Many of us tend to neglect the cyber threat looming atop our heads at all times despite there being a high probability that we have all doubled up against malware at some point in our lives. And I am pretty sure that some, like me, have lost valuable data to those pesky little troublemakers when formatting the entire system and reinstalling the OS was the only step that could be taken to halt the spread of infection. Still, I will say they were the good old days and good old viruses. The time when Avast! Antivirus looked something like this.
Good Old, CZ things have gotten much, much worse now. Nowadays, malware penetrates your machine to steal your data. Yes, the focus and design of malware has witnessed a considerable shift from replicating and messing up your PC to lying low, like a frog, until a fly passes by.
“Today, cybersecurity is more about user security and user privacy.”
Today the effects of computer viruses involve your personal information getting sold on some dark web black market. Today, the malware infection cycle involves pushing more Ads to your screen to gain money from disruptive advertising. Today those organized criminals want to hijack your computer and hold your data for ransom! In view of ‘that’ looming danger, we shall be covering some personal cybersecurity practices. Before we move on how to remove malware from pc, let's first look at symptoms indicative of malware infection.

What is Malware?
If you ask me, I'll say, don't get into the details. You don't want to know about it, all you want to do is avoid it. But just for heads up, Malware is a broad term that inclusively defines different types of malicious tools such as Viruses, Trojans, Worms, Botnets, Spyware, Ransomware, Adware, Sweepers etc. designed to undermine your productivity and cyber wellbeing. And that is just the beginning, since, talking about just the viruses, you will be shocked to realize there are 10 of different virus strains - ranging from boot sector viruses, web scripting viruses or file-less viruses to resident and polymorphic viruses that have been identified. Not to mention newer entries that get added every hour. Another reason why I'd say we shouldn’t get into the details is that more often than not, a single infected file can (and does) carry multiple infections - Viruses, Worms, Sweepers or more sophisticated, profitable and easily deliverable - Trojans, Ransomware and Spyware. Most people simply refer to ‘malware’ as ‘virus’ and it sounds kinda sweet.
In a similar-ish case, the malware you meet might not be either of what we discussed. It could be let's say a hybrid of a virus and a worm, carrying the lethality of each yet lighter in file-size. More often than not, the malware you are more likely to meet these days will be a trojan fashioned into a spyware. After all ingenuity and staying a step ahead of your rivals is what cybersecurity is all about!
Warning Signs of Malware - Symptoms and Indications
The next big question is, how to check for malware infection? The answer in short is - it depends on the malware. Different malware have different effects on your machine. For instance, a botnet as it gets activated, tries to disable your antivirus and firewall before discharging its payload into your machine’s veins. A virus tries to disable the “show hidden files and folders” options in the view manager so that you cannot locate the infected file manually even if you wanted to.

A trojan delivered via a drive-by download attack will trick the windows defender smart screen through a fake verified publisher certificate and persistent prompting. The Smart Screen [No] option becomes nonfunctional, as the prompt is repeated until you give up and say [Yes], which installs the trojan. If your computer is crashing or freezing (mind you that is different from slowing down/hogging), then you might as well already be in for a painful ride since that is a ransomware probing your data to encrypt it. So, there are no strictly black or white virus indicators, but let's see what we have -
Computer Lags
There can be many reasons for sluggish and irregular behavior of the machine. More often than not, it could be that your machine is not powerful enough to support the kind of work you do - your applications - like those graphic intensive games we all want to play - are just way too heavy. But if not, and if, everything was fine just until yesterday when you opened a suspicious mail, or plugged in your friend’s flash drive, then you should as well run a scan. Malware can choke your disk, RAM and processor bandwidth by running their own malicious processes in the background and triggering malicious downloads. Malware can also infect your less secure applications, causing them to auto-launch. Again, the extent of damage caused depends on the type of malware and its purpose.
A ransomware, spyware or adware will choke your disk and RAM bandwidth while a miner will choke your processor bandwidth.
Slow Boot
Boot time depends on a lot of things - it could be a disk consistency check automatically scheduled by windows due to a bad shutdown or a windows update, but in both the cases there is a distinct difference. Update displays a “please wait” banner and check disk utility progress can be seen in the form of percentage on the pre-BIOS screen. Apart from that, the delay could also be indicative of aging hardware.
