It's a bright sunny day at the beach when you are done with roasting some peanuts and the wind picks up. What a sign, it is going to be a great time to surf, you think as you head towards your surfboard to wreck some waves.

But take care when you are out at the sea, lest you may hit the “black rock”.

Such a large chunk of the rock should be easy to spot and avoid. Right?
Of course, unless the rock can hide itself.
And disguise itself.
And appear all of a sudden from anywhere.
What? What? What?
And unless the ocean isn’t a real ocean but a digital one.
Well, so what we are talking about is the black rock malware that can bring your internet surfing experience to a costly and disruptive end. And if you are not convinced enough, I’ll tell you it might compromise your capability to surf the real ocean too.
Yes, you can't afford a surfing vacation when you are bankrupt.
What is the fuss all about?
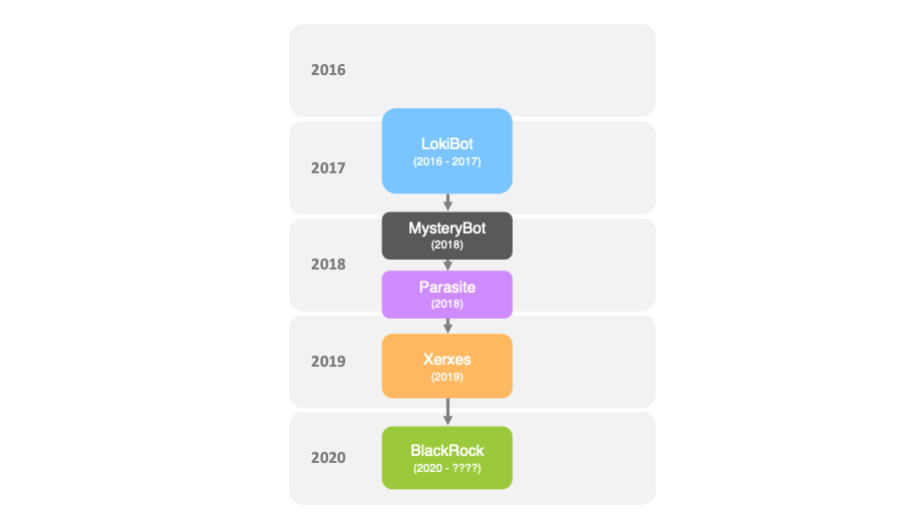
BlackRock is a malware that was discovered earlier this year by analysts at ThreatFabric- an online security firm. While the malware itself is new, it is based upon the strain of the good old Xerxes whose source code was leaked last year. On the surface, BlackRock is quite similar to most other Android Banking Trojans around, but below the surface, there is so much more than what meets the eye.
What Does Not Meet the Eye?
To begin with, BlackRock, unlike its predecessors, can target a much larger set of Apps, 377 precisely. The recon and obscurity functionalities it leverages have been enhanced further and certain unrequired premises of Xerxes have been removed (although Xerxes is older, it still offers more functionalities). This makes BlackRock faster, lighter, meaner, and more agile in comparison. It is the first recorded banking Trojan and first from the LokiBot family of strains that can attack "non-financial apps" as well. These can range from social media to streaming to shopping apps.
As of now, attacks have been reported against- WhatsApp, Facebook, Tinder, Gmail, YouTube, Yahoo Mail, Amazon Prime, Netflix, Amazon Shopping, Skype, Twitter, Snapchat, Instagram, Hoop and Tumblr among others. Credential theft appears to be a plausible reason for the targeting of these apps. Additionally, BlackRock can also execute commands from a remote attacker.
BlackRock is predisposed towards attacking Apps that facilitate financial transactions. These include-
- Banking Apps like HSBC Mobile Banking, Citibank Quickfin, PiBank, OpenBank, Bank of America Mobile Banking, ABN AMRO Mobiel Bankieren.
- Cryptocurrency Apps like Bitfinex, BitPay, Coinbase, Bitcoin Wallet - Airbitz, etc.
- Finance/Money Transfer/Digi Wallet Apps like GPay, Paytm, BHIM, Amazon Pay, PayPal, and Azimo among others.
- Apps like Ola, Uber, Zomato, Swiggy that are not financial in nature but facilitate wallet based quick in-app payments have come under attack too.
Another functionality targeted by BlackRock is the Android Messages (SMS), allowing for the malware to intercept/send/receive messages and read your inbox. Furthermore, BlackRock can Generate Bogus Notifications whenever it needs any new access.
Lastly, BlackRock comes equipped with a “keylogger” - a tool that can record your keystrokes (whatever you enter, including passwords) and recreate them on another similar keyboard, thus recording everything you have typed on your smartphone!
