Ransomware is a malware that uses strong encryption techniques to lock down your important data. The cybercriminal who has infected your system with the ransomware then demands a ransom with a deadline. Fail to make the payment within the given time and your data is lost forever.
An almost impossible to decode 2048-bit encryption key makes sure you spend a higher amount trying to figure it out - yes an 8 GB RAM system will take trillions of years to crack it. In such a case, accepting the demands of the attackers become a smarter choice.
What is this ‘encryption’ thingy?
When we say that something is encrypted, we mean that it is converted from a readable format like this -
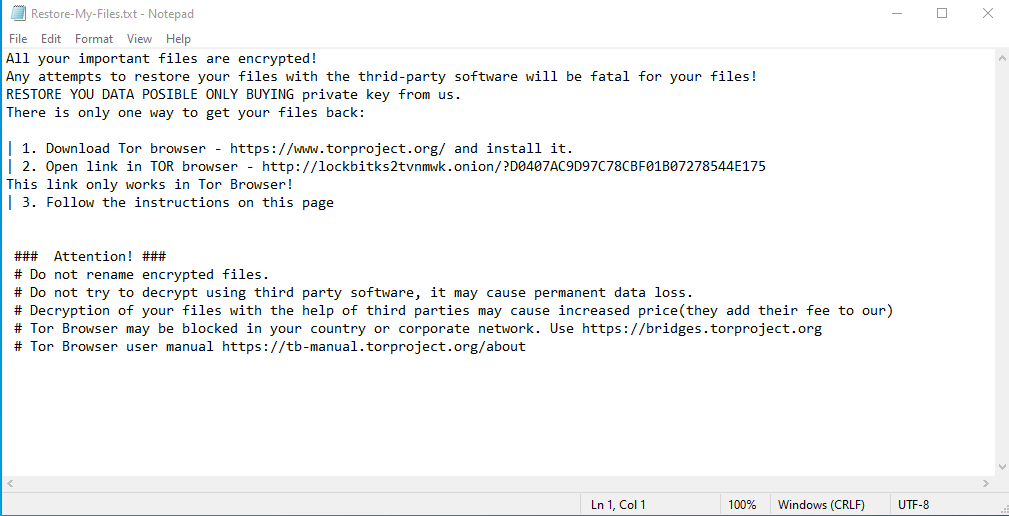
To something like this-
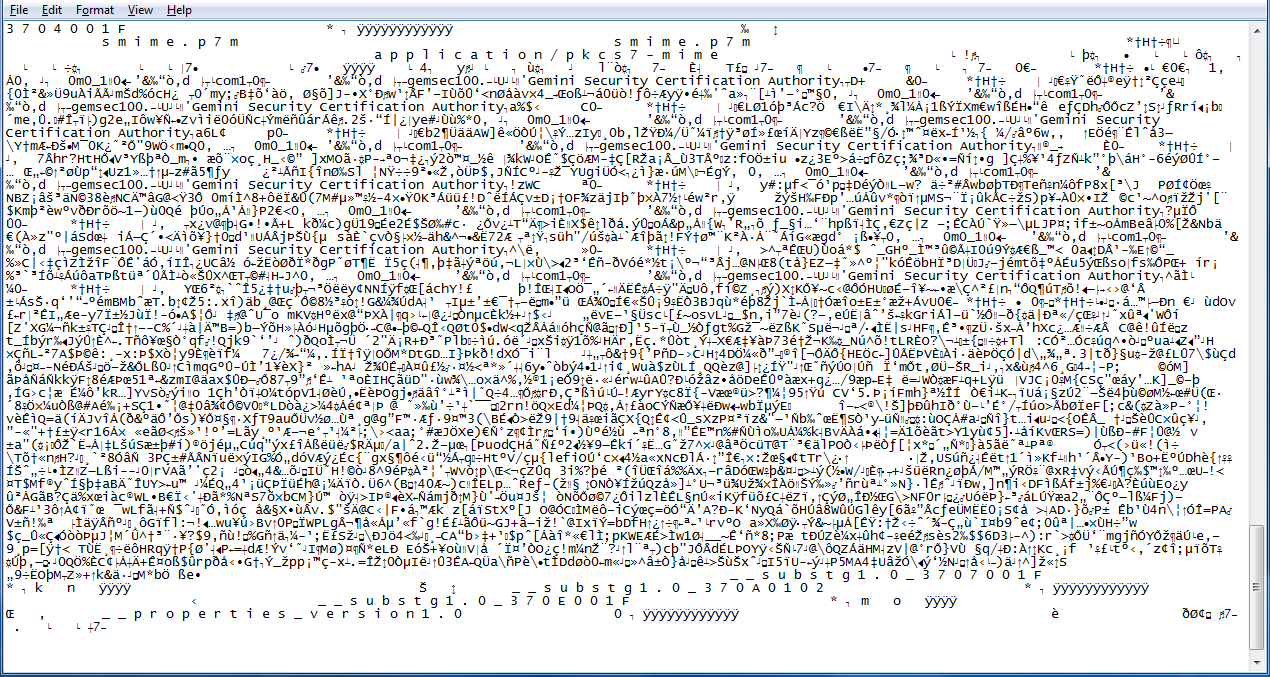
Readable only by machines. And there too, not every machine can read it though - to convert it into readable English again, you need the mathematical key we just talked about.
Why Bother?
Simply put, Ransomware is easy money and big bucks! The ransomware market has expanded rapidly since the beginning of the decade. In terms of the amount of ransom paid, time lost and other related costs,
In 2017, ransomware resulted in $5 billion in losses,
In 2019, we saw them grab some $11.5 billion and
In 2020, this figure stood at a massive $20 billion!
That is a 4X increase in a span of just 3 years! Based on the trend we can only wonder what 2021 has in store for us.
Businesses particularly prone to ransomware attacks are Hospitals, MSMEs, Coworking Spaces and Hospitality Chains, as these businesses have become increasingly reliant on the internet and their security standards are not up to the mark. It's estimated that 35% of ransomware attacks target healthcare orgs, 28% attack MSMEs and another 17% have been known to target Coworking Spaces.
How Ransomware Attacks - The Threat Vector
For Ransomware, the most common delivery system is a Phishing Email - through attachments masquerading as a file coming from a source you can trust. The goal is to get you to click on the link, on the image or download and run the attachment.
Although it is possible for ransomware like NotPetya and WannaCry to penetrate your network, without your clicking anywhere by simply leveraging the security loopholes, attacks like that are extremely rare.
Once the malware makes it to your system/network, it begins by disabling your security before proceeding to encrypt your files.
Where did it all begin?
The first known malware extortion attack was carried out in 1989 by Joseph Propp, using his "AIDS Trojan". This particular attack was easily defeated owing to a severe design failure - the malware simply encrypted the names and hid the files on the hard drive.
But, the idea of a trojan deployed to extort quickly caught the fantasies of several criminal-minded coders from around the world.
