What is common between a business, a bird’s nest and a whole civilization? The answer is, it takes years worth of time, labour and effort to build them up while it takes just one single disaster to bring them down.

One such disaster is that of a Cyberattack. If at this point in time you are amongst the lucky 57% of small businesses that have not faced a cyberattack to date, congratulations, you can take measures now.
38% of businesses amongst the unlucky 43% would tell you how not investing in cybersecurity led them towards a cumulative loss upwards of $3.92 million.
And then, not every loss can be calculated. There are some things we earn at a slower rate than wealth- things like -
Reputation: Holy grail for every startup that gets shattered by one single data breach which is easier for a hacker to pull, than we think.
Credibility: Now imagine if the hacker sells your information online, how do you prove that this was not an insider job? You might end up getting your banking or credit card facilities withdrawn!
Client Goodwill: Loss of a loyal clientele is anyway more crippling than the actual data loss.
Peace of Mind: After the attack takes place, you would spend ANY amount to deal with the situation.
“Less than a hundredth of the investment at the right time could have saved the day!”
Self Esteem: Commonest attacks - Ransomware delivered via Phishing Mails attack your mind rather than your network - encrypting your data with a 2048 bit encryption key, decrypting which is going to take trillions of years on a standard 8GB RAM system!
Tensed already? Don’t be. Now that you are here, your journey towards a secure, stable and high performing workspace internet has already begun.
Small business cyber attack examples
Premises first- we are only looking at the attacks against SMEs and the attacks which are common (P(Attack Type=X) > 0.62). We need to keep to the premises because
- Attacks can be overlapped
- Hackers are innovating fast.
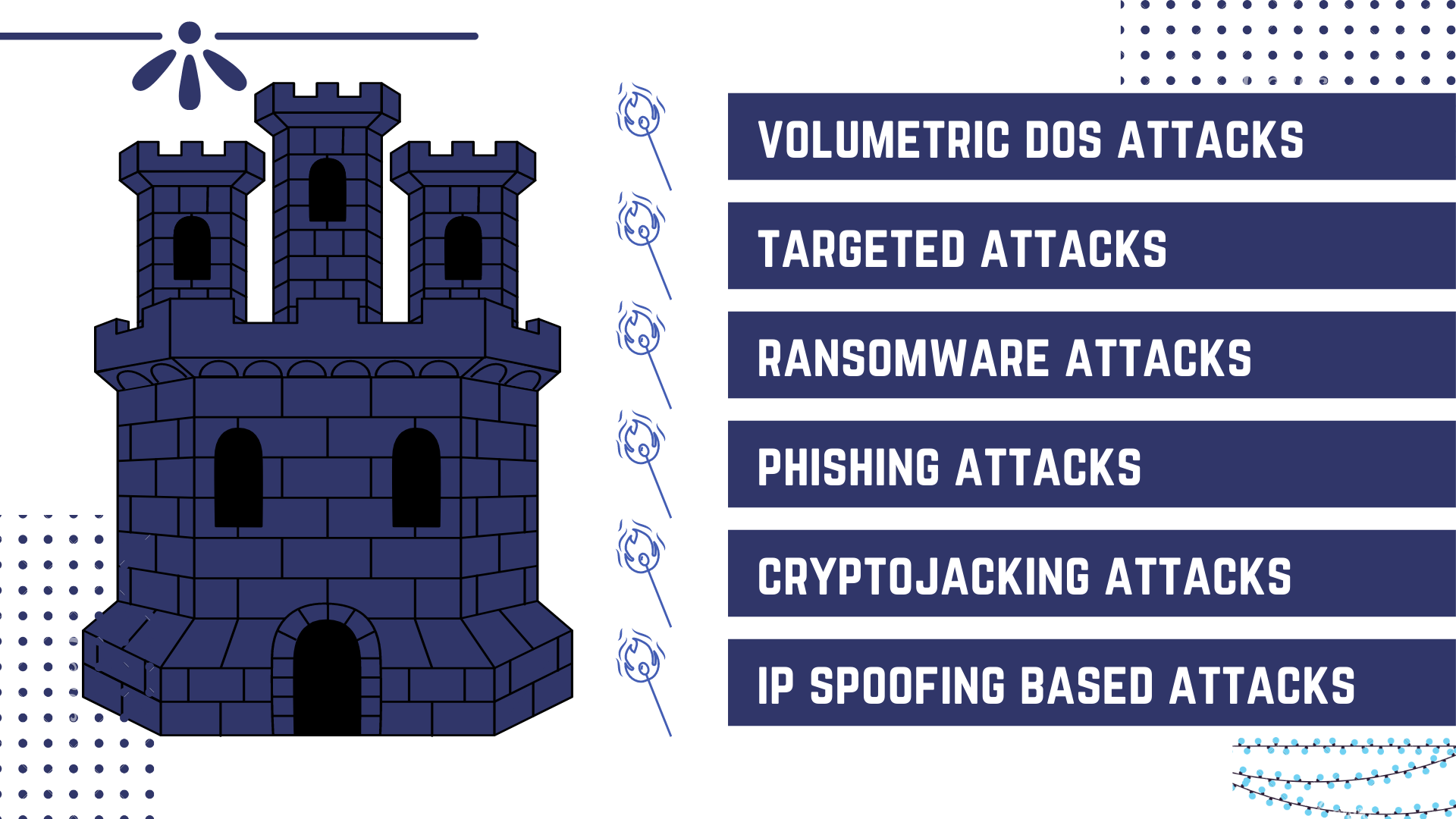
DDoS Attack: Distributed Denial of Service attack aims to flood your network with bogus traffic to overwhelm your servers. Sometimes you might not even realize because of the low volume of attack since in that case, it is usually a Hacker trying to "probe" your network infrastructure for vulnerabilities.