If however none of that happens and your system is taking longer than usual to boot with the startup screen freezing unresponsively, the culprit may be a boot sector virus - a virus notorious for affecting the partition table of a disk. You might additionally witness unknown programs that startup when your machine finally boots up. (Remember the Malware can trigger auto-launch!) You may become aware of the unfamiliar program when you start your computer via observing the system notification set or you might notice it by checking your computer’s list of active self-launch applications.
Blue screen of death (BSOD)
Frequent BSODs? Going by 99% of cases, either you installed an emulator (PlayStation or Android Emulator) that has messed with your paging file allocation, or you have messed with your paging file allocation yourself, or it is a malware! Some advanced sandbox avoiding viruses, file-less viruses, botnets and trojans are capable of triggering BSOD as a preventive measure, usually at a time when your security systems are attempting to apprehend them.
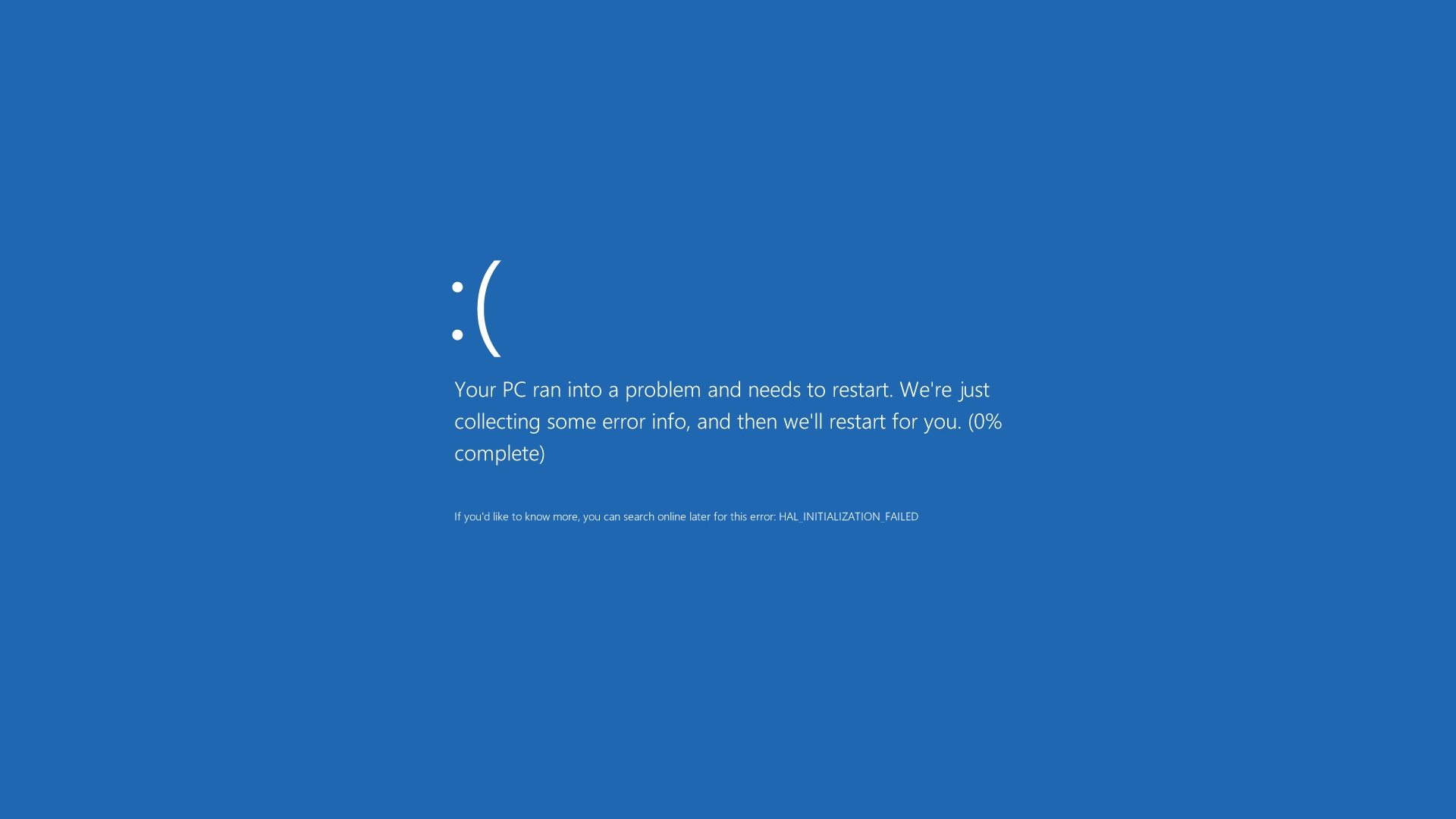
Other reasons for BSODs include incompatible/logically wrong device drivers, malfunctioning hardware (mostly RAM), overheating of components or overclocked hardware.