Types of Ransomware
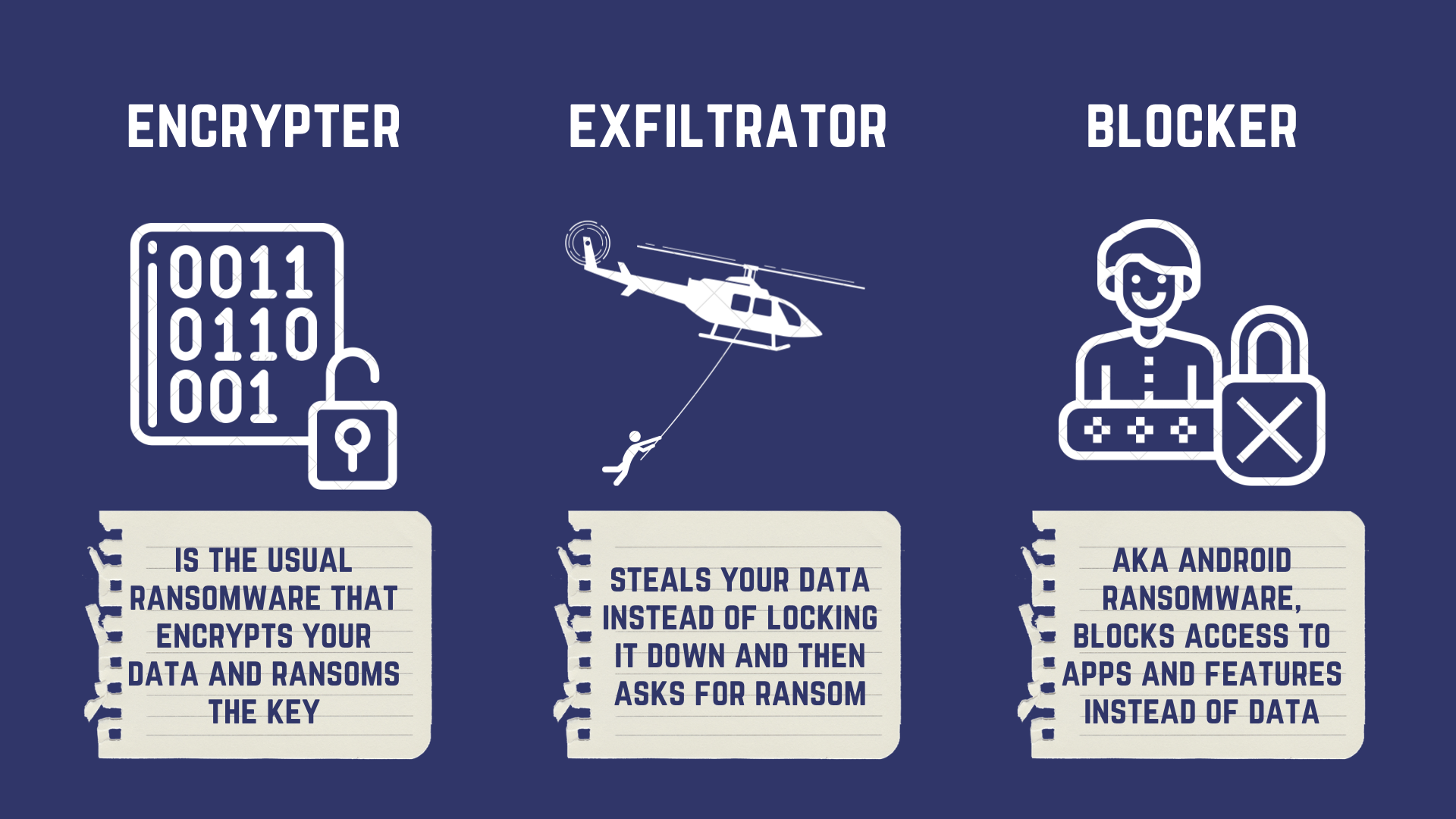
The Encryptor (The locker)
The usual guy around, Encryptor leverages strong encryption to deny you access to your files. In most of cases, the encryptor does not lock down your interface, though it does use overlays to deny access to your security dashboard.
The Exfiltrator (Leakware)
The steps of attack are almost the same - data is scanned, critical files are located, prepared (moved to encryption directories) - but instead of being encrypted, it is exfiltrated (hijacked). Your data is leaked to the attacker, earning it the name - leakware. The attacker will then threaten to publicize your sensitive data unless a ransom is paid.
The Blocker (Smartphone Ransomware)
Since mobile devices are ‘always awake’ and always in sync with the cloud, restoring data is not a difficult thing to do. Due to this, the ransomware that attacks smartphones is essentially a ‘blocker’. It targets Android's core functionalities using ‘clickjacking’ and uses an overlay to display a blocking message.