DNS Amplification Attack: A type of DDoS Attack that leverages the Domain Naming System (DNS) to conduct a MORE POWERFUL DDOS from a relatively weak device. Collectively these types of attacks where the hacker leverages the existing internet infrastructure are commonly known as “Reflection Attacks”.
Malicious Port Scan: Remember the hacker trying to “probe” your network for vulnerabilities? Well, that probing is carried out via Port Scanning. Malicious bots scan for open ports or known devices on IP ranges to create a target list.
Targeted Attack: Takes place when the cybercriminal has been following you around the internet to find out important things about you and is now using the same to launch an attack like SQL Injection (SQLi), Cross-Site Scripting (XSS) or Man in The Middle (MiTM).
Ransomware: As discussed will encrypt your data and ask you for ransom should you ever wish to see it again. Notorious for spreading fast, usually the ransomware is spread around via ...
Phishing Attacks: Mostly carried out via (but not limited to) Emails that carry malicious links and all the convincing content required to get you to click, which in turn invites the malware into your system or network. The link could be directly visible, hidden within attachment, image, text - possibilities are endless!
Crypto Jacking Attack: Embeds an undetectable malware into your system that harnesses your processing power behind your back to mine cryptocurrency for the cybercriminal at the expense of your infrastructure.
IP Spoofing based Attacks: The attacker will impersonate a device or user recognized by your network and then launch attacks against hosts, steal data, spread malware or bypass access controls.
What should cybersecurity for a small & medium business look like?
To secure your network, you need a professional cybersecurity solution, the essence of which lies in its IDS/IPS (Intrusion Detection/Prevention System), primarily tasked with filtering the traffic entering/leaving your network.
If the traffic is healthy, it is allowed to pass, if it is malicious, it is blocked. But ...
How does the IDS or IPS know which one is a healthy packet and which one is not?
It refers to a database known as a threat database.
Now since storing data (or even metadata) of all threats that have ever emerged in this world is impossible given the diversity and ingenuity of cybercriminals, this database store rules formulated based on what we call “indicators of compromise”.
“Right from detection and mitigation to the prevention of future cyberattacks, indicators of compromise are what you should be looking out for!”
Although you still need a network monitoring solution to be able to look for these indicators, timely detection can help IT personnel prevent major impending attacks or breaches and plug security vulnerabilities.
Top Indicators of Compromise
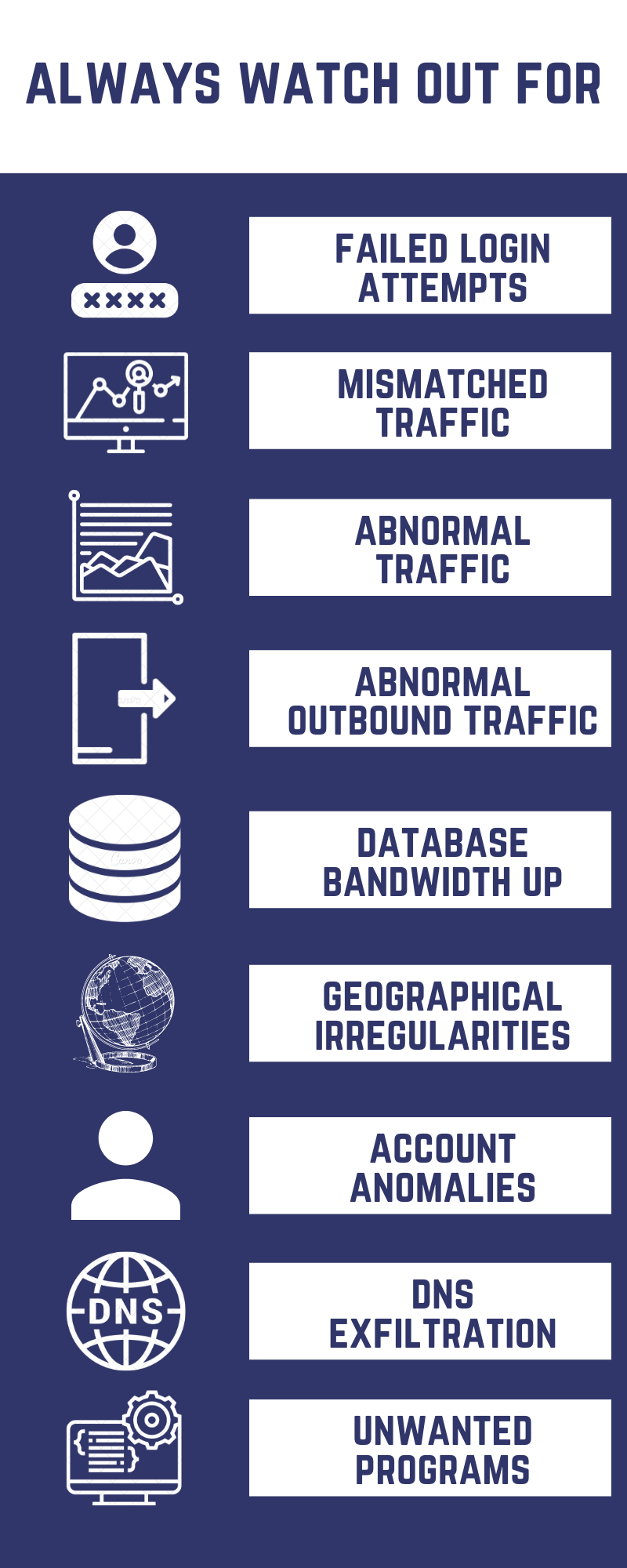
Don’t panic, but be alarmed when your network comes across-
Failed Login Attempts: It is completely human to forget passwords or enter the wrong ones by mistake. However, if you witness continuous repeated failed login attempts or login attempts outside of office hours, it could be a cybercriminal attempting to brute force their way in.