Programs opening/closing by themselves
A sure shot symptom that is indicative of a malware, no testing or sampling required! As already discussed above when we were talking about Slow Boot, this is a result of some strains purposely triggering your installed applications to trick you into believing that something has gone wrong with them, while the malware stays hidden from your attention. Trojan based malware like spyware, malicious trackers and adware usually employ this technique, although the adware generally triggers browser tabs with malicious/abusive and otherwise unwanted ads and in much fewer cases, installs and runs crap on your system, hoping deep down that you might come to love it.
Storage space filling up fast
Malware can fill up your storage by replicating - creating copies of themselves or their infected host files over and over until your space runs out. In the case of Windows, the malware usually attempts to damage/delete system files responsible for indexing, thus rendering the hard disk (or the particular partition) useless. Boot sector virus that alters the partition table of a disk, as discussed above, is an example of the same.
A considerably confirmatory indication is your system checking a particular partition of your hard disk or your complete hard disk at every boot. Though it could be indicative of consistency collapse due to file corruption, or a bad shutdown too, but in this case, the chkdsk utility shall run only once (not at every boot) and once successfully completed, your boot shall return to normal.
Missing or Corrupted Files
Modifying and deleting files is a symptom indicative of a system infected with trojan virus, resident virus or trojan/worm based ransomware. While a ransomware usually attempts to encrypt your files and hold it for ransom, the trojan needs to infect as many as quickly as possible to replicate faster than your security system can trace and disinfect the files.
Taking regular well structured offline backups seems the only viable defence against a Ransomware, given that some ransomware shred your files and wipe your disk clean despite your having paid them the ransom. Seriously, some cybercriminals designed their malware that way as some smart-ass had found a way around - using a rescue disk to recover the system, quick format of drives, a fresh OS installation and then using Recuva to recover the files.
Infected Browser
The relationship between your browser and malware is like that of the one between throat and common cold. Apart from frequent annoying pop-up windows (remember all browsers tend to block popups by default until you explicitly allow them) and links redirecting to wrong web pages, your browser can drastically slow down, experience frequent lags, freezes and might as well crash all of a sudden. Given the criticality of a well functioning, smooth browser to your productivity, and the fact that you might take some of the symptoms (like slow speed) as an indication of low bandwidth, you must at all times be watchful of any changes that appear on your browser that you didn't make.
