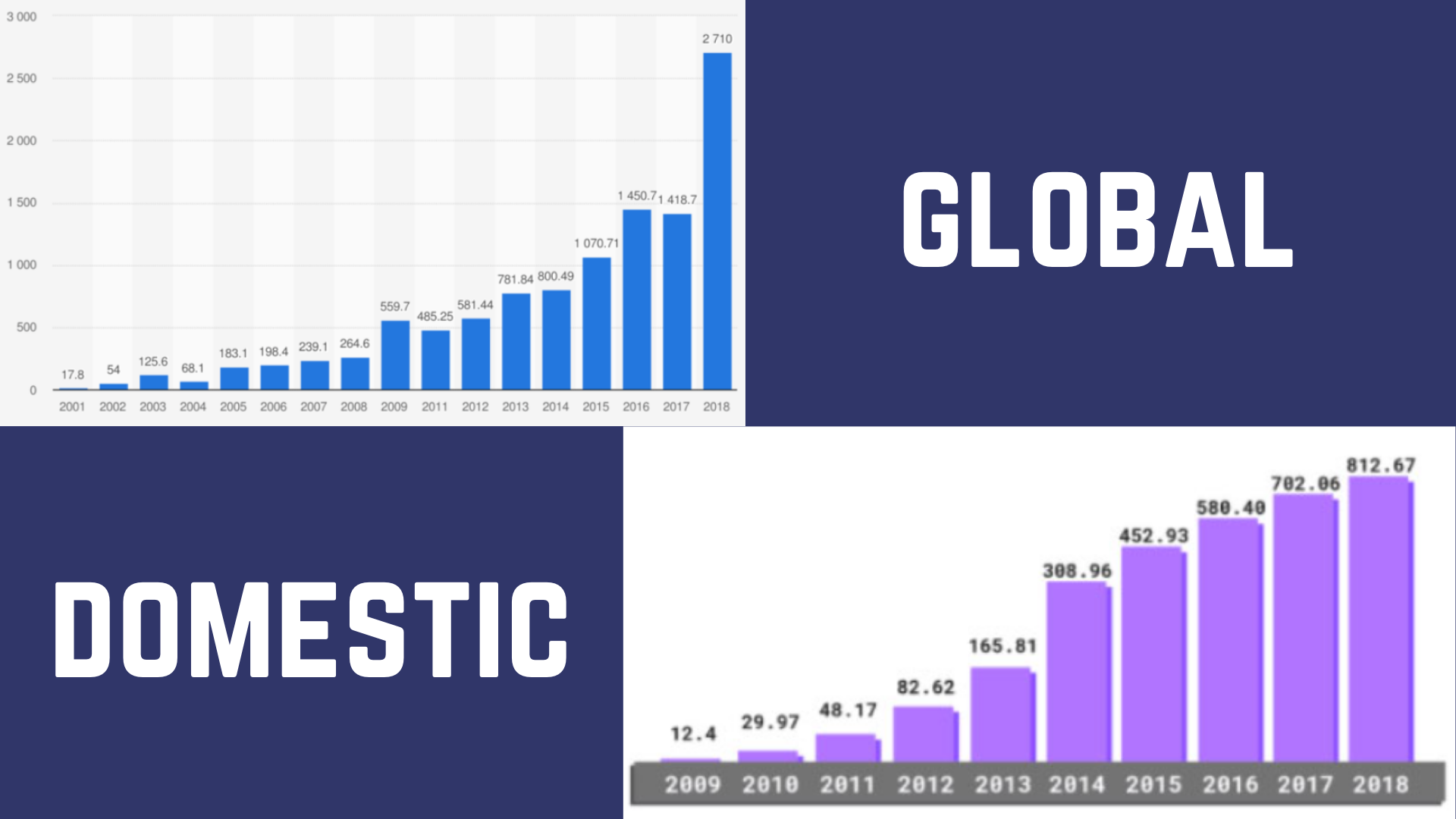
Most small and medium businesses believe that investing in cybersecurity is not just expensive but too cumbersome and mentally taxing for its own good.
And as a matter of fact, given the traditional approach to enterprise networking, this school of thought is not completely unjustified either.
But things are changing fast - Next Generation Networking Solutions
Some milestone technological innovations in networking, in recent past, have not just challenged the traditionalists, but are poised to pull the carpet anytime.
Firewalls are never going to be the same again.
The Floating Cloud - Rapid adoption of cloud has made it possible for manufacturers to better integrate the firewall with threat databases (big libraries containing malware signatures used to compare incoming/outgoing packets).
Cloud has also made it possible for the firewall to be managed by IT professionals working off premise - firewall as a service.
Then, thanks to the better resource availability on the cloud, most of the processing functions of the firewalls have been boiled over (sent to the clouds) optimizing their size and cost.
Software Defined Networking - has not just made the firewalls more flexible, but together with the cloud, has upgraded its performance and flexibility by many a fold.
It has allowed for the application of advanced algorithming - Artificial Intelligence and Machine Learning based models that can now manage and secure your network autonomously.
This completely eliminates the need for skilled professionals to supervise networks.
The one stop supermarket - The next generation networking solutions come preloaded with many features that are not there on basic, even mid range firewalls; remember the complementary features we just talked about.
These include advanced security and management features like IPS/IDS, Deep State Inspection & Analytics, Anti DoS measures, VPN, Application Security and Threat Intelligence platforms.