Mismatched Traffic: Always keep your eyes open for the port-application mismatch. Command-and-control (CNC) traffic is important to an attacker because it allows them to manage an ongoing attack and can be spread over port 53, masked as a DNS request or over port 80, masked as an HTTP request. If an application is using an unusual port, it could be CNC traffic masquerading as "normal".
Abnormal Traffic: Computers infected with adware/spyware/malicious trackers generate observable volumes of traffic in short bursts. This should be immediately red-flagged as it doesn’t match with normal human browsing behavior.
DNS Exfiltration: Malicious CNC traffic can also be caught by closely monitoring DNS requests. A spike in requests from a specific host or DNS requests to external hosts with GeoIP anomalies and suspicious reputation data indicates potentially suspicious activity.
Database Bandwidth Spike: If an attacker is trying to extract sensitive information from your database, it generates an enormous amount of read volume, much higher than what you would usually see when the data is being accessed in a more procedural manner.
Inconsistent Outbound Traffic: Monitoring outbound traffic is as important as inbound traffic! Compromised systems will try to communicate with their command-and-control servers, and if you are able to intercept this traffic in real-time, you can move to block it.
Privileged Account Anomaly: Attackers try to gain control of admin accounts or they try to escalate privileges of accounts they've already compromised. Keeping tabs on unusual account behaviour from privileged accounts such as time of activity, systems accessed, type or volume of information accessed can help drastically reduce such attacks.
Geographical Irregularities: Connections, logins and traffic to and from countries your company doesn’t usually do business with should sound the alarm. Same is the case with one account logging in from multiple geo-locations within a short period of time. Keeping custom tunnel settings for VPN can help distinguish employees in this case.
Unwanted Programs, Patches and Files: Software that gets installed on your systems (usually as a patch or update) abruptly is a cause for concern. Abruptly means at a time when a manufacturer like Microsoft or Linux has not notified an update in advance. These ‘patches’ can contain potentially harmful software that can infect your network.
At least in theory, if you take these precautions, you are safe. In reality, there are many more things we need to keep our eyes peeled for and these things move really fast. Registry Anomalies would be a good example here, though it has several iterations and keeping track isn't always easy.
Parting Words and Takeaways
The role of cybersecurity for your organization is as critical as that of any other department and if implemented properly, can guarantee sustained productivity, high returns and seamless peace of mind.
It is always better to invest in a professional cybersecurity solution given the wide variety of attacks and the sheer number of indicators of compromise.
Don’t wait for something to happen, as there is a 50% chance it won't be to your liking. ;-) Simple math!
Cheers and Happy Reading!


Comments
Become a BhaiFi® | Blog & Stories member below to join the conversation (it's free!). As a member, you will also receive new posts by email (you can unsubscribe at any time).