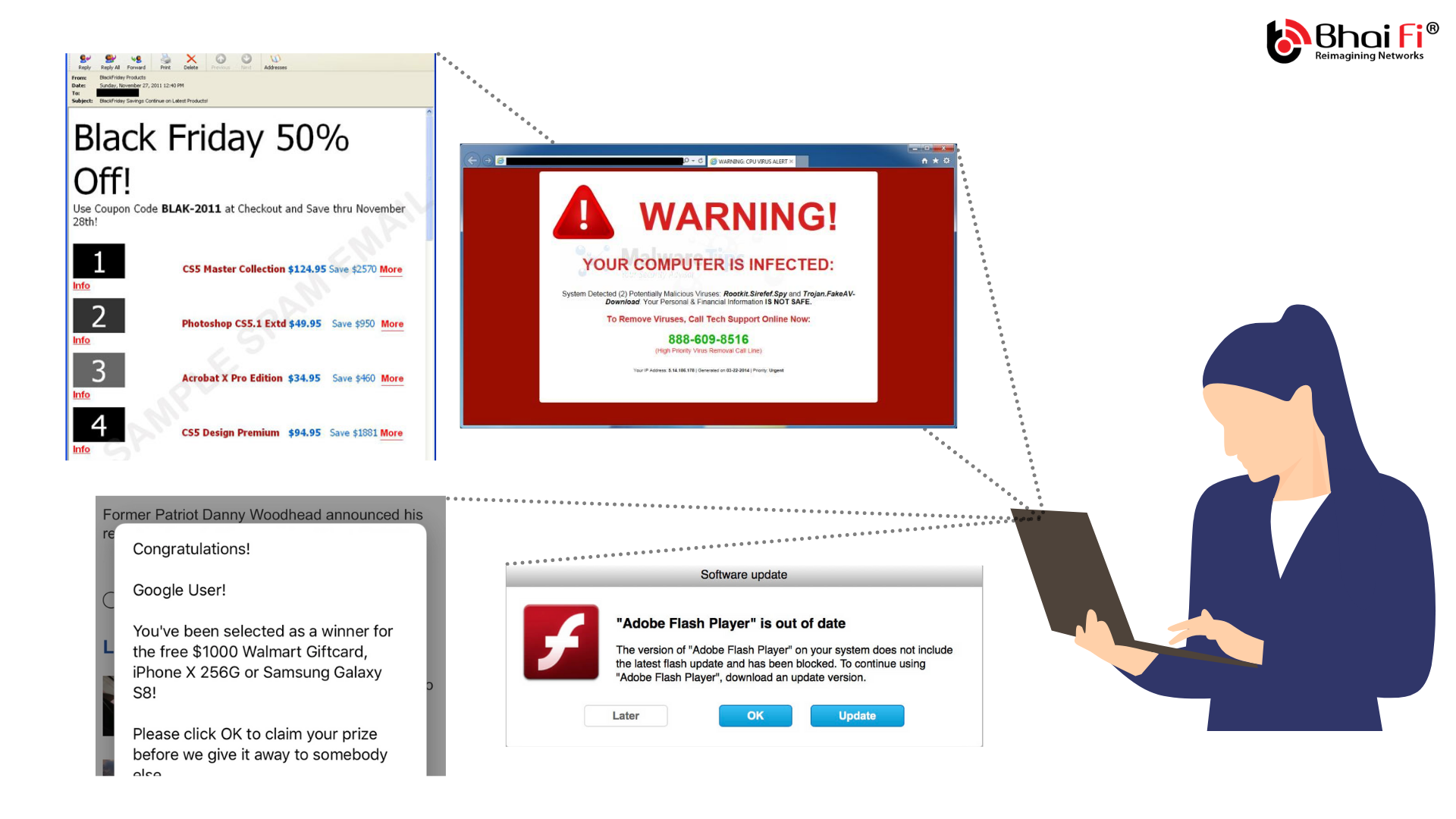
For instance, changes in default search engine or privacy policy or cookie settings, disappearing browsing history (browsers tend to keep history until it is erased or your settings call for their erasure after certain time/sessions) and disabled security/ad-blocking extensions are some signs you should watch out for.
Since javascript trojans don't affect the system, on the whole, the only symptom is that browser pages load abruptly and tabs are slower than usual (‘slightly’ or ‘considerably’ depending on how light/heavy the malware is.) Another way you can be sure is by checking the browser task manager (or the system task manager) for resource usage. If the values are higher than usual and increase/decrease disproportionately after opening/closing new tabs, then that should set your bells ringing.
Pop-ups, toolbars and other unwanted programs
Infection common to both windows and android, and perhaps the number of instances for which have shot up multifold over the recent years, this is a symptom of adware. Once an adware has successfully installed itself onto your system (beware, it doesn’t have to be an installed application - the adware is capable of getting installed as a flash plugin on your browser), it can get your browser to open malicious links or simply pesky advertisements. Then some adware can go on to install their own toolbars and programs you don't want.
While browsers are the primary target for adware, they are capable of targeting the OS as well, especially, android, causing ads to appear every few minutes (even on the lock screen) and as a notification. On windows they can embed themselves on the taskbar and use the notification pane to push their scam.
Infected Emails and Social Media Messages
The flagship achievement of Melissa, a virus that wreaked havoc across the silicon valley in the March-April 1999 was her newfound ability to send out emails containing her replicated copies. With the internet security not being what it is today, more often than not, emails from contacts containing malicious links were not filtered, in addition to being trusted by the accomplice, whose system took off on a ride. Today, thankfully Gmail can not just filter, but also actively scan and block malicious content, but just as we discussed, nobody knows for how long. So if you do come across a situation where your contacts claim to have received a malicious link from you, (or simply a link from you, when you didn’t send anything over) it's time to run a scan.
Simply put, today, attackers employ several techniques to disrupt and compromise networks and systems and are actively innovating for new ones. The best defence you have against them is your cyber threat awareness. What is the biggest cybersecurity threat they ask? Your lack of awareness!
Then .. how to protect your computer from viruses?