Some High-risk Ransomware
CryptoLocker Ransomware Attack: First reported in 2013, September, Cryptolocker is the harbinger of the modern age of ransomware. It infected up to 500,000 machines at its height.
WannaCry Ransomware Attack: Unlike the usual Trojan based Ransomware, this was the first of its kind based on worm architecture - the WannaCry cryptoworm. It propagated through EternalBlue, an exploit (security loophole) on older Windows systems.
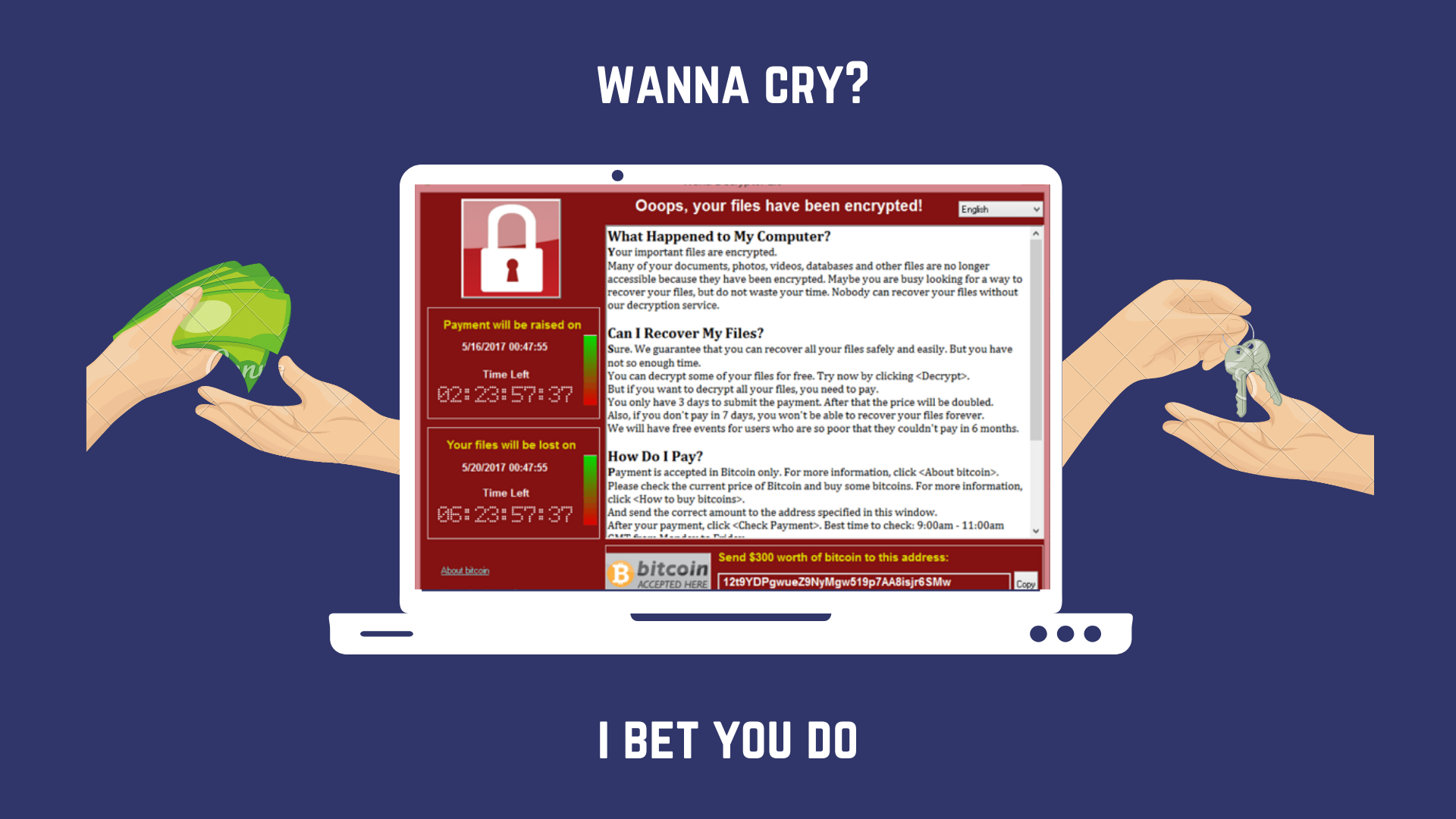
Since Microsoft had immediately released patches to close the exploit, many of WannaCry's victims were people who DON'T UPDATE THEIR SYSTEMS REGULARLY.