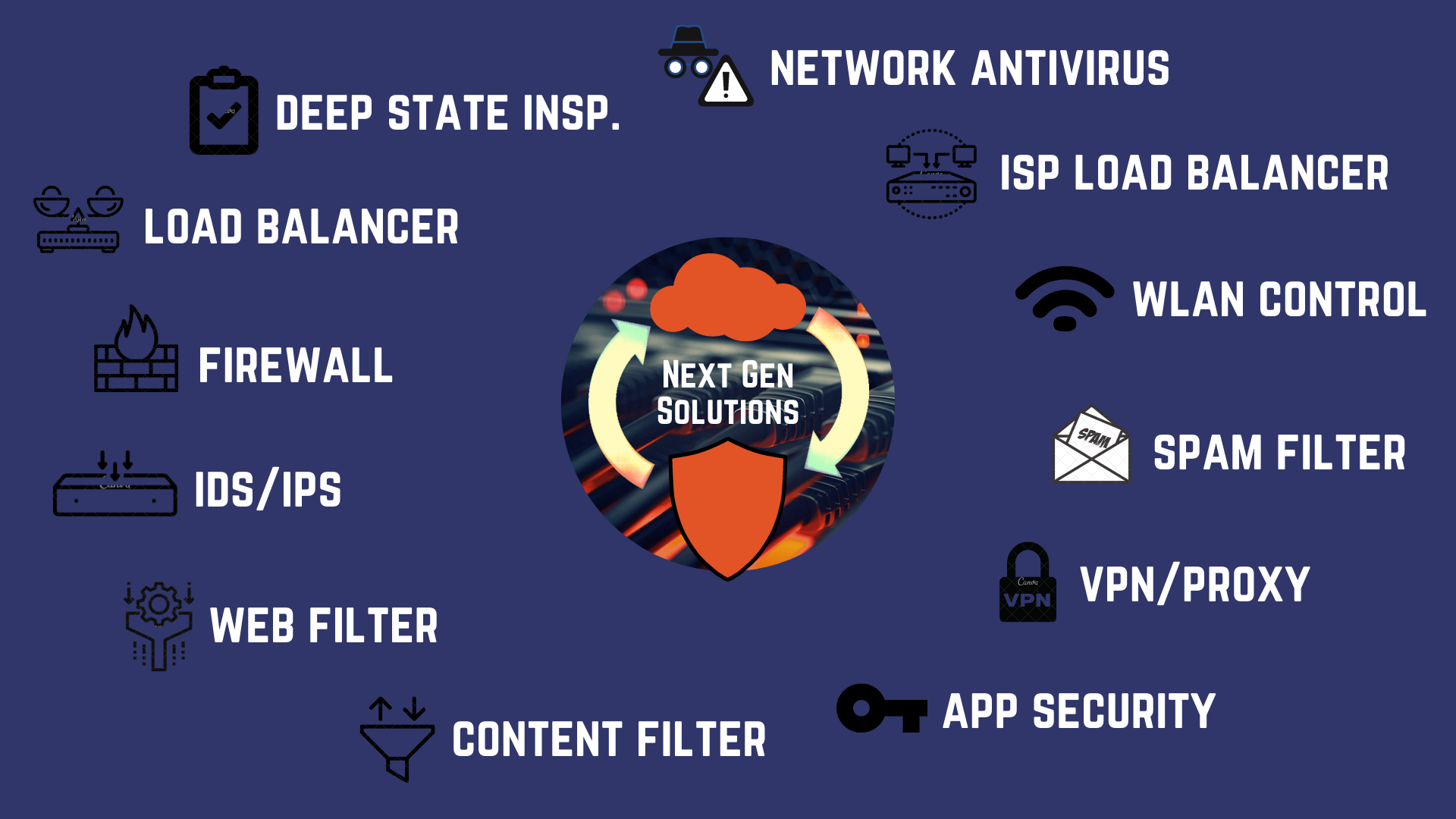
Firewalls sporting these additional features are known as next generation firewalls or UTMs (Unified Threat Mitigation) platforms - both fancy and mostly marketing terms, but the main takeaway here is that these firewalls (if you want to call them that) can save you a lot of 'getting things up and running' pain.
There can be differences depending upon brands but more or less it is going to be like plus minus one or two features.
A Firewall for Everyone?
Of course and why not?
With the rise of these next gen solutions, it doesn't really matter whether you run a small startup or a large enterprise, the "one size fits all" solutions are finally here.
This brings us to the next important point - next gen networking solutions boast of much better integration, owing largely to the ready availability of hardware drivers, tailored device profiling and automatic troubleshooting.
Once you plug in the firewall, it can autodetect its environment - making subtle adjustments to sculpt a security and management agenda best suited to your business.
NG solutions also prove cost effective in the longer run - even at the end of 3 years your next gen firewall is as good as new.
Its RAM, proc, disk - everything resides in the cloud and its capabilities were scaled to meet the demands of both changing times and your requirements, without even opening the door that leads to your server room.
What wonders would it have been if the same was possible with all devices - RAM automatically increasing from 3GB to 6GB as soon as you install Asphalt 9.
So long??
Frankly with the cybercrimes skyrocketing it was anything but expected for cybersecurity to have repositioned itself as such. Larger enterprises having dedicated network security setups are not the targets anymore with this shift creating a huge vaccum between cybersec demand and availability.
Cybercrimes against SMEs and SMBs have grown by a massive 210% over the past year and that figure too will have augmented 3x in 2021 itself.
Planning to be back soon with an exhaustive list of next gen networking solutions you might want to consider, and if you do have one in mind, don't forget to mention it in the comments, will surely pit it against rivals across all tracks before the list is up.
Also, if you think traditional security does the job better in your case, do let me know that too, along with why you prefer it?
Till next time.
Cheers and Happy reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).