Not saying that windows defender is any bad, it has surely come a long way from what it used to be in past, but still finds itself pretty defenceless against serious threats. RTP (Real-Time Protection or passive scanner) doesn’t fare well against trojan based strains in general and botnets in particular. While it does advertise some sort of ransomware capabilities, I bet you don't wanna try.
Prevention of Computer Virus
Given prevention is better than cure, it is good to formulate a cybersecurity strategy aimed at preventing malware infection. Apart from being aware, taking regular backups and staying vigilant, it would be a good idea to install at least a free antivirus. There are some excellent free anti-viruses like Avira, Malwarebytes, Avast!, AVG and Bitdefender that can provide you with a greater degree of security. You might also want to consider the free variants of some top-notch security modules like Kaspersky but they offer pretty limited features like file scanners (antivirus only).
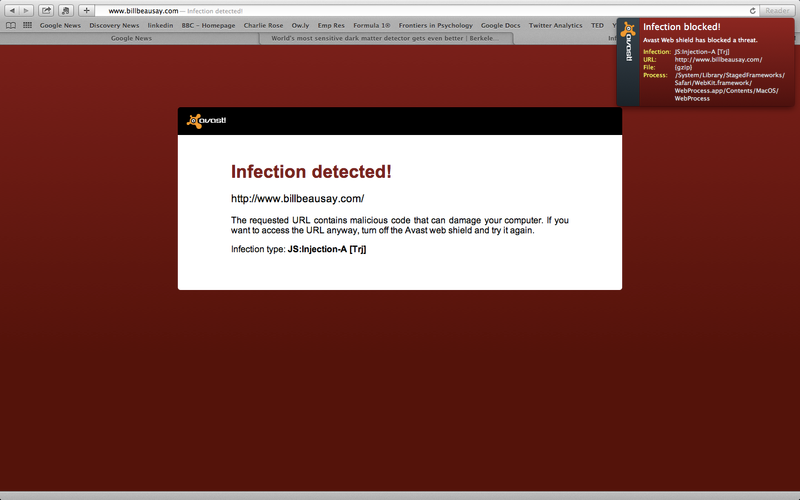
The good thing is, almost all of these anti-viruses come equipped with 'safe browsing' - a browser plugin that actively blocks links to malicious/unsafe websites and scripts. Last but not the least, always make sure you are running the latest version of the software with virus definitions set to auto-update.
Both software and hardware firewalls can also come in handy when it comes to preventing malware infection. So if your home/workspace network doesn’t have a hardware firewall installed, you should certainly download a free version of Comodo. Talking of an office/enterprise, cyber threat hunting is generally done at the network level. BhaiFi is one such platform that identifies and blocks malware in real-time keeping your entire network safe.
What if your computer is already infected?
A good question! Since most free tools (and windows defender) are capable only of detecting and neutralizing the malware (deleting/quarantining or disinfecting the file), but are kind of incapable of reversing the damage that has already been caused to your system. Setting up system restore points at regular intervals or backing up system image in a pen drive are your best bets in such a scenario. It is also a good habit to back your registry up when you are taking data/image backups to help preserve your advanced settings.
Software like the VER (Virus Effect Remover) and the MRT (Malicious Removal Tool) utility can also help reverse the damage caused by a virus, but that mostly incorporates the system settings that got altered, they cannot recover your files. A good idea is to run a file recovery software like Disk Drill, Recuva or EaseUS once the malware has been removed and the system state has been restored.
Software like CCleaner are also pretty helpful as they can help you remove spyware, trackers and adware. CCleaner can also be used to help maintain your PC by cleaning up your digital junk, defragmenting your drives, registry and memory.
Summing Up
Ah! And the time has flitted by so quickly - we are at the conclusion already! So rounding up, the purpose of our time together - it was to acquaint you with common symptoms of malware infection or the virus effect on your computer. It’s important for individuals and organizations to recognize how their systems can be targeted so that proactive steps may be taken through a layered security approach as countermeasures to the cyber threat. In the next article, we shall be looking at how malware attacks are carried out - various entry points or ‘highways’ that lead to your system, in addition to some other vulnerabilities that you might want to plug right away to help mitigate, even eliminate the tremendous risk to your data security and online privacy.
Feel free to discuss your doubts and thoughts in the comment section and don't forget to subscribe to our newsletter to be the first to read the next article as soon as it goes live.
Cheers and Happy Reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).