WYSIWYE Ransomware Attack: Wysiwye (What you see is what you encrypt) scans the web for open Remote Desktop Protocol (RDP) servers, steals admin credentials and then brute forces its way inside the network, making it exceptionally good for targeted attacks.
GandCrab Ransomware Attack: GandCrab, the terror of 2018, is the most lucrative ransomware ever, to a hacker. Sold as RaaS (Ransomware as a Service), GrandCrab based malware have claimed more than $2 billion in victim payouts. The infamous Sodinokibi is one such GrandCrab based strain.
Thanos Ransomware Attack: Thanos is the most disruptive ransomware detected thus far. It leverages the RIPlace technique to bypass most anti-ransomware systems. Thanks to a highly developed UI, customizing Thanos is a matter of minutes for anybody.
How to remove Ransomware from your system?
Removing Ransomware is not difficult, just like any other malware it can be removed from your system by an antivirus.
Hit Win+R and type in “msconfig”.
In the System Configuration box that opens up, go to the second tab (boot) and click on the radio button next to “safe boot”.
Install an antivirus if you don't have one and run a full system scan. (A boot scan may be required, the antivirus will inform you.)
Allow the scan to complete and “quarantine” the malware files that are found (don't delete them).
Does it help? Hell NAH! XD Your Data is Still Encrypted!
And had I not told you to quarantine the ransomware instead of deleting it, you would have lost your chances of paying the ransom and getting your files back as well. Go back to your quarantine and restore and allow it- the damage has already been done.
Ransomware Prevention - The key lies in blocking it!
On a more reassuring note, if you follow the cybersecurity best practices in general, you have an upper hand already! Ransomware is ultimately a malware and can be blocked by both endpoint and network security solutions.

The essence of dealing with Ransomware lies in BLOCKING IT AT THE ENTRY POINT - either when it is entering your machine (by antivirus) or when it is entering your network (by firewall).
Stopping it before it gets inside your network is always the better bet as you can save everything inside and hence we recommend availing a comprehensive cybersecurity solution like a high-end firewall or BhaiFi to guarantee the peace of mind you are looking for.
If however, you intend to continue without that, here are some tips that can help.
- Keep your operating systems patched and up-to-date to ensure you leave fewer vulnerabilities for the hacker to exploit.
- For Windows, set ‘Core Isolation’ to active in Defender. This feature isolates the core files of your system, making it difficult for ransomware to take footing.
- Use Folder/Directory locking software.
- Don't give administrative privileges to unverified software unless extremely sure of its functionality and authenticity.
- Make sure your IT team is extra careful with remote access.
- Install antivirus software - even a free version - it can still detect malware and actively block them. Browser extensions of these antiviruses are also very helpful.
- Go for Whitelisting software - Only the trusted applications would be allowed to ply on your network and devices, increasing security.
- And, of course, make a habit of taking regular backups of your data. It won't stop an attack, but it can make the damage caused by one seem much less significant.
And most importantly- stay vigilant. Cybersecurity is always a human problem.
Conclusively Enough
Ransomware attackers know their trade well. They keep prices relatively low - an amount companies can usually afford to pay on short notice. Additionally, what looks like ransomware may not have actually encrypted your data at all!
Before making the ransom payment, make sure you aren't dealing with a "scareware popup”. See if it is possible to minimize the extortion message screen and access files.
Hope this was able to help. Do let us know in the comments if there is something we missed out and don't forget to sign up for our newsletter for fortnightly updates.
Cheers and Happy Reading!

Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).