The list of affected apps is long and growing at this time. New items are being added as and when there are targeted. You can have a look at the comprehensive list here.
So How does it Work?
Unlike most other trojans, BlackRock is not a standalone software- it needs another app to get downloaded into your system. Once you have successfully installed that malicious app, it will ask you for permission to access the Android Accessibility Settings. For those of us not familiar with the term, Android Accessibility is a powerful feature of the Android OS that serves as a primary guardian (first line of defense) against any malicious attempt. It allows the App manufacturers to control and carry out the required automation across their fleet of devices, to allow for a more “eased” and "hands-free" access to their users.
“In other words, this feature can perform taps on your behalf.”
In most of the cases, you need to allow certain permissions to apps for them to function properly.
Once you have provided the required accesses, BlackRock contaminates and overwhelms the Android DPC (Device Policy Controller), also known as Android Works Profile to grant itself Admin Permissions of your device, which allows for even greater control over your device’s automation.
Once that happens, you are doomed . . . . .
And, doomed you are indeed. The BlackRock having gained access to your system, uses what we call “overlays” to target your financial transactions. In an overlay attack, the trojan knows when you are going to conduct an account transaction and waits for the time when you make the payment. As soon as you have tapped “pay”, you are redirected to the "overlay interface", instead of the genuine payments gateway interface and your financial transactional credentials are recorded as you enter them. They are with the hackers now. You receive your OTP, everything goes as planned, unless after some time has passed, you realize that Amazon has not yet sent you the online receipt of your order. When you go to your orders screen, to your horror, you never placed the order yet your account has been charged. Oops!
Should you be concerned?
Ask me, there is not one but there are multiple reasons why you should be all the more concerned, for starters:
- I'm sure you noticed, BlackRock can access your SMS functionality. This means it can forward the messages you have received, to the attackers. These may include messages from your bank.
- And since it can remotely execute commands from the attacker, BlackRock can be used to carry out SMS floods and SPAM attacks. Although the browser has not been breached by BlackRock as of yet, once that happens, your phone can be used by the same remote attacker to carry out DDOS attacks as well.
- BlackRock can start and stop apps, causing them to behave as it wants. It is capable enough to shut down your antivirus or any other security mechanism you have in place, thus eliminating any chance of detection.
- That means it can also disable device app management functionality and cleaning apps as well, securing its ground. As a bonus, it can also hide its icon from the App Drawer, once it is installed, so you really don't know what is causing the problem.
- Apart from the financial implications, it can compromise your social media presence by stealing your credentials and there have been instances in the past where situations have escalated beyond control within no time. Take the recent Twitter bitcoin scam for instance.
- The data collected from your profiles can be sold by the hackers at black markets, hence the malware maintains profitability for the hacker/cybercriminal even if you don't use your cellphone for online transactions.
- BlackRock is just the beginning. Even we don't know what else a twisted mind might turn it into. The strain can always be enhanced with more features, updates, and tweaks just like your usual software.
- In the past, BankBot, a similar malware was quickly succeeded by its variants - CometBot, Razdel, and Anubis, each specialized to carry out a specific attack.
How can you fend against it?
Well, as of now no antivirus program is equipped enough to deal with this strain, but it can be prevented from entering your network by a hardware or cloud based or recently updated software firewall. Talking of your device, the best you can do is prevent its entry. It will be downloaded as a malicious app like the ones commonly available on 3rd party platforms other than Google Play. Refrain from visiting and entertaining them.
The most commonly deployed luring mechanism by BlackRock involves leveraging the Google Update Notifications. The malware is capable of displaying fake update notifications to prompt you to provide it with the initial level of access.
Since the malware has already breached the Play Store, what you need to remember is that Google Updates do not explicitly need any new permissions since they have them since the day you first held your device in your hand. If someday they do, then it will surely be as an epilogue to a major OS/Firmware/UI update.
Now that the virus strain has been discovered and analyzed, Google has already initiated updates to its systems to root it out and block it. Several Financial Apps have initiated security reforms and enhancements to eliminate vulnerabilities. MVC/Redirection encryptions and script killers, for instance, can prevent overlays from popping up.
Bottom Line
Summing all that up, to deal with a threat, the first and foremost thing we need is situational awareness. You cant deal with a threat if you don't know about it in the first place. Now it's up to you to spread it even further so more and more people know about it. The second thing we need is to stay alert and strike a balance between our desires and greed which can easily be taken advantage of. Every malady has a cure, all we need to do is hold out until we are reinforced.
We at BhaiFi already have mechanisms in place to deal with such threats and we are sure others will follow suite soon. It is hoped the article helps keep you and your loved ones safe from this malware. Cheers and Happy Reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).